Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Pass-The-Salt 2021 Virtual Wrap-Up
published on 2021-07-07 15:54:00 UTC by XavierContent:
I did not write any wrap-up for a while because we are all stuck at home and most conference organizers still decided to cancel live events (even if it seems to change by the end of 2021 where some nice events are already scheduled). For the second time, Pass-The-Salt was converted to a virtual event. I like this small event with a great atmosphere. This edition in a few numbers: they received 27 proposals and selected 16 amongst them. They were presented spread across three half-days. Let’s review what was presented.
The first day started with Eloi Benoist-Vanderbeken who talked about jailbreak detection mechanisms in iOS and how to bypass them. iOS is a closed operating system and Apple really takes this seriously. Indeed, when a device has been “jailbroken”, all security measures are bypassed and the user gains full control of the device. Some apps really take this as a major problem and try to detect this. Think about banking applications but also games. To detect how the jailbreak detection is implemented, it’s mandatory to reverse the app to read the code. Also, Apple restricts a lot of operations: only signed code can be executed, side loading is not allowed (you remember the Epic Game problem?) and apps may only use public API’s. One of the best tools to help is debugging an app is Frida. How to debug an iOS app? Without a jailbreak in place, Frida is injected using ptrace but the app must be repackaged, with a lot of side effects. With a jailbreak already in place, Frida can just attach to the process. As a case study, a banking app was taken as an example. When the app is launched on a jailbroken device, it just crashes. A first set of checks did not reveal anything special. Check deeper, the app tried to trigger an invalid