Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Windows Defender Exploit Guard ASR Obfuscated Script Rule
published on 2017-11-08 12:00:00 UTC by Carlos PerezContent:
On this blog post I will cover my testing of the Attack Surface Reduction rule for Potentially Obfuscated Scripts. This is one of the features that intrigued me the most. One obfuscates the scripts for several reasons:
- Bypass detection controls like AV, automatic log analysis and other controls.
- Hinder analysis of the script to determine its purpose and action.
On the offense side it is a requirement given how more tools are improving their detection the obfuscation allows to bypass them but also has the drawback of bringing attention to the code since it will look out of place. By detecting obfuscation and blocking its execution it would impact the capabilities of some actors limiting the tool-set they can use.
Microsoft describes the rule as follows in their documentation:
Rule: Block execution of potentially obfuscated scripts Malware and other threats can attempt to obfuscate or hide their malicious code in some script files. This rule prevents scripts that appear to be obfuscated from running. It uses the AntiMalwareScanInterface (AMSI) to determine if a script is potentially obfuscated, and then blocks such a script, or blocks scripts when an attempt is made to access them.
Based on the description the rule is meant to block potentially obfuscated scripts. To test this I will use the "Windows Defender Exploit Guard evaluation package" tool to see how Microsoft is testing the rule.
I launch the tool, select the rule for script obfuscation and select the setting to be Audit. I run the scenario the scenario twice.
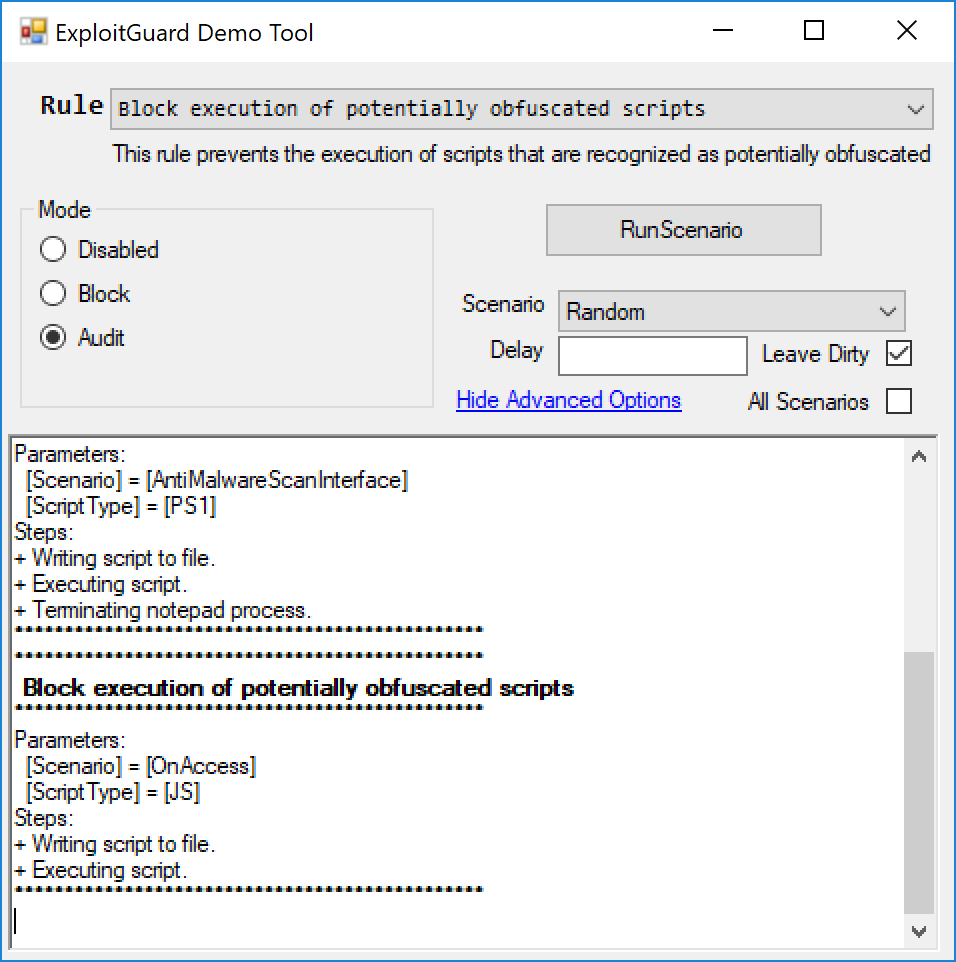
In Advanced Settings I select the option of "Leave Dirty" so I can take a look at the files it used for the test.
The PowerShell script that it used for testing did not looked obfuscated at all .
