Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.SEO Expert Hired and Fired By Ashley Madison Turned on Company, Promising Revenge
published on 2023-07-13 21:45:02 UTC by BrianKrebsContent:
[This is Part II of a story published here last week on reporting that went into a new Hulu documentary series on the 2015 Ashley Madison hack.]
It was around 9 p.m. on Sunday, July 19, when I received a message through the contact form on KrebsOnSecurity.com that the marital infidelity website AshleyMadison.com had been hacked. The message contained links to confidential Ashley Madison documents, and included a manifesto that said a hacker group calling itself the Impact Team was prepared to leak data on all 37 million users unless Ashley Madison and a sister property voluntarily closed down within 30 days.
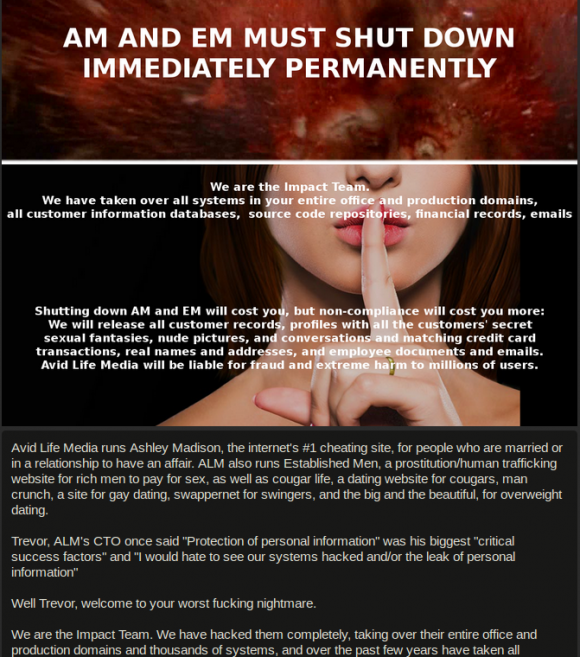
A snippet of the message left behind by the Impact Team.
The message included links to files containing highly sensitive information, including snippets of leaked user account data, maps of internal AshleyMadison company servers, employee network account information, company bank account data and salary information.
A master employee contact list was among the documents leaked that evening. Helpfully, it included the cell phone number for Noel Biderman, then the CEO of Ashley Madison parent firm Avid Life Media (ALM). To my everlasting surprise, Biderman answered on the first ring and acknowledged they’d been hacked without even waiting to be asked.
“We’re on the doorstep of [confirming] who we believe is the culprit, and unfortunately that may have triggered this mass publication,” Biderman told me on July 19, just minutes before I published the first known public report about the breach. “I’ve got their profile right in front of me, all their work credentials. It was definitely a person here that was not an employee but certainly had touched our technical services.”
On Aug 18, 2015, the Impact Team posted a “Time’s up!” message online, along with links to 60 gigabytes of Ashley Madison user data. The data leak led to the public shaming and extortion of many Ashley Madison users, and to at least two suicides. Many other users lost their jobs or their marriages. To this day, nobody has been charged in the hack, and incredibly Ashley Madison remains a thriving company.
THE CHAOS MAKER
The former employee that Biderman undoubtedly had in mind on July 19, 2015 was William Brewster Harrison, a self-described expert in search engine optimization (SEO) tricks that are designed to help websites increase their rankings for various keywords in Google and other search engines.
It is evident that Harrison was Biderman’s top suspect immediately after the breach became public because — in addition to releasing data on 37 million users a month later in August 2015 — the hackers also dumped three years worth of email they stole from Biderman. And Biderman’s inbox is full of messages about hate-filled personal attacks from Harrison.
A Native of Northern Virginia, Harrison eventually settled in North Carolina, had a son with his then-wife, and started a fence-building business. ALM hired Harrison in March 2010 to promote its various adult brands online, and it is clear that one of his roles was creating and maintaining female profiles on Ashley Madison, and creating blogs that were made to look like they were written by women who’d just joined Ashley Madison.

A selfie that William B. Harrison posted to his Facebook page in 2013 shows him holding a handgun and wearing a bulletproof vest.
It appears Harrison was working as an affiliate of Ashley Madison prior to his official employment with the company, which suggests that Harrison had already demonstrated he could drive signups to the service and help improve its standing in the search engine rankings.
What is less clear is whether anyone at ALM ever performed a basic background check on Harrison before hiring him. Because if they had, the results almost certainly would have given them pause. Virginia prosecutors charged the young 20-something Harrison with a series of misdemeanors, including trespassing, unlawful entry, drunk in public, and making obscene phone calls.
In 2008, North Carolina authorities charged Harrison with criminal extortion, a case that was transferred to South Carolina before ultimately being dismissed. In December 2009, Harrison faced charges of false imprisonment, charges that were also dropped by the local district attorney.
