Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Year-long spear-phishing campaign targets global energy industry
published on 2021-07-08 21:50:09 UTC by Derek B. JohnsonContent:

An unknown group has been conducting a year-long spear-phishing campaign against energy companies and other industries around the world.
The campaign has been happening for at least a year and targets companies and employees in the gas and oil, energy, information technology, media and electronics industries around the world, according to new research from Intezer, though many of the affected businesses are located in South Korea. The spear-phish emails leverage both typosquatting and spoofing to make the incoming emails look like they’re coming from established companies. They also reference executives from the company by name and include legitimate business addresses and company logos.
Many of the spear-phishing emails demonstrate how the threat actor appears to have done their homework, filled with procurement language jargon, referencing real ongoing projects the impersonated company is working on and inviting the target to bid for a portion of the work by clicking on an attachment.
That attachment – which is designed to mimic the appearance of a PDF but is usually an IMG, ISO or CAB file — contains information-stealing malware to steal banking data, log keystrokes and collect browsing data. The actors don’t appear to rely on a single type or family of malware, instead using a variety of remote access tools and other malware-as-a-service, like Agent Tesla and Formbook. Like many successful phishing lures, they’re designed to give a financial incentive to the victim to click on the link and create a sense of urgency in responding.
“It seems like part of the incentive was that the receiving component could think that there’s some money coming their way,” said Ryan Robinson, a security researcher at Intezer, in an interview.
In one example, a fake email account pretending to be from Hyundai Engineering Inc. mentions a real power plant project in Panama, is filled with procurement jargon and gives short turnaround deadlines for expressing interest in the project (48 hours from receipt of email) and submitting a bid (March 29). In another, an employee from Netherlands-based offshore drilling company GustoMSC asks the target to sign and return a non-disclosure document and mentions a wind farm in Dunkirk managed by GustoMSC.
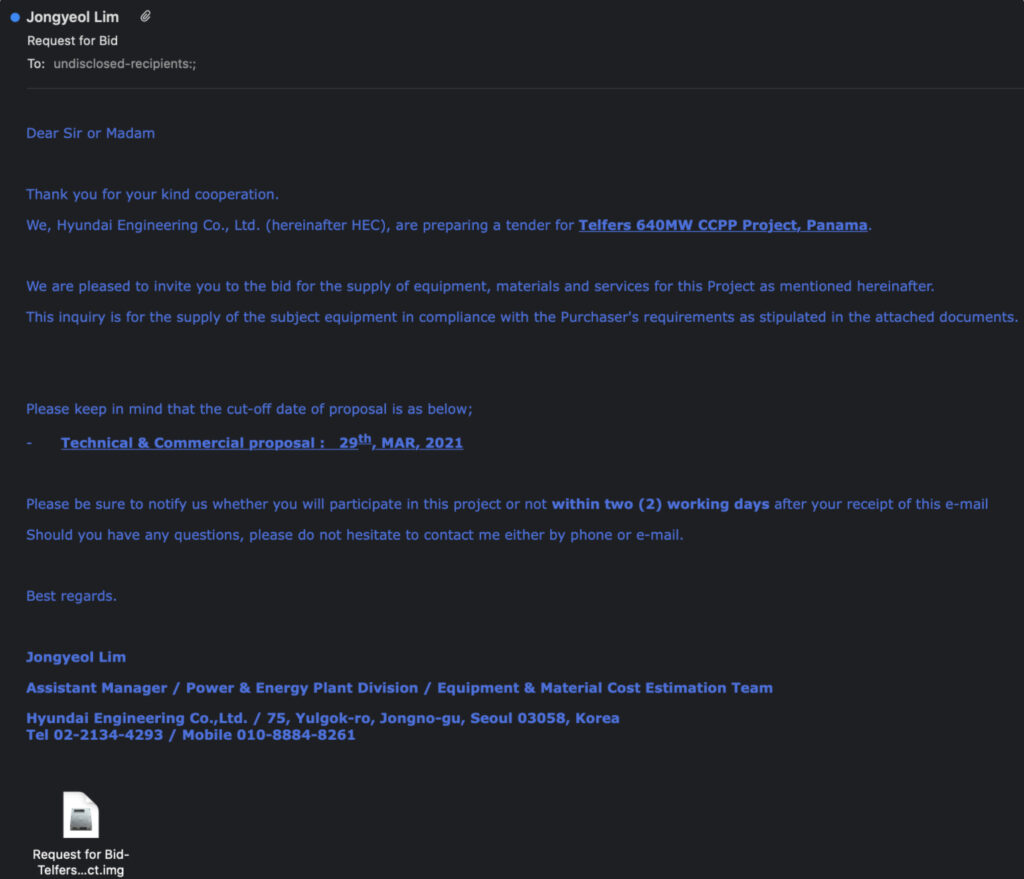
The researchers say most of the companies targeted in the campaign were South Korean, while a number of targets from other countries wound up having some substantial business connection to South Korea. One business that appears to stand out from the rest of the targeted victims is the Korean branch of the Far East Broadcasting Company, an international Christian radio broadcaster. FEBC is known for broadcasting the Gospel and religious programs across borders into countries that outlaw or restrict religious freedom, including North Korea.
Robinson said the emails were mostly in English and are “slightly better than average” in terms of their presentation, tending to lack many of the obvious typos or language errors that give away other campaigns, though they note they could not fully scrutinize some of the emails since they were in Korean and Intezer does not have a native Korean-speaker on staff. Another Intezer researcher, Nicole Fishbein, said there were other indicators that the spearphishers did their homework for each target.
“I think the language of the email, all the terms that are related to the business of oil and gas, and even engineering terms, it looks like the people that are behind it really understand what they’re talking about,” Fishbein said.
Intezer pointedly does not make or attempt any attribution about the actors or group behind the campaign. Fishbein and Robinson said that’s partly due to the lack of a clear or established patterns in the types of malware deployed, as well as their widespread use by other threat actors. Robinson said they had to cross-reference malware-laced images to emails received and opened by the victim on the same day, ultimately collecting data from hundreds of emails that they could conclusively tie to the campaign.
The nature of the malware strains and the type of data stolen indicates that the activity could be the first step in a larger hacking project.
“I would say that because we see the malware delivered is an information stealer and not ransomware, they’re after information, it could be information for the next stage of the campaign,” said Fishbein.
Intezer’s blog lists Indicators of Compromise for the spear-phishing emails and malware used in the campaign, and Robinson said properly configured email security protocols like DMARC and SPF can also help reduce or eliminate many of the lures that rely on spoofing email addresses.
The post Year-long spear-phishing campaign targets global energy industry appeared first on SC Media.
https://www.scmagazine.com/home/security-news/phishing/year-long-spear-phishing-campaign-targets-global-energy-industry/
Published: 2021 07 08 21:50:09
Received: 2021 07 08 22:00:47
Feed: SC Magazine
Source: SC Media
Category: News
Topic: Cyber Security
Views: 2