The Jscript did looked like it had an offuscated string that it never used and it then launched notpad.exe using a none obfuscated wscript.shell call.
I enabled using the PowerShell cmdlet the rule for obfuscated scripts.
Add-MpPreference -AttackSurfaceReductionRules_Ids 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC -AttackSurfaceReductionRules_Actions Enabled
I will test first how well it detects obfuscated PowerShell script. First test is a control one, I will run the same script that MS provides for testing.
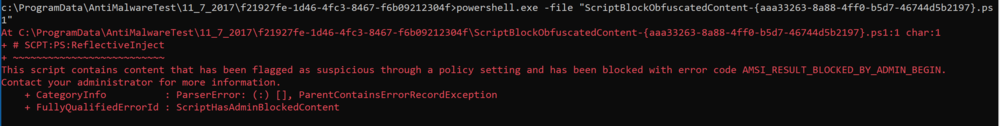
We can see it was blocked. It states it was for the PowerSploit cmdlet name. In the event log the event has an ID of 1121 like all ASR rules, the rule is specified in the EventData section of the event and it shows that was the script that was blocked.
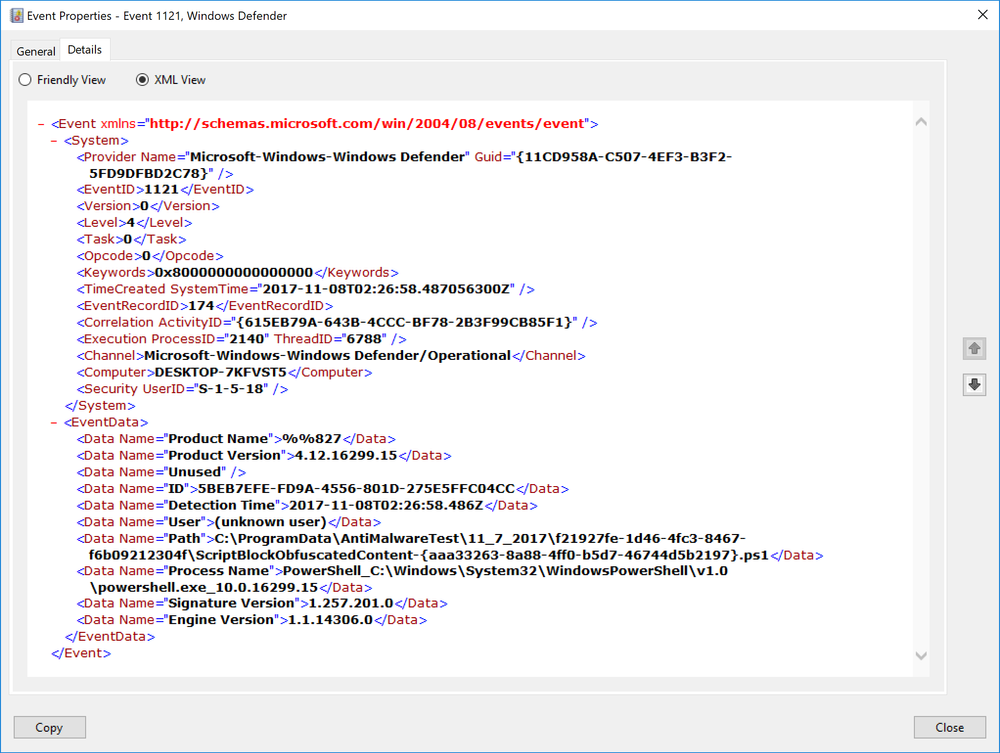
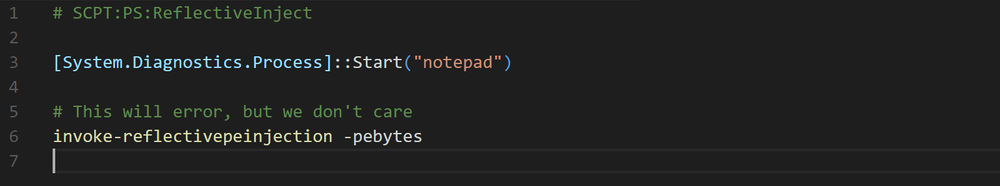
I decided to build my own script and have the PowerSploit command in it, I decided to use Daniel Bohannon Invoke-Obfuscation module to obfuscate the script to see how well it works.
Write-Host 'Getting system info' Get-WmiObject -Class "win32_operatingsystem" Write-Host 'Starting a process' Start-Process 'notepad.exe' invoke-reflectivepeinjection -pebytes
I saved the script on the target machine with no obfuscation. As soon as I saved it was caught and blocked by the ASR rule. I did not even needed to run script.