By the time Ashley Madison officially hired him, Harrison’s life was falling apart. His fence business had failed, and he’d just filed for bankruptcy. Also, his marriage had soured, and after a new arrest for driving under the influence, he was in danger of getting divorced, losing access to his son, and/or going to jail.
It also seems likely that nobody at ALM bothered to look at the dozens of domain names registered to Harrison’s various Vistomail.com email addresses, because had they done so they likely would have noticed two things.
One is that Harrison had a history of creating websites to lambaste companies he didn’t like, or that he believed had slighted him or his family in some way. Some of these websites included content that defamed and doxed executives, such as bash-a-business[.]com, google-your-business[.]com, contact-a-ceo[.]com, lowes-is-a-cancer[.]com (according to Harrison, the home improvement chain once employed his wife).
A background check on Harrison’s online footprint also would have revealed he was a self-styled rapper who claimed to be an active menace to corporate America. Harrison’s website lyrical-gangsta[.]com included a number of works, such as “Slim Thug — I Run — Remix Spoof,” which are replete with menacing words for unnamed corporate executives:
[HOOK]
I surf the net all night n day (the web love thug)
cuz I still surf the net all night n day
yuhh I type for my mind, got smart for my ego
still running circles round them, what’s good?
cuz I still surf, the net all night n day,
I cant stay away.
They don’t make to [sic] many hackers like me
bonafide hustler certified G
still pumpin’ the TOP 10 results
if you got the right dough!
think the results are fake? sucka Google ME
smarter than executives, bigger then Wal-Mart
Nelly strugglin’ with the fact that I’m #1 NOW
street boys know me, ain’t nuttin’ new
about to make my mill, with an all new crew
I-95 execs don’t know what to do, or where to go
watchin them stocks evaporate all their dough
I already left the hood, got up off the streets
its in my blood im a gangsta till Im deceased
moving lumber for money or typin’ in a zone
all night hackin’ till 6 in the mornin
that shit im focusin’ on, stronger then cologne
you can prolly smell the jealousy
through your LCD screen
if you still broke– better work for some green
called them Fortune execs on that legal bluff
cuz the Feds busy raidin other stuff
Imma run the Net til im six feet under
I’m a leave my mark — no reason to wonder
(Yea Yea)

Some of the anti-corporate rhymes busted by Harrison’s hacker/rapper alter ego “Chaos Dog.” Image: Archive.org.
The same theme appears in another rap (“The Hacker Backstage”) penned by Harrison’s rapper alter ego — “Chaos Dog:”
…this hacker was born to write
bust off the rhymes and watch em take flight
you know all about them corporate jets
and handing out pinkslips without regrets
oversized companies are the problem
well, I’ve got a solution
It’s called good ol’ fashioned retribution
file bankruptcy, boycott you like Boston colonists
Corporate America cant stop this Eminem style columnist
2pac would have honored my style
Im the next generation of hacker inspiration
Americans don’t want a corporate nation
All that DOW Jones shit is a dying sensation
In addition to pimping Ashley Madison with fake profiles and phony user blogs, it appears Harrison also went after the company’s enemies during the brief time he was an employee. As noted in Part I of this story, Harrison used multiple pseudonymous Vistomail.com email addresses to harass the owners of AshleyMadisonSucks[.]com into selling or shutting down the site.
When the owner of AshleyMadisonSucks[.]com refused to sell the domain, he and his then-girlfriend were subject to an unrelenting campaign of online harassment and blackmail. It now appears those attacks were perpetrated by Harrison, who sent emails from different accounts at the free email service Vistomail pretending to be the domain owner, his then-girlfriend and their friends. Harrison even went after the domain owner’s lawyer and wife, listing them both on his Contact-A-CEO[.]com website.
TURNABOUT IS FAIR PLAY
Things started going sideways for Ashley Madison when Harrison’s employment contract was terminated in November 2011. The leaked emails do not explain why Harrison was fired, but his mercurial temperament likely played a major role. According to Harrison, it was because he had expressed some moral reservations with certain aspects of his duties, although he was not specific on that point and none of this could be confirmed.
Shortly after Harrison was fired, the company’s executives began noticing that Google was auto-completing the words “Jew” and “Jewish” whenever someone searched for Biderman’s name. The results returned when one accepted Google’s recommended search at the time filled the first page with links to Stormfront, a far-right, neo-Nazi hate group. The company strongly suspected someone was using underhanded SEO techniques to slander and attack its CEO.
In July 2022, KrebsOnSecurity published a retrospective on the 2015 Ashley Madison breach which found that Biderman had become the subject of increasing ire from members of Stormfront and other extremists groups in the years leading up to the hack. According to the neo-Nazi groups, Biderman was a worthy target of their harassment not just because he was a successful Jewish CEO, but also because his company was hellbent on destroying Christian morals and families.