entry error. Some Frida usage examples were reviewed, based on hooks. Frida can hook syscalls to get information about the parameters and/or return values or completely replace the syscall with another function. It can also execute a function before any syscall. This is very interesting to follow what’s happening (example: to keep an eye on decrypted data). Another technique is the classic usage of breakpoints. Some techniques to detect jailbreaks: access specific files with open(), utime(), stats(), …), try to detect the presence of a debugger, check the parent PID, is the root filesystem writable?
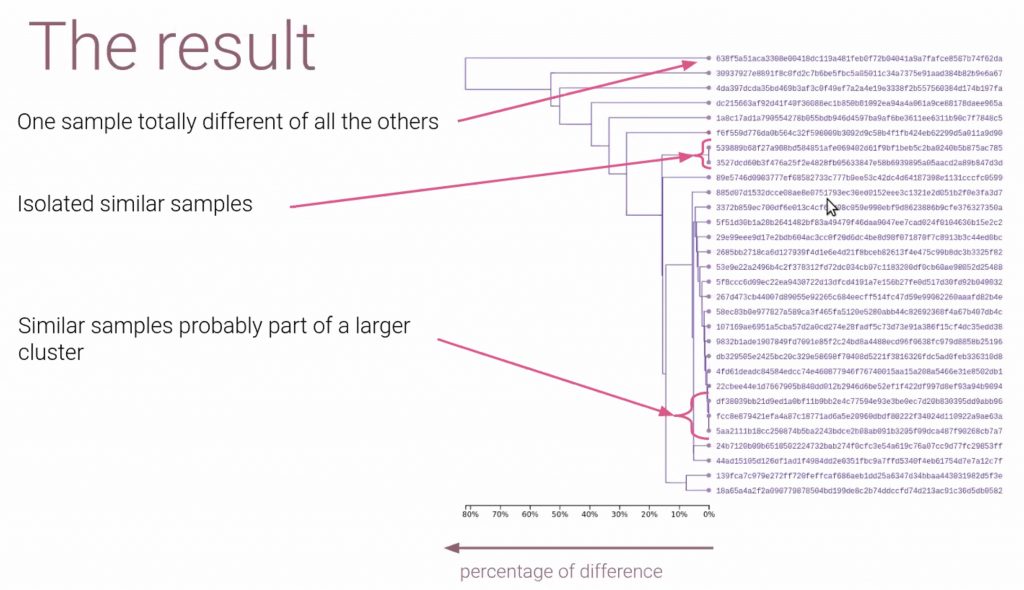
The second presentation was the one of Esther Onfroy. She’s an Android expert, hacktivist and speaker. The title of Esther’s presentation was “Pithus: let’s open the Android pandora’s box”. Pithus is a project that focus on analyzing Android applications (APK). Why a new project? According to Esther, threat intelligence should not be the proprietary of a private company. For some, the price is a subscription is crazy high so the idea to develop an open-source tool based on free software and self-hostable. Pithus is able to check domains, certificates, the application time line, behavioral analysis and is linked to 3rd party services like MalwareBazaar. A specific function was presented deeper: The CFG (“Control Flow Graph”) dissection using AndroGuard. This is an interesting feature to search for share code:
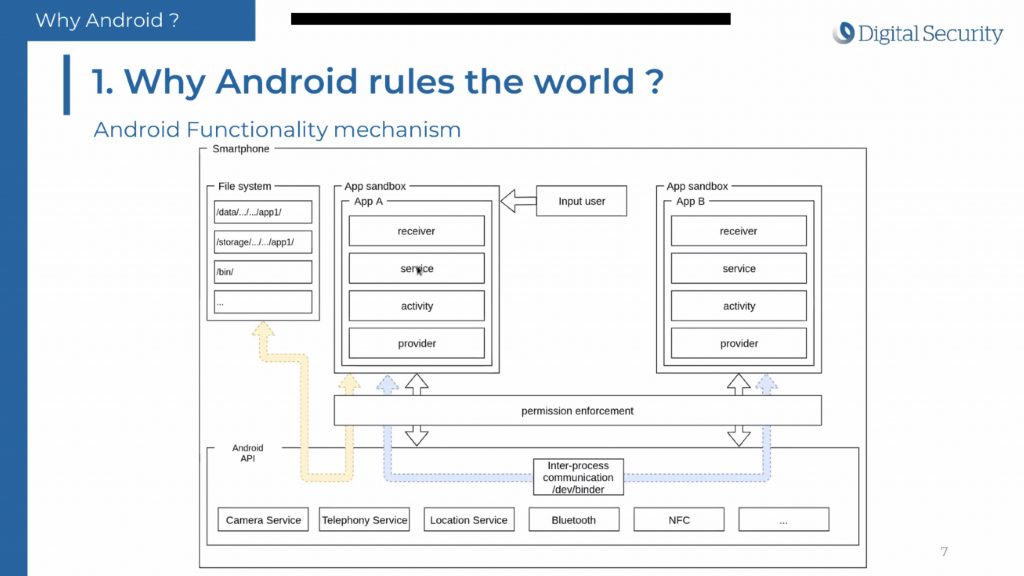
Benoit Forgette presented “Hook as you want it“. Android is very popular in the mobile landscape. It provides a standard bootloader, an API for hardware, an ARM trustzone, High-level language (easy to write apps) and IPC. Review of the Android permission enforcement mechanism. AST is a tree and a hook is a programming trick that helps to intercept system calls. Once again here Frida will be used.