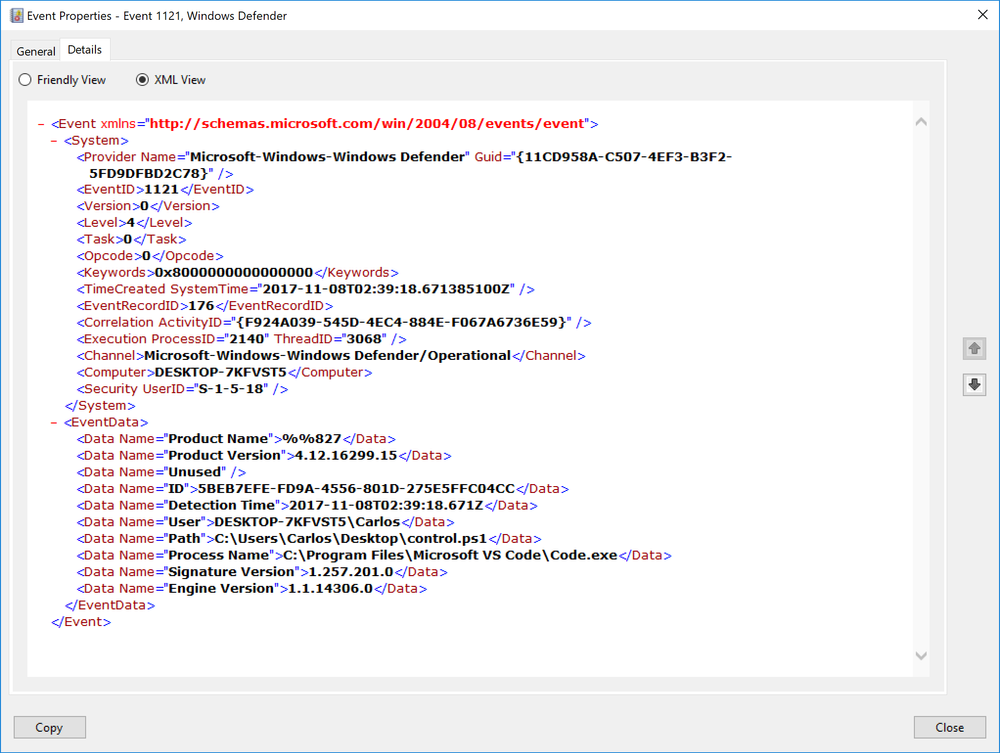
First method of obfuscation I uses was the string concatination technique in the tool.
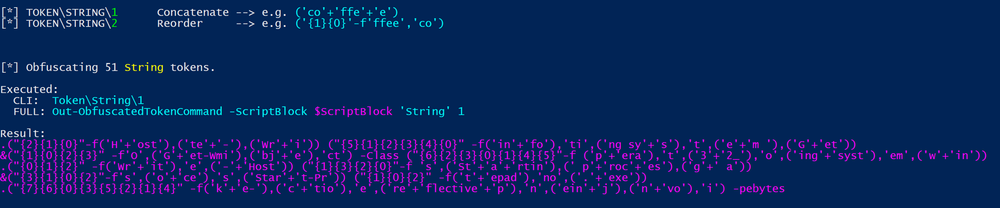
I ran the script and it executed with no problems to my surprise.
Next I obfuscated the script with the reorder technique
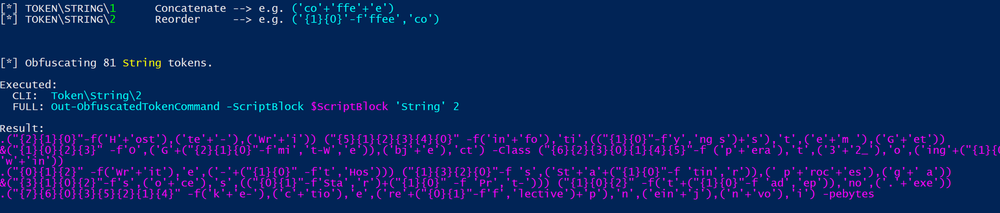
Ran the script again and to my surprised it executed without any problems. The rule is not catching at all the obfuscated script.
For PowerShell the ASR rule provided in my testing no detection of any obfuscated script.
For JS I ran it's own copy of the obfuscated JS and it triggered. Once I removed the none obfuscated section that launched notepad.exe it was not being blocked.
Sadly I do not have a tool to obfuscate Jscript reliably but there are many for VBScript. I will use the Scripting.Encoder COM object to encode a script that launches notepad.exe to see if it gets detected.