Biderman’s leaked emails show that in February 2012 he hired Brian Cuban — the attorney brother of Mark Cuban, the owner of the Dallas Mavericks and one the main “sharks” on the ABC reality television series Shark Tank. Through Cuban, Ashley Madison appealed their case to both Google and to the Anti-Defamation League, but neither was apparently able or willing to help.
Also in early January 2012, Biderman and other Ashley Madison executives found themselves inundated with anonymous Vistomail.com emails that were replete with profanity and slurs against Jews. Although he used fake names and email addresses, Harrison made little effort to hide his identity in several of these nastygrams.
One particularly ugly message from Harrison even included a link to a Youtube video he’d put online of his young son playing basketball for a school team. That Youtube video was included in an email wherein Harrison – then separated from his wife — lamented all the hours he spent working for Ashley Madison up in Canada instead of spending time with his son.
Harrison then turned to making threatening phone calls to Ashley Madison executives. In one incident in March 2012, Harrison called the company’s former director of Human Resources using a caller ID spoofing service to make it look like he was calling from inside the building.
ALM’s lawyers contacted the Toronto police in response to Harrison’s harassment.
“For Will to have disguised his phone number as Mark’s strongly suggest he has hacked my email, legal counsel for the opposing side in a perceived legal dispute,” ALM VP and general counsel Mike Dacks wrote in a letter to a detective at the Toronto Police. “Over the months of his many hundreds of emails he alluded a number of times to undertaking cyberattacks against us and this was noted in my original report to police.”
Based on the exchanges in Bidernman’s inbox it appears those appeals to the Toronto authorities were successful in having Harrison barred from being able to enter Canada.
ALM also contacted a detective in Harrison’s home county in North Carolina. But when the local police paid a visit to Harrison’s home to follow up on the harassment complaints, Harrison fled out his back porch, injuring himself after jumping off the second-story deck.
It is unclear if the police ever succeeded in interviewing Harrison in response to the harassment complaints from ALM. The Raleigh police officer contacted by ALM did not respond to requests for information. But the visit from the local cops only seemed to embolden and anger Harrison even more, and Biderman’s emails indicate the harassment continued after this incident.
HUMAN DECOYS
Then in August 2012, the former sex worker turned blogger and activist Maggie McNeill published screenshots from an internal system that Ashley Madison used called the “Human Decoy Interface,” which was a fancy way of describing a system built to manage phony female accounts on the service.
The screenshots appeared to show that a great many female accounts were in fact bots designed to bring in paying customers. Ashley Madison was always free to join, but users had to pay if they wished to chat directly with other users.
Although Harrison had been fired nearly a year earlier, Biderman’s leaked emails show that Harrison’s access to Ashley Madison’s internal tools wasn’t revoked until after the screenshots were posted online and the company began reviewing which employee accounts had access to the Human Decoy Interface.
“Who or what is asdfdfsda@asdf.com?,” Biderman asked, after being sent a list of nine email addresses.
“It appears to be the email address Will used for his profiles,” the IT director replied.
“And his access was never shut off until today?,” asked the company’s general counsel Mike Dacks.
TRUTH BOMBS
Biderman’s leaked emails suggest that Harrison stopped his harassment campaign sometime after 2012. A decade later, KrebsOnSecurity sought to track down and interview Harrison. Finding nobody at his former addresses and phone numbers in North Carolina, KrebsOnSecurity wound up speaking with Will’s stepmother, Tena Nauheim, who lives with Will’s dad in Northern Virginia.
Nauheim quickly dropped two big truth bombs after patiently listening to my spiel about why I was calling and looking for Mr. Harrison. The first was that Will was brought up Jewish, although he did not practice the faith: A local rabbi and friend of the family gave the service at Will’s funeral in 2014.
Nauheim also shared that her stepson had killed himself in 2014, shooting himself in the head with a handgun. Will’s mother discovered his body.
“Will committed suicide in March 2014,” Nauheim shared. “I’ve heard all those stories you just mentioned. Will was severely mentally ill. He was probably as close to a sociopath as I can imagine anyone being. He was also a paranoid schizophrenic who wouldn’t take his medication.”
William B. Harrison died on March 5, 2014, nearly 16 months before The Impact Team announced they’d hacked Ashley Madison.
Nauheim said she constantly felt physically threatened when Will was around. But she had trouble believing that her stepson was a raging anti-Semite. She also said she thought the timing of Will’s suicide effectively ruled him out as a suspect in the 2015 Ashley Madison hack.
“Considering the date of death, I’m not sure if he’s your guy,” Nauheim offered toward the end of our conversation.