The next talk was “PatrowlHears and Survival tips for prioritizing threats” by Nicolas Mattiocco. It starts with a quick overview of Patrowl with themotto “demotivate attackers”. In vulnerability management, process is key: “How to manage vulnerabilities?”. It’s not only running a tool at regular interval:
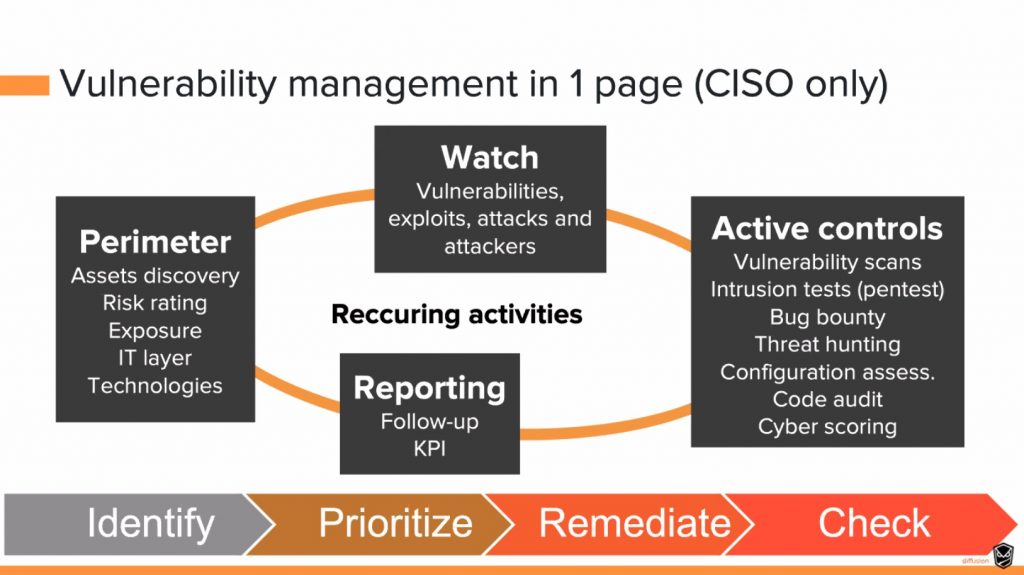
One of the problems is the changing landscape, a lack of skilled people, budget pressure, … Automation is also a key point. And when running the tool more often, you get more findings and more alerts How to improve this? Then Nicolas explained how to prioritise findings. Some ideas: check the CVSS score, are we vulnerable? Is it exposed to the Internet? Is it a critical asset? Functional exploit? Patch or work around? etc… Most important: does it have a nice logo?  To help in this process, PatrolHears was introduced. It provides scalable, free and open-source solutions for orchestrating Security Operations and providing Threat Intelligence feeds. PatrowlHears is an advanced and real-time Vulnerability Intelligence platform, including CVE, exploits and threats news. Its also a feed aggregator (Packetstorm, Tenable Nessus DB, Metasploit, Exploitdb, ZDI, … Great tool to check if you’re dealing with vulnerability management.
To help in this process, PatrolHears was introduced. It provides scalable, free and open-source solutions for orchestrating Security Operations and providing Threat Intelligence feeds. PatrowlHears is an advanced and real-time Vulnerability Intelligence platform, including CVE, exploits and threats news. Its also a feed aggregator (Packetstorm, Tenable Nessus DB, Metasploit, Exploitdb, ZDI, … Great tool to check if you’re dealing with vulnerability management.
To wrap-up the first day, we had a pretty funny presentation by Michael Hamm from circl.lu. The Luxembourg CERT produces always nice content and it was, once again, the case. Michael presented three live demos (yes, live) of USB devices alterations from a forensic point of view. The first one was about changing the content of a USB disk mounted in “read-only” mode. Yes, it’s possible. That’s why using a physical write-blocker is always highly recommended. The second one, was a kind of DoS attack: By modifying only a few bytes on the filesystem, a Linux system will, once the modified disk is inserted, mount it up to 250 times  Finally, the last demo was even more impressive: by altering the MDR (Master Boot Record) and creating a “Polyglot boot sector”, Michael demonstrated how different files can be seen by different operating systems. Mounting the drive on Linux, some files will be listed, on Windows, other files will be listed.
Finally, the last demo was even more impressive: by altering the MDR (Master Boot Record) and creating a “Polyglot boot sector”, Michael demonstrated how different files can be seen by different operating systems. Mounting the drive on Linux, some files will be listed, on Windows, other files will be listed.
