Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Impact of Freenom halting registrations on cybercrime
published on 2023-08-02 15:43:12 UTC by Bobby DilleyContent:
Freenom, which offers free domain names in .tk and several other ccTLDs, is being sued by Meta for ignoring abuse complaints. Freenom subsequently paused new domain registrations in March 2023. More recently, .ga (Gabon) and .ml (Mali) have moved away from the provider.
These changes have led to a dramatic reduction in the amount of cybercrime across these TLDs — where free and easily acquired domains have long been attractive to criminals. However, the move away from Freenom has not been without incident: hundreds of domains within .ml have been implicated in a scheme to typosquat domains on the US military TLD .mil, and delayed migration in .ga which let new registrants snipe existing domains from their previous owner.
Gabon and Mali ccTLDs being migrated away from Freenom
In June, we noted that .ga had been transferred from Freenom back to the Gabonese government’s National Agency for Digital Infrastructure and Frequencies (ANINF). Afnic, the French ccTLD registry, has been helping migrate the TLD from to the Gabonese government. ANINF and Afnic jointly stated this decision is due to “the failure of the company Freenom, which has managed the .ga TLD up until now, to provide the Internet community with a satisfactory service”.
As part of the migration, several million .ga domain names were deactivated. Initial results from Netcraft’s August 2023 Web Server Survey show that over 99.99% of .ga domains have stopped working. There has been a huge decrease in the number of web-facing .ga domains, down from 5.3 million in May’s survey to just 2,601 in August’s survey. This is the result of ANINF proactively disabling .ga domain names. To reactivate their domain name, ANINF explains that domain name holders must contact their registrars.
There was a delay between .ga being transferred to ANINF and individual paid .ga domains being migrated to their new registrar, Safenames. Some domains (tele.ga, google.ga) were migrated quickly although many legitimate domains may have been vulnerable to hijacking during that window – as evidenced by asti.ga, which was re-registered at Gandi by its legitimate owner during the window, overwriting the previous registration.
On March 17th, Mali also terminated its contract with Freenom. Cybercrime on .ml is nothing new: Mali was the most-cybercrime-ridden TLD Netcraft saw in the two months following .ml domains becoming free to register in July 2013.
Misdirected US military email
Joost Zuurbier, Freenom’s CEO, recently announced that since January he has collected tens of thousands of emails intended for .mil domains but mistakenly sent to the .ml equivalents, revealing sensitive information such as diplomatic documents, passwords, and the itineraries of top officers. Zuurbier highlighted the risk of Mali’s government having the capability to receive these misdirected emails after the end of Freenom’s contract.
Netcraft has identified 59 .ml domains which have a .mil counterpart, including the US Air Force (af.ml), Army (army.ml), Marines (marines.ml), Navy (navy.ml), and the Pentagon (pentagon.ml). These domains all have DNS records pointing emails to be delivered to handle.catchemail.ml. This currently points at AWS’s eu-west-1 region.
We first saw an MX record for dfas.ml pointing at handle.catchemail.ml in the second quarter of 2015, and the record has been in place every time we have queried it since. dfas.ml is a typo of dfas.mil, the domain name of the US Defense Finance and Accounting Service.
What have we detected?
