Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.FBI Seizes Bot Shop ‘Genesis Market’ Amid Arrests Targeting Operators, Suppliers
published on 2023-04-04 21:04:11 UTC by BrianKrebsContent:
Several domain names tied to Genesis Market, a bustling cybercrime store that sold access to passwords and other data stolen from millions of computers infected with malicious software, were seized by the Federal Bureau of Investigation (FBI) today. Sources tell KrebsOnsecurity the domain seizures coincided with “dozens” of arrests in the United States and abroad targeting those who allegedly operated the service, as well as suppliers who continuously fed Genesis Market with freshly-stolen data.
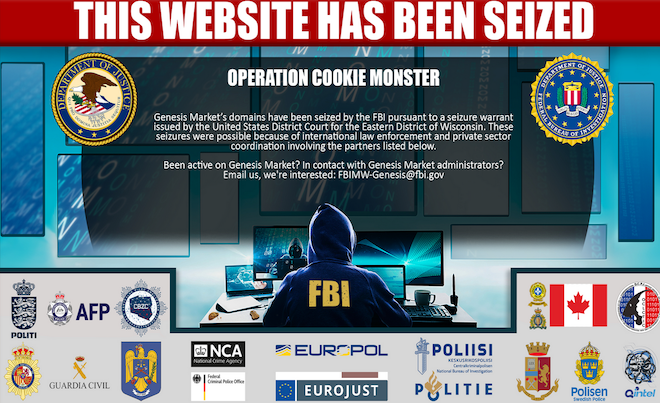
Several websites tied to the cybercrime store Genesis Market had their homepages changed today to this seizure notice.
Active since 2018, Genesis Market’s slogan has long been, “Our store sells bots with logs, cookies, and their real fingerprints.” Customers could search for infected systems with a variety of options, including by Internet address or by specific domain names associated with stolen credentials.
But earlier today, multiple domains associated with Genesis had their homepages replaced with a seizure notice from the FBI, which said the domains were seized pursuant to a warrant issued by the U.S. District Court for the Eastern District of Wisconsin.
The U.S. Attorney’s Office for the Eastern District of Wisconsin did not respond to requests for comment. The FBI declined to comment.
But sources close to the investigation tell KrebsOnSecurity that law enforcement agencies in the United States, Canada and across Europe are currently serving arrest warrants on dozens of individuals thought to support Genesis, either by maintaining the site or selling the service bot logs from infected systems.
The seizure notice includes the seals of law enforcement entities from several countries, including Australia, Canada, Denmark, Germany, the Netherlands, Spain, Sweden and the United Kingdom.
When Genesis customers purchase a bot, they’re purchasing the ability to have all of the victim’s authentication cookies loaded into their browser, so that online accounts belonging to that victim can be accessed without the need of a password, or in some cases even multi-factor authentication.
“You can buy a bot with a real fingerprint, access to e-mail, social networks, bank accounts, payment systems!,” a cybercrime forum ads for Genesis enthused. “You also get all previous digital life (history) of the bot – most services won’t even ask for login and password and identify you as their returning customer. Purchasing a bot kit with the fingerprint, cookies and accesses, you become the unique user of all his or her services and other web-sites. The other use of our kit of real fingerprints is to cover-up the traces of your real internet activity.”
