Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Spam Kingpin Peter Levashov Gets Time Served
published on 2021-07-20 21:30:00 UTC by BrianKrebsContent:

Peter Levashov, appearing via Zoom at his sentencing hearing today.
A federal judge in Connecticut today handed down a sentence of time served to spam kingpin Peter “Severa” Levashov, a prolific purveyor of malicious and junk email, and the creator of malware strains that infected millions of Microsoft computers globally. Levashov has been in federal custody since his extradition to the United States and guilty plea in 2018, and was facing up to 12 more years in prison. Instead, he will go free under three years of supervised release and a possible fine.
A native of St. Petersburg, Russia, the 40-year-old Levashov operated under the hacker handle “Severa.” Over the course of his 15-year cybercriminal career, Severa would emerge as a pivotal figure in the cybercrime underground, serving as the primary moderator of a spam community that spanned multiple top Russian cybercrime forums.
Severa created and then leased out to others some of the nastiest cybercrime engines in history — including the Storm worm, and the Waledac and Kelihos spam botnets. His central role in the spam forums gave Severa a prime spot to advertise the services tied to his various botnets, while allowing him to keep tabs on the activities of other spammers.
Severa rented out segments of his Waledac botnet to anyone seeking a vehicle for sending spam. For $200, vetted users could hire his botnet to blast one million emails containing malware or ads for male enhancement drugs. Junk email campaigns touting employment or “money mule” scams cost $300 per million, and phishing emails could be blasted out through Severa’s botnet for the bargain price of $500 per million.
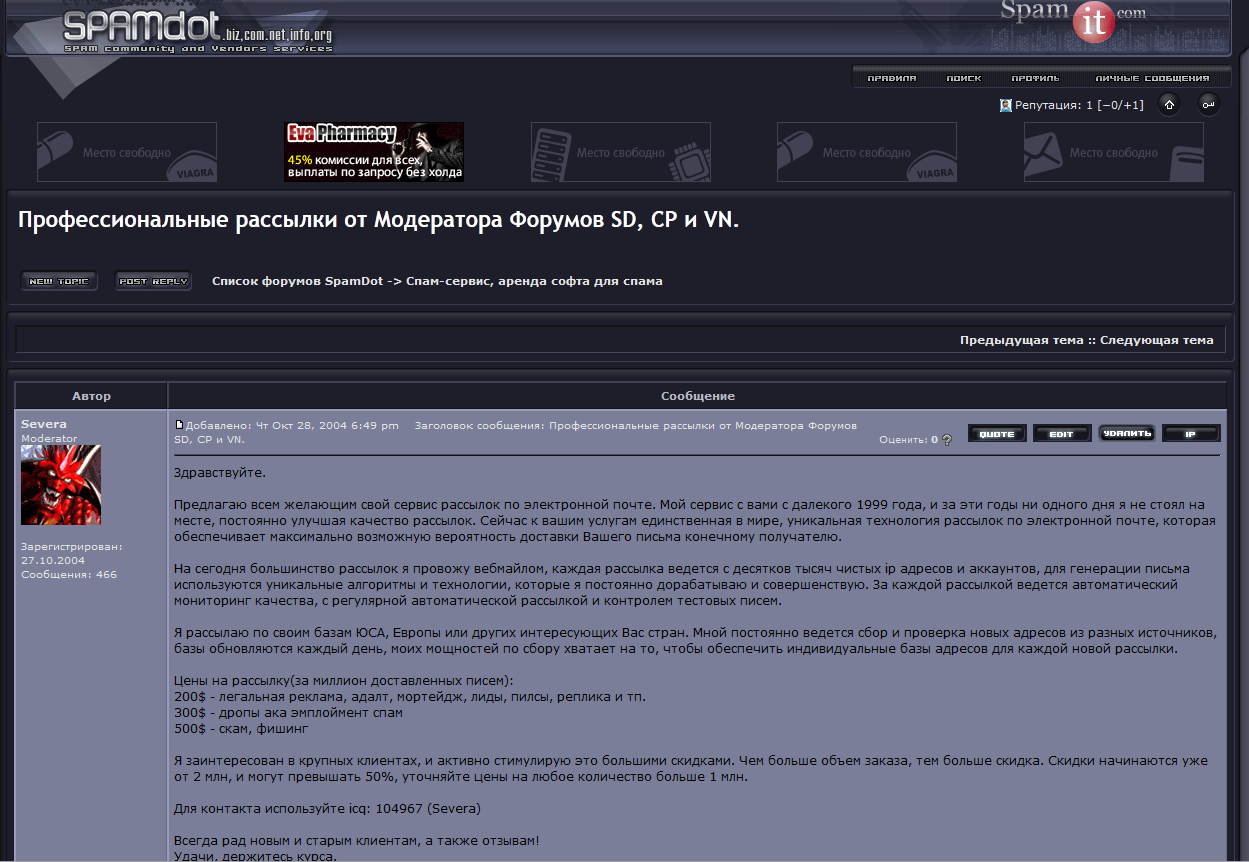
Severa was a moderator on the Russian spam community Spamdot[.]biz. In this paid ad from 2004, Severa lists prices to rent his spam botnet.