Day two started with “Fedora CoreOS, a container focused OS to securely deploy and run applications” by Timothée Ravier. Intro to CoreOS: automatic updates, automatic provisioning (Ignition is used to provision nodes on 1st boot), immutable infrastructure and finally huge use of containers. What about security? “Softwares have bugs” so reduce the OS footprint (-> reduce the attack surface). Next, use safer languages: Go & Rust (memory safe languages). They use rpm-ostree to update the system (think about a “git for operating system”. Uses read-only filesystems and a clear split across important directories (/usr, /etc, /var). Everything runs in containers (podman, docker). Confinement with SELinux. Demos! The first one was to run a Matrix server More about CoreOS here.
The second talk was provided by Clément Oudot, a regular PTS speaker: “Hosting Identity in the Cloud with free softwares“. After a nice live song, Clément did a quick introduction/recap about IAM (“Identity and Access Management”) and a review of the market: big players are expensive – pay per user – and complex to install/manage.
So what about FOSS? A lot of tools exist but don’t cover the complete set of IAM features. FusionIAM is a project to propose a unified platform based on different tools: OpenLDAP, LDAP ToolBox, Fusion Directory, LDAP Synchronization Connector, and LemonLDAP:NG. From a features point of view, it provides whites pages, access manager, sync connector, service desk, directory server, directory manager. A great solution to investigate if you need to deploy IAM in a cloud environment.
The next presentation was “Biscuit: pubkey signed token with offline attenuation and Datalog authz policies” by Geoffroy Couprie. Geoffroy works for a hosting company and is often facing authentication issues (example for API’s). A classic way to authenticate users is a JWT (JSON Web Token). They are usually signed using a public key and contain a lot of data. They are not perfect therefore Geoffroy developed a new authentication and authorization token called Biscuit. You can find more information about this project here (code) and here.
Ange Albertini presented “Generating Weird Files“. Ange is known to play a lot with file formats. He already presented several pieces of research where he demonstrated how files can be built in a way that, depending on the program used to open them, they will present different types of content. Today, Ange presented his tool called Mitra. The open-source tool takes 2 files, checks their types, and generates possible polyglots.
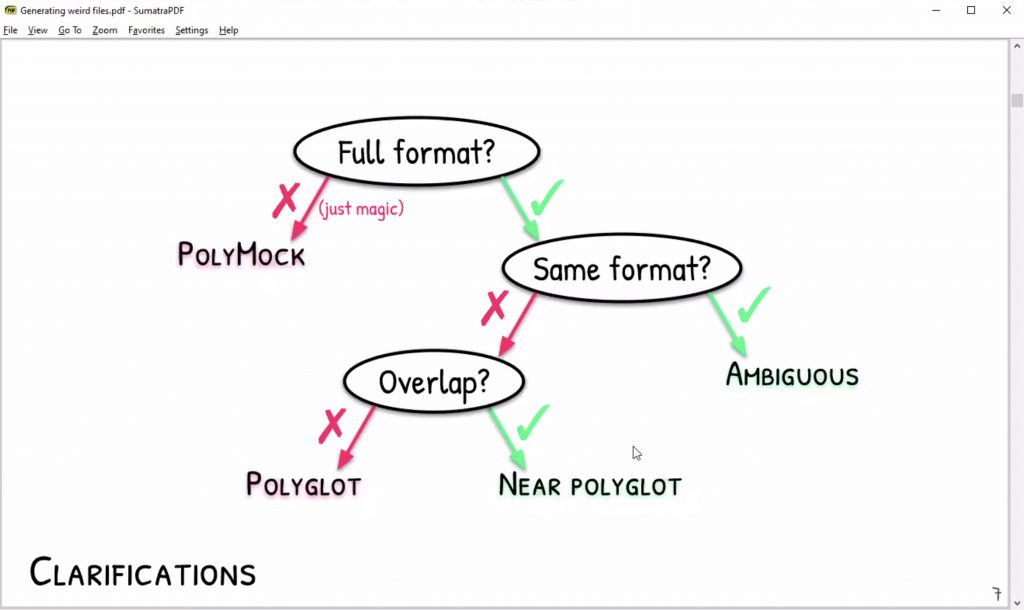
What are the strategies used by Mitra?