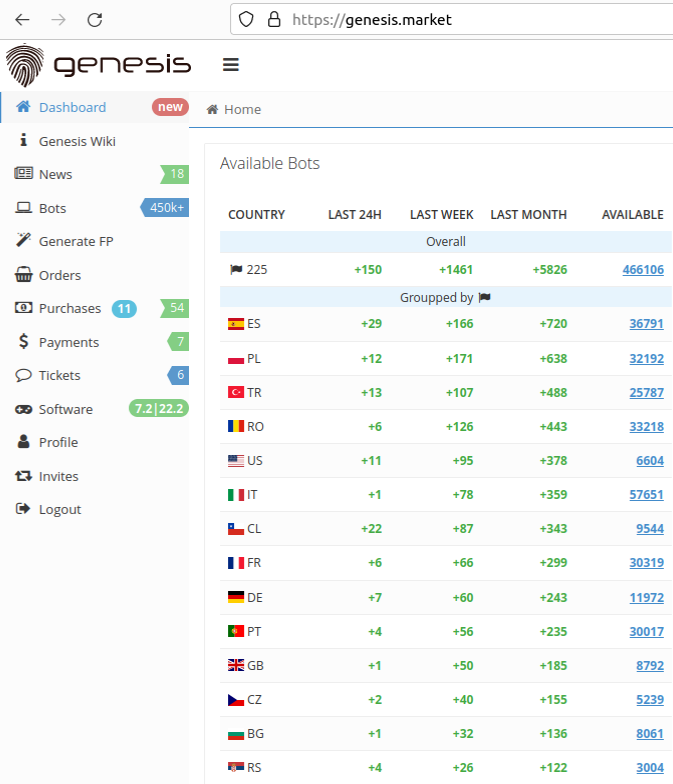
The Genesis Store had more than 450,000 bots for sale as of Mar. 21, 2023. Image: KrebsOnSecurity.
The pricing for Genesis bots ranged quite a bit, but in general bots with large amounts of passwords and authentication cookies — or those with access to specific financial websites such as PayPal and Coinbase — tended to fetch far higher prices.
New York based cyber intelligence firm Flashpoint says that in addition to containing a large number of resources, the most expensive bots overwhelmingly seem to have access to accounts that are easy to monetize.
“The high incidence of Google and Facebook is expected, as they are such widely used platforms,” Flashpoint noted in an analysis of Genesis Market, observing that all ten of the ten most expensive bots at the time included Coinbase credentials.
Genesis Market has introduced a number of cybercriminal innovations over its existence. Probably the best example is Genesis Security, which is a custom Web browser plugin which can load a Genesis bot profile so that the browser mimics virtually every important aspect of the victim’s device, from screen size and refresh rate to the unique user agent string tied to the victim’s web browser.
Flashpoint said the administrators of Genesis Market claim they are a team of specialists with “extensive experience in the field of systems metrics.” They say they developed the Genesis Security software by analyzing the top forty-seven browser fingerprinting and tracking systems, as well as those utilized by 283 different banking and payment systems.
Cybersecurity experts say Genesis and a handful of other bot shops are also popular among cybercriminals who work to identify and purchase bots inside corporate networks, and then turn around and resell that access to ransomware gangs.
Michael Debolt, chief intelligence officer for Intel 471, said so-called “network access brokers” will scour automated bot shops for high value targets, and then resell them for a bigger profit.
“From ‘used’ or ‘processed’ logs — it is actually quite common for the same log to be used by multiple different actors who are all using it for different purposes – for instance, some actors are only interested in crypto wallet or banking credentials so they bypass credentials that network access brokers are interested in,” Debolt said. “These network access brokers buy these ‘used’ logs for very cheap (or sometimes for free) and search for big fish targets from there.”
In June 2021, hackers who broke into and stole a wealth of source code and game data from the computer gaming giant EA told Motherboard they gained access by purchasing a $10 bot from Genesis Market that let them log into a company Slack account.
One feature of Genesis that sets it apart from other bot shops is that customers can retain access to infected systems in real-time, so that if the rightful owner of an infected system creates a new account online, those new credentials will get stolen and displayed in the web-based panel of the Genesis customer who purchased that bot.
“While some infostealers are designed to remove themselves after execution, others create persistent access,” reads a March 2023 report from cybersecurity firm SpyCloud. “That means bad actors have access to the current data for as long as the device remains infected, even if the user changes passwords.
SpyCloud says Genesis even advertises its commitment to keep the stolen data and the compromised systems’ fingerprints up to date.
“According to our research, Genesis Market had more than 430,000 stolen identities for sale as of early last year – and there are many other marketplaces like this one,” the SpyCloud report concludes.
This is a developing story. Any updates will be added with notice and timestamp here.
https://krebsonsecurity.com/2023/04/fbi-seizes-bot-shop-genesis-market-amid-arrests-targeting-operators-suppliers/
Published: 2023 04 04 21:04:11
Received: 2023 04 04 21:20:40
Feed: Krebs on Security
Source: Krebs on Security
Category: Cyber Security
Topic: Cyber Security
Views: 4
