Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Android Browser Kitkat Content Spoofing Vulnerability
published on 2015-03-12 05:41:00 UTC by RafayContent:
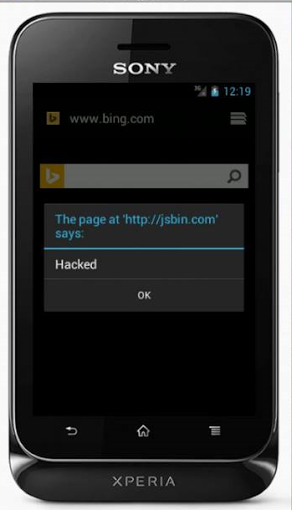
The following is a low risk vulnerability that was found few months ago while testing the latest Android Stock browser on Android Kitkat. The issue that was found is commonly referred as Content spoofing Vulnerability or dialog box spoofing vulnerability which could be used to fake an alert message on a legitimate website.
In other words, i could display an alert box (Of my choice) on the site of my choice. Whereas in chrome, Firefox and other browser the alert box appears on correct tab.
POC
<a onclick="test()">CLICK</a>
<script> function test()
{ window.open('http://bing.com/') setTimeout (function(){alert("HACKED");}, 5000) }
</script>
Upon executing the above code, the alert box would be displayed on bing.com.
Technical Details
The issue resides inside of the ASOP browser, and more specifically due to the fact the webview fails to overwrite the WebChromeClient.onJsAlert() method which is responsible for displaying the javascript alert box and this way webview is not able to switch the JsAlert() to the correct tab.
Future Releases
I have recently reported another medium risk issue present in latest android stock browser, which would be released once the issue is addressed by the Google team.
http://www.rafayhackingarticles.net/2015/03/android-browser-kitkat-content-spoofing.html
Published: 2015 03 12 05:41:00
Received: 2023 04 01 05:22:27
Feed: Ethical Hacking - Rafayhackingarticles
Source: Ethical Hacking - Rafayhackingarticles
Category: Cyber Security
Topic: Cyber Security
Views: 16