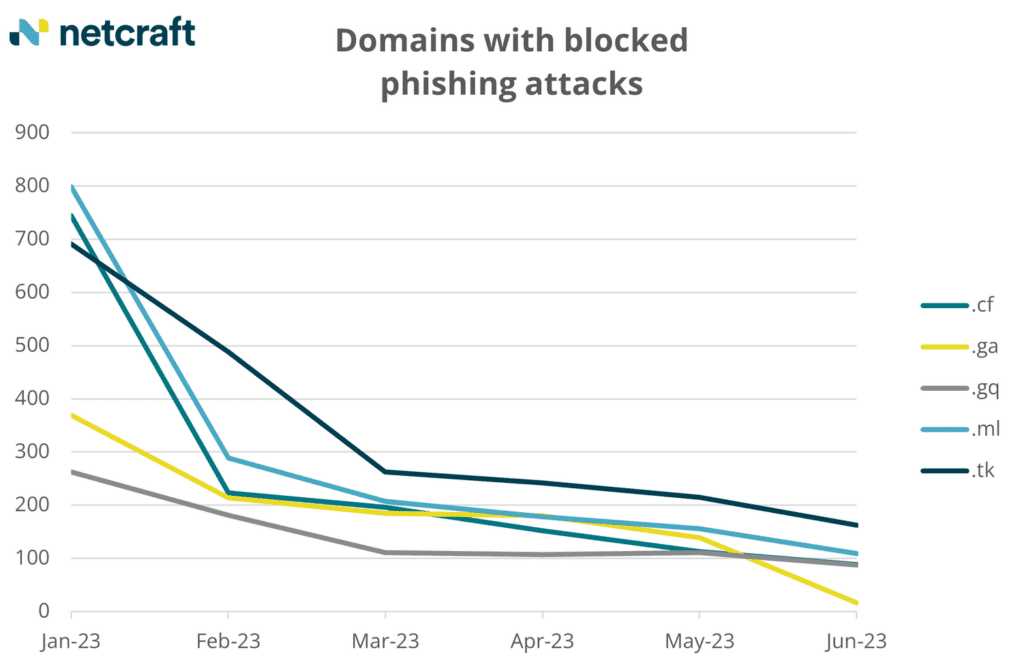
Freenom halted new registrations in March 2023. Combining insight from our Web Server Survey with our global threat intelligence shows there has been a:
- significant reduction in the amount of phishing blocked each month on Freenom’s TLDs since the start of this year (from 2,865 domains serving at least one phishing URL blocked in January to 462 in June)
- significant reduction in the number of .ga phishing blocks compared to other TLDs Freenom has managed (from 369 domains serving at least one phishing URL blocked in January to just 16 in June)
- huge decrease in the number of web-facing .ga domains (from 5.3 million domains in May’s survey to 2,601 in August’s survey).
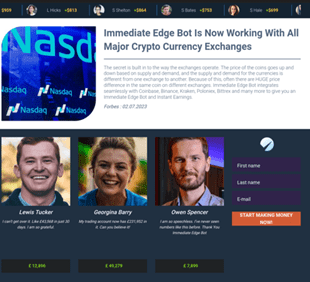
However, the move to ANINF has not put an end to all malicious use of the .ga TLD. Since 7th June, typo-squatters have been buying up short .ga domain names freed up by the transition. 822 of the web-facing .ga domains seen at this point (such as pastebin[.]ga) currently point to Trellian, a domain parking company. When visited these parked domains redirect through an advertising network to various destinations. We observed one redirect to a cryptocurrency investment scam: the final URL after the chain of redirects was immediateedgebot-appl-en[.]tazadoko[.]com.
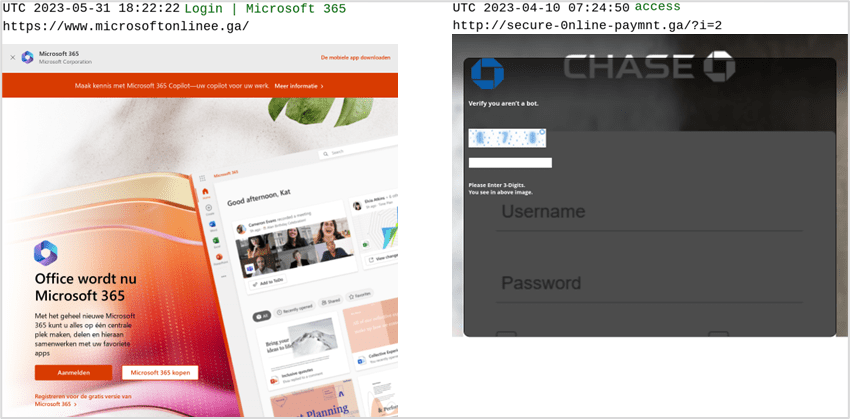
We’ve also found phishing sites (which have since gone offline) targeting Amazon, Microsoft and Chase Bank.
How can Netcraft help?
Netcraft monitors DNS registrations, zone files and certificate transparency logs for domains and hostnames deceptively similar to our customers. Our highly automated digital risk protection platform searches for typosquatting, homoglyph attacks and other lookalike domains. Discovered impersonations are monitored, and as soon as malicious content is detected, they are taken down.
This forms one part of our broad cybercrime detection and global cyber threat intelligence platform that provides online brand protection to some of the largest companies and governments in world. Contact us to learn more.
https://www.netcraft.com/blog/impact-of-freenom-halting-registrations-on-cybercrime/
Published: 2023 08 02 15:43:12
Received: 2023 08 24 12:22:53
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 18