Early in his career, Severa worked very closely with two major purveyors of spam. One was Alan Ralsky, an American spammer who was convicted in 2009 of paying Severa and other spammers to promote pump-and-dump stock scams.
The other was a major spammer who went by the nickname “Cosma,” the cybercriminal thought to be responsible for managing the Rustock botnet (so named because it was a Russian botnet frequently used to send pump-and-dump stock spam). Microsoft, which has battled to scrub botnets like Rustock off of millions of PCs, later offered a still-unclaimed $250,000 reward for information leading to the arrest and conviction of the Rustock author.
Severa ran several affiliate programs that paid cybercriminals to trick people into installing fake antivirus software. In 2011, KrebsOnSecurity dissected “SevAntivir” — Severa’s eponymous fake antivirus affiliate program — showing it was used to deploy new copies of the Kelihos spam botnet.
A screenshot of the “SevAntivir” fake antivirus or “scareware” affiliate program run by Severa.
In 2010, Microsoft — in tandem with a number of security researchers — launched a combined technical and legal sneak attack on the Waledac botnet, successfully dismantling it. The company would later do the same to the Kelihos botnet, a global spam machine which shared a great deal of code with Waledac and infected more than 110,000 Microsoft Windows PCs.
Levashov was arrested in 2017 while in Barcelona, Spain with his family. According to a lengthy April 2017 story in Wired.com, he got caught because he violated a basic security no-no: He used the same log-in credentials to both run his criminal enterprise and log into sites like iTunes.
In fighting his extradition to the United States, Levashov famously told the media, “If I go to the U.S., I will die in a year.” But a few months after his extradition, Levashov would plead guilty to four felony counts, including intentional damage to protected computers, conspiracy, wire fraud and aggravated identity theft.
At his sentencing hearing today, Levashov thanked his wife, attorney and the large number of people who wrote the court in support of his character, but otherwise declined to make a statement. His attorney read a lengthy statement explaining that Levashov got into spamming as a way to provide for his family, and that over a period of many years that business saw him supporting countless cybercrime operations.
The plea agreement Levashov approved in 2018 gave Judge Robert Chatigny broad latitude to impose a harsh prison sentence. The government argued that under U.S. federal sentencing guidelines, Levashov’s crimes deserved an “offense level” of 32, which for a first-time offender means a sentence of anywhere from 121 to 151 months (10 to 12 years).
But Judge Chatigny said he had concerns that “the total offense level does overstate the seriousness of Mr. Levashov’s crimes and his criminal culpability,” and said he believed Levashov was unlikely to offend again.
“33 months is a long time and I’m sure it was especially difficult for you considering that you were away from your wife and child and home,” Chatigny told the defendant. “I believe you have a lot to offer and hope that you will do your best to be a positive and contributing member of society.”
Mark Rasch, a former federal prosecutor with the U.S. Justice Department, said the sentencing guidelines are no longer mandatory, but they do reflect the position of Congress, the U.S. Sentencing Commission, and the Administrative Office of the U.S. Courts about the seriousness of the offenses.
“One of the problems you have here is it’s hard enough to catch and prosecute and convict cybercriminals, but at the end of the day the courts often don’t take these offenses seriously,” Rasch said. “On the one hand, sentences like these do tend to diminish the deterrent effect, but also I doubt there are any hackers in St. Petersburg right now who are watching this case and going, ‘Okay, great now I can keep doing what I’m doing.'”
Judge Chatigny deferred ruling on what — if any — financial damages Levashov may have to pay as a result of the plea.
The government acknowledged that it was difficult to come to an accurate accounting of how much Levashov’s various botnets cost companies and consumers. But the plea agreement states a figure of approximately $7 million — which prosecutors say represents a mix of actual damages and ill-gotten gains.
However, the judge delayed ruling on whether to impose a fine because prosecutors had yet to supply a document to back up the defendant’s alleged profit/loss figures. The judge also ordered Levashov to submit to three years of supervised release, which includes constant monitoring of his online communications.
https://krebsonsecurity.com/2021/07/spam-kingpin-peter-levashov-gets-time-served/
Published: 2021 07 20 21:30:00
Received: 2021 07 20 22:05:57
Feed: Krebs on Security
Source: Krebs on Security
Category: Cyber Security
Topic: Cyber Security
Views: 26