Dim obj0
Set obj0 = CreateObject("Wscript.Shell")
obj0.Run "notepad.exe"
Once encoded it looks like
#@~^TgAAAA==9b:~K4N!@#@&?OPK4%!,'~/M+lDnr(L+1OcJq/1DrwO UtnV^E#@#@&G8N!R]; PExKOwC9R6+r5hcAAA==^#~@
Next I tried obfuscation instead of encoding by using a free online obfuscation tool https://isvbscriptdead.com/vbs-obfuscator/.
Execute(chr(-5626+CLng("&H163e"))&chr(-53797+CLng("&Hd28e"))&chr(CLng("&He91e")-59569)&chr(1115680/CLng("&H8831"))&chr(-57799+CLng("&He236"))&chr(-40971+CLng("&Ha06d"))&chr(-96064+CLng("&H177aa"))&chr(CLng("&H9d12")-40162)&chr(-40140+CLng("&H9cd6"))&chr(-92141+CLng("&H16840"))&chr(-26424+CLng("&H679d"))&chr(9425928/CLng("&H13d6a"))&chr(1998848/CLng("&Hf400"))&chr(-66972+CLng("&H1060b"))&chr(CLng("&H92f8")-37526)&chr(3+CLng("&H67"))&chr(CLng("&H9fb3")-40835)&chr(998944/CLng("&H79f1"))&chr(2216008/CLng("&H8de8"))&chr(-75722+CLng("&H127ea"))&chr(-93087+CLng("&H16be2"))&chr(4261320/CLng("&H9204"))&chr(2835979/CLng("&H6daf"))&chr(CLng("&H1493d")-84188)&chr(CLng("&Hbc89")-48149)&chr(CLng("&H97f7")-38802)&chr(-55357+CLng("&Hd88c"))&chr(CLng("&H17a4a")-96744)&chr(-66498+CLng("&H1042c"))&chr(CLng("&Hae1")-2684)&chr(3691512/CLng("&H91a8"))&chr(CLng("&H15d8")-5476)&chr(-67153+CLng("&H10679"))&chr(CLng("&H7063")-28737)&chr(6261912/CLng("&H11928"))&chr(-89681+CLng("&H15ec4"))&chr(CLng("&H39b1")-14670)&chr(10802412/CLng("&H17226"))&chr(10425450/CLng("&H183da"))&chr(CLng("&Hc49b")-50219)&chr(CLng("&H78f7")-30851)&chr(3946938/CLng("&H14f2b"))&chr(6164410/CLng("&H1221e"))&chr(1537640/CLng("&H39c1"))&chr(-87077+CLng("&H1548a"))&chr(CLng("&H58d6")-22634)&chr(CLng("&H11539")-70861)&chr(1753958/CLng("&Hc983"))&chr(2733552/CLng("&H10470"))&chr(855450/CLng("&H14e29"))&chr(CLng("&He5")-118)&chr(CLng("&H107b2")-67408)&chr(CLng("&H17bc4")-97114)&chr(183456/CLng("&Heee"))&chr(-13138+CLng("&H3380"))&chr(CLng("&Ha1d3")-41345)&chr(11267217/CLng("&H1782d"))&chr(-88265+CLng("&H15937"))&chr(CLng("&H6035")-24597)&chr(CLng("&H16616")-91636)&chr(1594890/CLng("&H38a3"))&chr(-56120+CLng("&Hdba7"))&chr(CLng("&H1389c")-79912)&chr(2985560/CLng("&H7378"))&chr(1449392/CLng("&H328d"))&chr(CLng("&H2ddf")-11646)&chr(1121500/CLng("&H2bcf"))&chr(-35984+CLng("&H8cbe"))&chr(1811738/CLng("&H4612"))&chr(-56604+CLng("&Hdd94"))&chr(-69873+CLng("&H11156"))&chr(3200692/CLng("&H16fba"))&vbcrlf)
Again the script executed without any issues.
I have to admit I'm very disappointed with this ASR mitigation. I was hopping it would behave like Daniel Bohannon and Lee Holmes tool Revoke-Obfuscation that detects obfuscated scripts with great accuracy.
I would recommend to not rely on this rule and hopefully Microsoft will improve on it making it trully valuable mitigation.
https://www.darkoperator.com/blog/2017/11/8/windows-defender-exploit-guard-asr-obfuscated-script-rule
Published: 2017 11 08 12:00:00
Received: 2023 06 02 12:43:20
Feed: Blog
Source: Blog
Category: Cyber Security
Topic: Cyber Security
Views: 13