- Concatenation: easy because some file format do not need to start at offset 0
- Cavities (filling empty spaces)
- Parasite (abusing comments in metadata)
- Zipper
Ange performed some demos. It was funny to see a reference to 1 file that identified up to 190 different file formats! The conclusion to this? These techniques could be prevented by creating new file formats that starts at offset 0 (magic bytes).
The next time slot was assigned to … me! I presented “Home-Made Distributed Blocklist“. More to come soon on this blog!
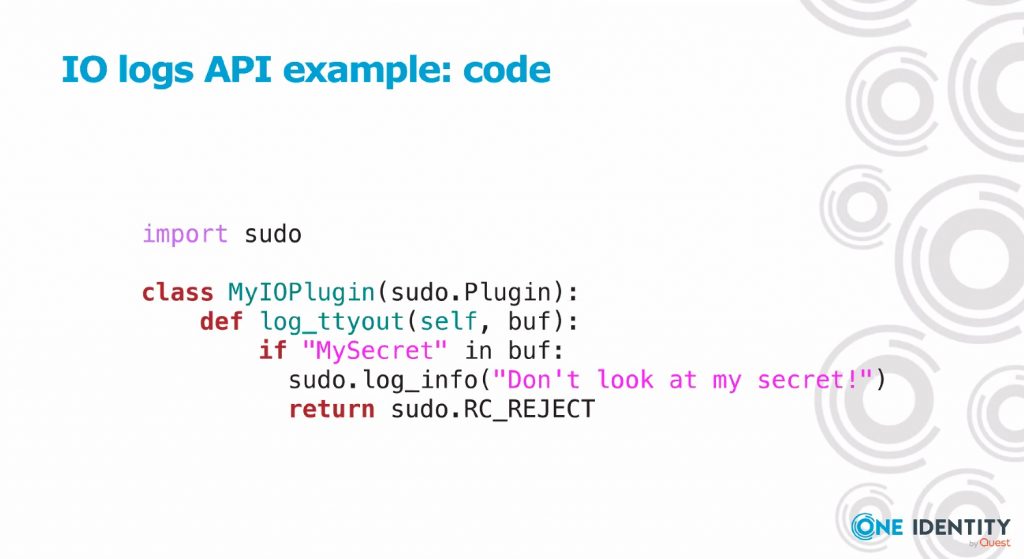
We wrapped the afternoon with a very interesting talk by Peter Czanik: “Security alerting made easy using Python“. Peter is a also a regular contributor to the conference and is leading open source products like syslog-ng or Sudo. Even if I’m an old Sudo user (probably for more than 15 years), I’m always learning new stuff about this wonderful tool and it was again the case. Peter explained how to interconnect Sudo and Python. Sudo is a modular tool that accepts plugins in C but also in Python to extend features and controls. You can filter data, alert, sanitize them etc… Peter reviewed some examples of integration.
