Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Web shells persist days after MOVEit mitigation
published on 2023-06-09 16:29:31 UTC by Bobby DilleyContent:
Exploiting a zero-day vulnerability in MOVEit Transfer, criminals have deployed web shells on vulnerable file transfer servers and gained access to a variety of high-profile organizations. More than a week since remediation instructions were published, Netcraft has discovered web shells still present on servers associated with energy, healthcare, and finance companies.
Web shells are control panels used by criminals to exfiltrate data from compromised servers, run exploits, and maintain remote access, often persisting long after the original vulnerability has been fixed.
Using zero-day vulnerabilities to install web shells is not a new tactic. We previously reported on web shells installed via the Microsoft Exchange ProxyLogon and ProxyShell vulnerabilities in 2021. Two years later, Netcraft continues to detect new installations of web shells on still-vulnerable Microsoft Exchange servers.
Earlier this week, we confirmed the presence of web shells on servers belonging to various companies, including two energy companies and a large state-chartered credit union. This blog post explains what we found, and why web shells remain such a key component of the cyber criminals’ toolbox.
Investigation into MOVEit hack
Following on from earlier internet scans, Netcraft probed approximately one thousand internet-visible web servers running MOVEit Transfer for the presence of web shells using the observed human2.aspx filename.
Affected servers can be identified by a fake 404 Not Found error page used by the web shell. Without the correct password, the human2 web shell returns a non-default 404 page with distinct HTML content.
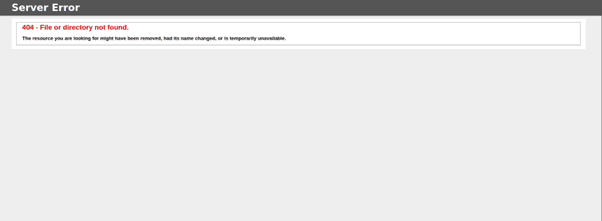
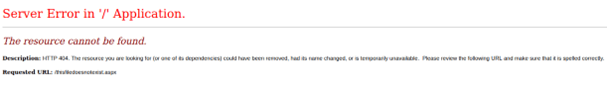
Using this technique, we confirmed the presence of web shells on hostnames belonging to various companies, almost certainly placed there using the MOVEit vulnerability. Netcraft detected web shells installed via the Microsoft Exchange ProxyLogon and ProxyShell vulnerabilities using a similar technique.
Many of the companies affected are US-based, but we also detected instances in Canada, Oman, and the Philippines. The affected companies include those across energy, healthcare, and finance industries. Due to the large amounts of sensitive customer data, and their position in supply chains, they may represent appealing targets for ransomware.
Netcraft has notified the affected companies, and at the time of writing most of the detected web shells are no longer accessible.
What are web shells? And why are they so dangerous?
Web shells are ‘The Criminal’s Control Panel’, enabling a range of cyber attacks using compromised servers. Criminals can send spam emails, exfiltrate data for sale or a ransomware attack, and use the server to host other malicious content. For around a quarter of the web shells Netcraft finds, we also find other forms of cybercrime on the same server including phishing, website defacement, cryptocurrency investment scams and malware.
Web shells can be designed with different purposes in mind, and often criminals install multiple shells on a compromised server to perform different tasks. For example, the use of “Mailers” to send out emails as part of a phishing campaign is particularly frequent: Netcraft has identified web shell mailers being used to send phishing emails impersonating over a hundred brands in the past three months.
Web shells are also used as a method of selling persistent administrative access to a compromised server. Initial access brokers operate marketplace websites where users can buy or sell remote access. These listings include anonymized information about the server including hosting provider, operating system, and even SEO statistics.
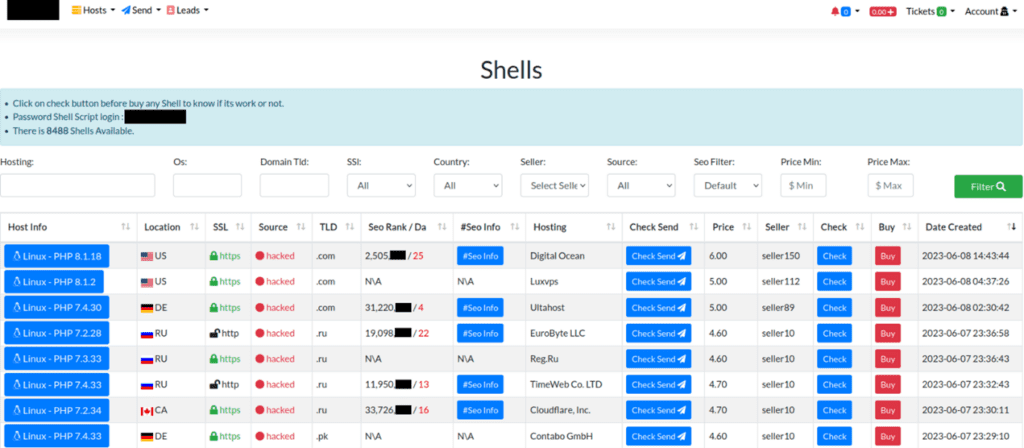
Removing the malicious content or patching the vulnerable service alone means that an attacker can simply regain access to the site and redeploy the content. Long after the underlying vulnerability has been patched, web shells allow continued administrative access to the server.
How can Netcraft help?
Netcraft has been detecting and disrupting web shells since 2016, as part of our cybercrime detection, disruption, and takedown platform. In that time, we’ve taken down half a million web shells. In the last 3 months alone, we’ve detected more than 155,000 web shells across more than 27,500 different IPs and 40,000 different hostnames.
As web shells are closely associated with other types of cybercrime, the removal of linked web shells when taking down phishing, scams, and malware impersonating a legitimate organization removes the tools available to cyber criminals and makes future attacks from the same infrastructure more difficult.
Hosting and network providers can also use Netcraft’s platform to receive threat data which will notify them whenever web shells (or other malware, or phishing activity) are detected on their infrastructure. Access to timely, validated alerts of cyber attacks deployed using their infrastructure can help registrars and hosting companies to preserve their network’s integrity and their brand’s reputation.
https://www.netcraft.com/blog/moveit-hack/
Published: 2023 06 09 16:29:31
Received: 2023 07 18 15:00:33
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 17
