Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.[SANS ISC] Undetected PowerShell Backdoor Disguised as a Profile File
published on 2023-06-10 08:31:11 UTC by XavierContent:
Yesterday, I published the following diary on isc.sans.edu: “Undetected PowerShell Backdoor Disguised as a Profile File“:
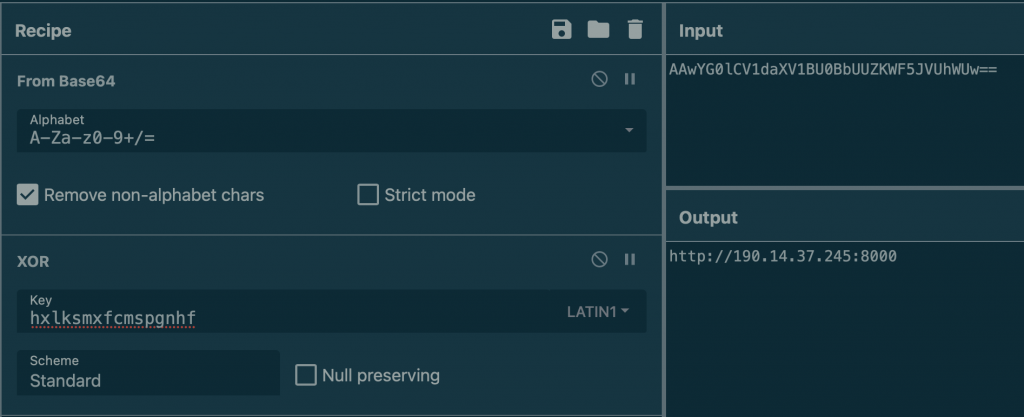
PowerShell remains an excellent way to compromise computers. Many PowerShell scripts found in the wild are usually obfuscated. Most of the time, this helps to have the script detected by fewer antivirus vendors. Yesterday, I found a script that scored 0/59 on VT! Let’s have a look at it.
The file was found with the name « Microsoft.PowerShell_profile.ps1 ». The attacker nicely selected this name because this is a familiar name used by Microsoft to manage PowerShell profiles[1]. You may compare this to the « .bashrc » on Linux. It’s a way to customize your environment. Everything you launch a PowerShell, it will look for several locations, and if a file is found, it will execute it. Note that it’s also an excellent way to implement persistence because the malicious code will be re-executed every time a new PowerShell is launched. It’s listed as T1546.013[2] in the MITRE framework… [Read more]
The post [SANS ISC] Undetected PowerShell Backdoor Disguised as a Profile File appeared first on /dev/random.
https://blog.rootshell.be/2023/06/10/sans-isc-undetected-powershell-backdoor-disguised-as-a-profile-file/
Published: 2023 06 10 08:31:11
Received: 2023 06 19 13:02:00
Feed: /dev/random
Source: /dev/random
Category: Cyber Security
Topic: Cyber Security
Views: 11