Day 3 started with some Kunernetes security stuff: “ATT&CKing Kubernetes: A technical deep dive into the new ATT&CK for Containers” by Magno Login. Magno is the maintainer of the following github project: awesome-k8s-security. Then, he talked about the MITRE ATT&CK and more precisely, the matrix dedicated to containers (link). This matrix was created for a while but was updated recently with plenty of new content (thanks to the contribution of volunteers)
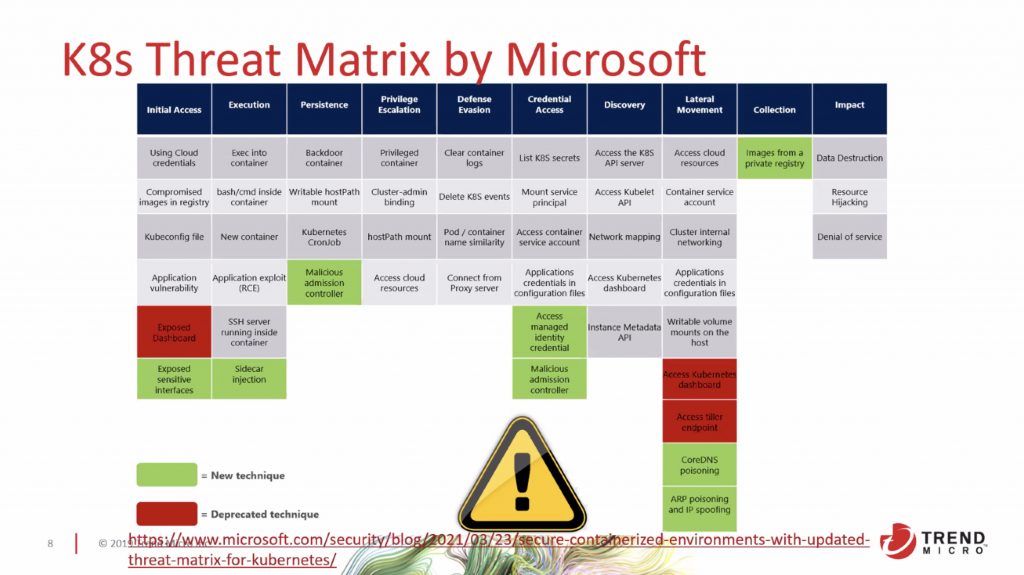
The second part of the talk was a suite of attacks scenarios based on a vulnerable Drupal CMS instance. Magno presented many techniques from the MITRE matrix. Scripts described in demos were collected from honeypots or found on C2 servers.