[There is one silver lining to Will Harrison’s otherwise sad tale: His widow has since remarried, and her new husband agreed to adopt their son as his own.]
ANALYSIS
Does Harrison’s untimely death rule him out as a suspect, as his stepmom suggested? This remains an open question. In a parting email to Biderman in late 2012, Harrison signed his real name and said he was leaving, but not going away.
“So good luck, I’m sure we’ll talk again soon, but for now, I’ve got better things in the oven,” Harrison wrote. “Just remember I outsmarted you last time and I will outsmart you and out maneuver you this time too, by keeping myself far far away from the action and just enjoying the sideline view, cheering for the opposition.”
Nothing in the leaked Biderman emails suggests that Ashley Madison did much to revamp the security of its computer systems in the wake of Harrison’s departure and subsequent campaign of harassment — apart from removing an administrator account of his a year after he’d already left the company.
KrebsOnSecurity found nothing in Harrison’s extensive domain history suggesting he had any real malicious hacking skills. But given the clientele that typically employed his skills — the adult entertainment industry — it seems likely Harrison was at least conversant in the dark arts of “Black SEO,” which involves using underhanded or else downright illegal methods to game search engine results.
Armed with such experience, it would not have been difficult for Harrison to have worked out a way to maintain access to working administrator accounts at Ashley Madison. If that in fact did happen, it would have been trivial for him to sell or give those credentials to someone else.
Or to something else. Like Nazi groups. As KrebsOnSecurity reported last year, in the six months leading up to the July 2015 hack, Ashley Madison and Biderman became a frequent subject of derision across multiple neo-Nazi websites.
On Jan. 14, 2015, a member of the neo-Nazi forum Stormfront posted a lively thread about Ashley Madison in the general discussion area titled, “Jewish owned dating website promoting adultery.”
On July 3, 2015, Andrew Anglin, the editor of the alt-right publication Daily Stormer, posted excerpts about Biderman from a story titled, “Jewish Hyper-Sexualization of Western Culture,” which referred to Biderman as the “Jewish King of Infidelity.”
On July 10, a mocking montage of Biderman photos with racist captions was posted to the extremist website Vanguard News Network, as part of a thread called “Jews normalize sexual perversion.”
Some readers have suggested that the data leaked by the Impact Team could have originally been stolen by Harrison. But that timeline does not add up given what we know about the hack. For one thing, the financial transaction records leaked from Ashley Madison show charges up until mid-2015. Also, the final message in the archive of Biderman’s stolen emails was dated July 7, 2015 — almost two weeks before the Impact Team would announce their hack.
Whoever hacked Ashley Madison clearly wanted to disrupt the company as a business, and disgrace its CEO as the endgame. The Impact Team’s intrusion struck just as Ashley Madison’s parent was preparing go public with an initial public offering (IPO) for investors. Also, the hackers stated that while they stole all emplyee emails, they were only interested in leaking Biderman’s.
Also, the Impact Team had to know that ALM would never comply with their demands to dismantle Ashley Madison and Established Men. In 2014, ALM reported revenues of $115 million. There was little chance the company was going to shut down some of its biggest money machines.
Hence, it appears the Impact Team’s goal all along was to create prodigious amounts of drama and tension by announcing the hack of a major cheating website, and then let that drama play out over the next few months as millions of exposed Ashley Madison users freaked out and became the targets of extortion attacks and public shaming.
After the Impact Team released Biderman’s email archives, several media outlets pounced on salacious exchanges in those messages as supposed proof he had carried on multiple affairs. Biderman resigned as CEO of Ashley Madison on Aug. 28, 2015.
Complicating things further, it appears more than one malicious party may have gained access to Ashley’s Madison’s network in 2015 or possibly earlier. Cyber intelligence firm Intel 471 recorded a series of posts by a user with the handle “Brutium” on the Russian-language cybercrime forum Antichat between 2014 and 2016.
Brutium routinely advertised the sale of large, hacked databases, and on Jan. 24, 2015, this user posted a thread offering to sell data on 32 million Ashley Madison users. However, there is no indication whether anyone purchased the information. Brutium’s profile has since been removed from the Antichat forum.
I realize this ending may be unsatisfying for many readers, as it is for me. The story I wrote in 2015 about the Ashley Madison hack is still the biggest scoop I’ve published here (in terms of traffic), yet it remains perhaps the single most frustrating investigation I’ve ever pursued. But my hunch is that there is still more to this story that has yet to unfold.
https://krebsonsecurity.com/2023/07/seo-expert-hired-and-fired-by-ashley-madison-turned-on-company-promising-revenge/
Published: 2023 07 13 21:45:02
Received: 2023 07 14 01:02:20
Feed: Krebs on Security
Source: Krebs on Security
Category: Cyber Security
Topic: Cyber Security
Views: 13