Then we switched to the wonderful world of shellcodes with Yashdeep Saini and Harpreet Singh who presented “Revisiting the Art of Encoder-Fu for novel shellcode obfuscation techniques“. Back to the roots with a review of the differences between x86, x64 and ARM registers and instructions (comparisons, shifting, control flows, stack, data movement and arithmetic operations.
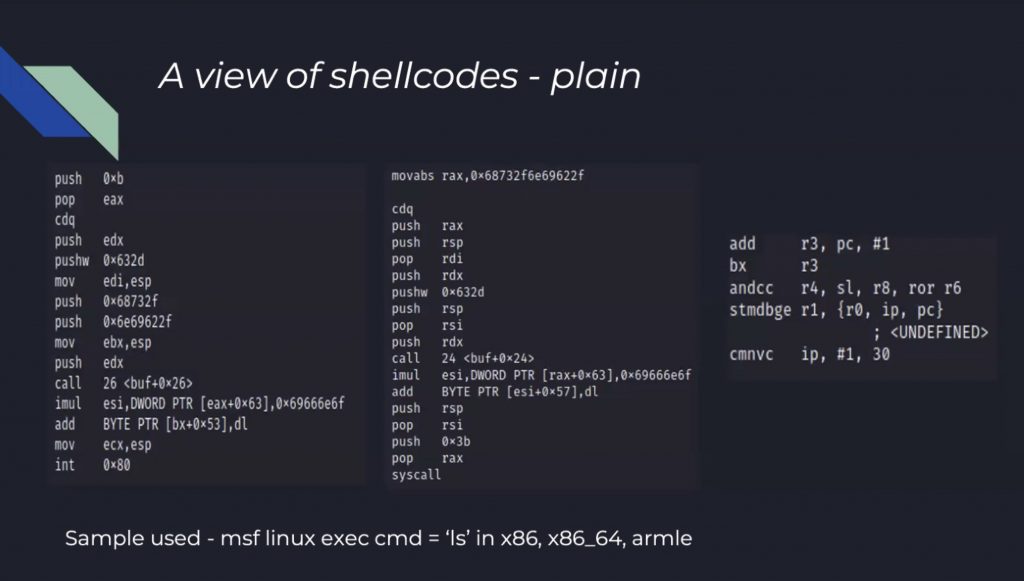
They reviewed how encoders affect the shell code (XOR, Shikata_ga_nai, etc). Another comparison was to show comparative graphs based on the distributions of instructions:
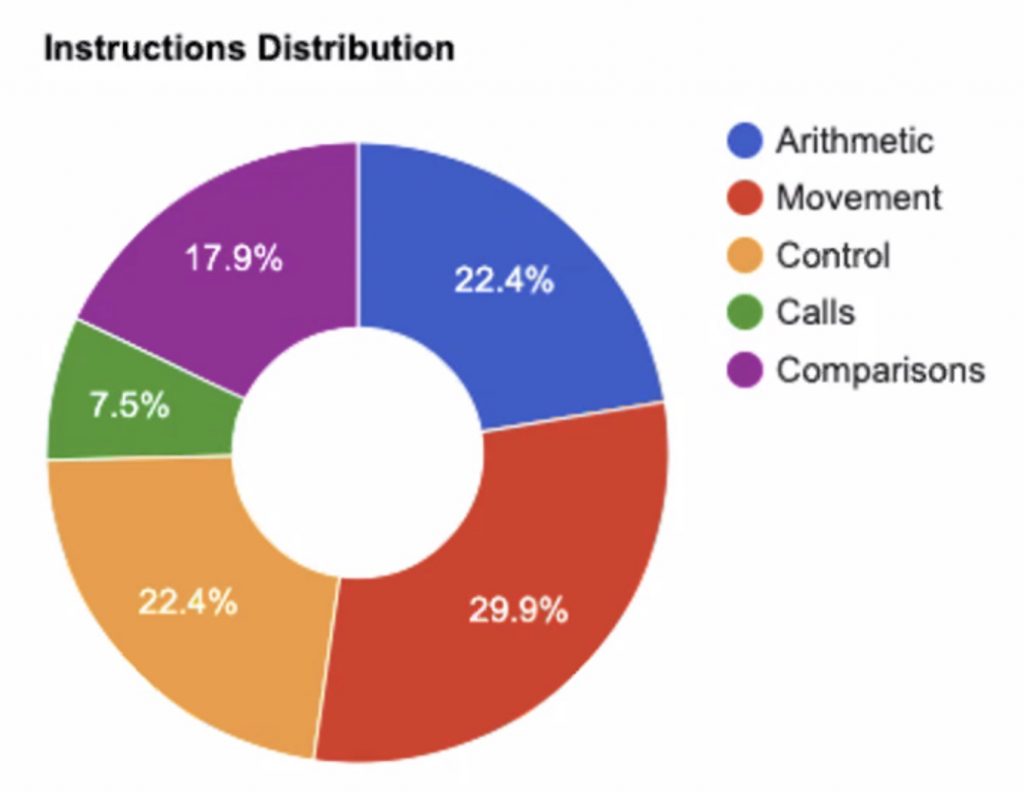
Other observations: encoder types adding laters and branches(mode control, call changes). Other add transformation (more data movements). Why encode? The shell code can be transformed as per transport supported by the target applications. Bad characters can be replaced and more obfuscation.
“In Search of Lost Time: A Review of JavaScript Timers in Browsers” by Thomas Rokicki. Timing attacks exploit timing differences to infer secrets from the sanbox.Attacks can be classified in 4 classes: Harare-contention-base attack (Ex: rawhammer.js), Transcient execution attacks (Spectre), Attacks based on system resources (Keystroke attacks, memory deduplication attacks ) and attacks based on browser resources(History sniffing or fingerprinting). This is a topic that remains always difficult to follow for me… I just kept this in mind as a recap to the talk: “If you are concerned by timing attacks, use the TOR browser, they are the strictest on timers countermesures“
Then Nils Amiet and Tommaso Gagliardoni presented “ORAMFS: Achieving Storage-Agnostic Privacy“. The important word here is “privacy” or how to store data on a 3rd party service in a safe way. The classic control is to encrypt the complete set of data. But even if data can’t be read more info can be leaked: The size of data, some fields of database will change, etc… Think about an employees db. Example with the good old Truecrypt software: Create a TC volume, encrypted then mounted by the user. A cool feature was the “hidden volume” but can be detected even without the passphrase:
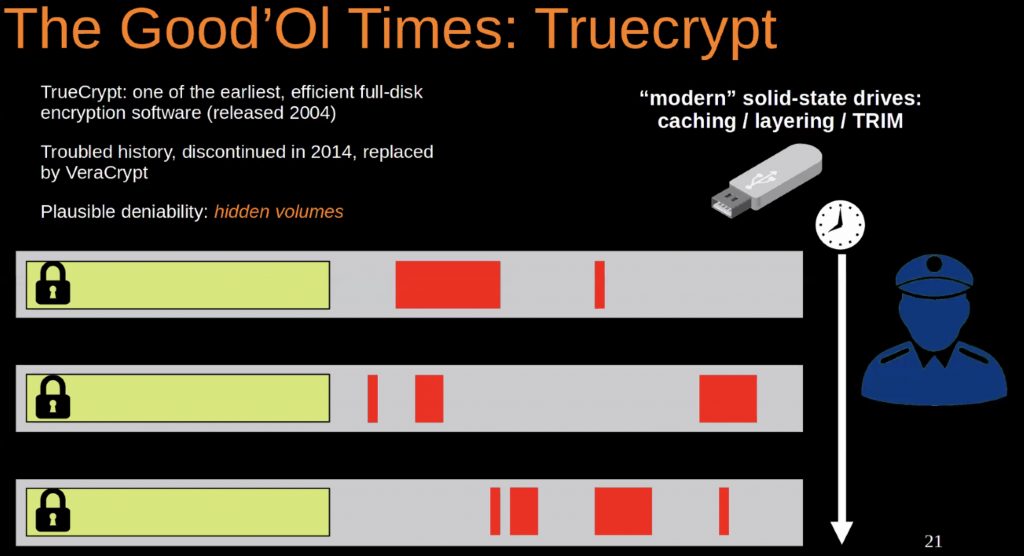
Keep in mind that “Encryption alone does not hide access patterns“. That’s why oramfs (Oblivious Random Access Machines) has been developed. Storage agnostic, written in Rust, resizing supported, multiple encryption cyphers, the tool was demonstrated live. Nice demo!
Finally, to wrap-up day 3, Damien Cauquil presented “Meet Piotr, a firmware emulation tool for trainers and researchers“. Damien performs a lot of IoT trainings and was looking for a nice solution to setup labs. Indeed, even more with the pandemic, it has been challenging to prepare labs. For example, some IoT device might be discontinued or their firmware upgraded to a non-vulnerable version. Another requirement was the size of the lab (to not download gigabytes of data). That’s why Piotr has been developed. It is based on Qemu, Firmadyne and ARM-X. After describing the architecture (how those components are interconnected), Damien performed some demos and booted/exploited some IoT devices. It looks to be a great solution also to researchers. If interested, the code is available here.
And that’s over for this virtual edition of Pass-The-Salt! Let’s hope that the next one will be in-person. Thanks to the organisers for keeping the event up’n’running! All slides are available online as well as videos.
The post Pass-The-Salt 2021 Virtual Wrap-Up appeared first on /dev/random.
https://blog.rootshell.be/2021/07/07/pass-the-salt-2021-virtual-wrap-up/
Published: 2021 07 07 15:54:00
Received: 2021 07 07 16:05:06
Feed: /dev/random
Source: /dev/random
Category: Cyber Security
Topic: Cyber Security
Views: 5
