Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Phone scams conducted using PayPal’s own invoicing service
published on 2023-09-20 09:49:42 UTC by Graham EdgecombeContent:
Phishing attacks often start with an email or text message that links to a malicious web site designed to steal sensitive information. However, some instead direct recipients to call a phone number. Despite claiming to belong to a legitimate organization these fake phone numbers are controlled by the criminal. Callers can be tricked into sending money, sensitive information, or giving access to online accounts and devices through persuasive social engineering tactics.
This blog post looks at a recent attack that uses PayPal’s own invoicing service to conduct such a phone-based phishing scam.
Phishing attacks lurking within the legitimate correspondence from familiar brands can be hard to spot. For example, Netcraft investigated the following email, sent with a from address of service@paypal.com:
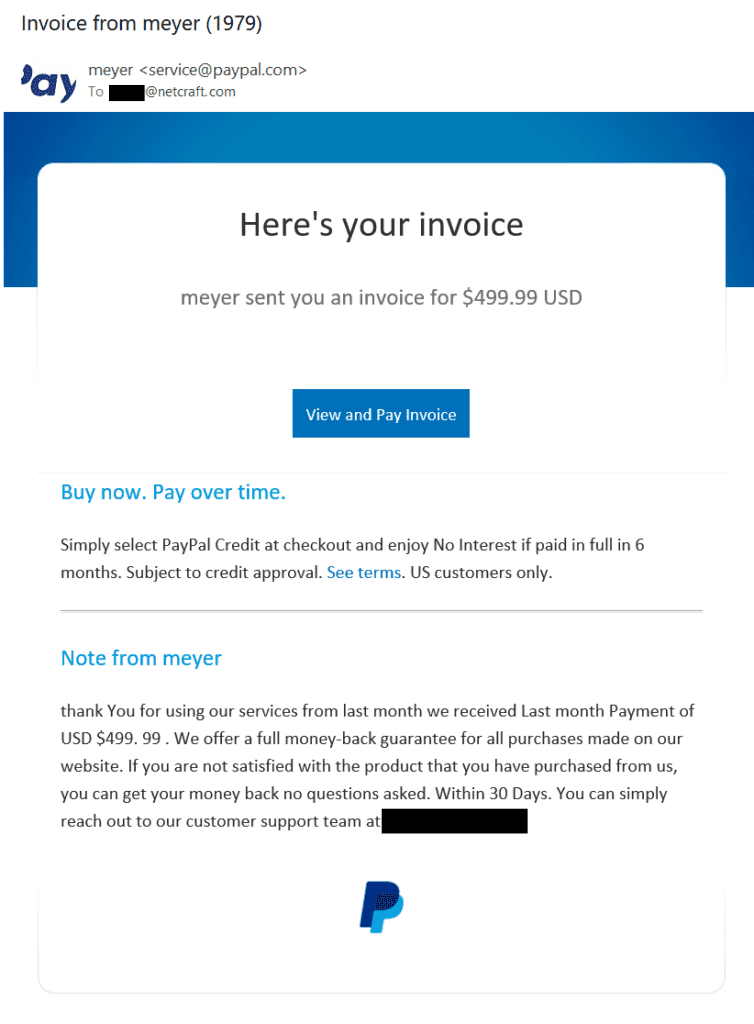
Calling the phone number (redacted in the above screenshot) confirms the impersonation. The criminal answering the call starts by introducing themselves as a PayPal employee from the billing or cancellation department. They ask the victim to confirm the invoice number, a common tactic designed to create the impression that this is a legitimate interaction, and then progress the scam from there. This could involve:
- trying to gain remote access to the victim’s device, by asking the victim to install a remote desktop application like AnyDesk or TeamViewer
- installing malware (malicious software) on the victim’s device
- tricking the victim into transferring money into a bank account controlled by the criminal
All the while, the criminal collects personal information about the victim that could be used for future attacks or sold to other criminals on the dark web.
In this case, the phone number was suspended within hours of Netcraft alerting the phone company to the scam. Other would-be victims who later received emails containing the same fraudulent phone number have been protected from falling victim to this scam.
Anatomy of the scam
This attack is much more difficult to detect than most phishing attacks because the fraudster has made use of PayPal’s free invoicing service to generate the lure for the scam. The email originates from PayPal’s own email server, and the link in the email goes to an invoice on PayPal’s own site, thus leading unwary victims to believe it is a real invoice.
But if we look at the text used within the email itself, there are some tell-tale signs of unusual behaviour, including:
- Grammatical errors and irregular capitalization (‘thank You’). If this were a genuine invoice, these trivial mistakes will most likely have been corrected.
- The unusual choice of words (‘simply reach out’, ‘get your money back no questions asked. Within 30 days’) suggests that this message has been created by a non-native English speaker.
- The payment’s sender (‘meyer’) is unknown to the receiver. Clicking the link shows that the sender’s PayPal account is registered to a generic Gmail address. Legitimate large businesses, such as PayPal, typically use email addresses under their own domain name.
Clicking the link displays the invoice below, which is hosted on PayPal’s own site. Victims who have been trained to check the domain name in their browser’s address bar may therefore think this is a genuine invoice.
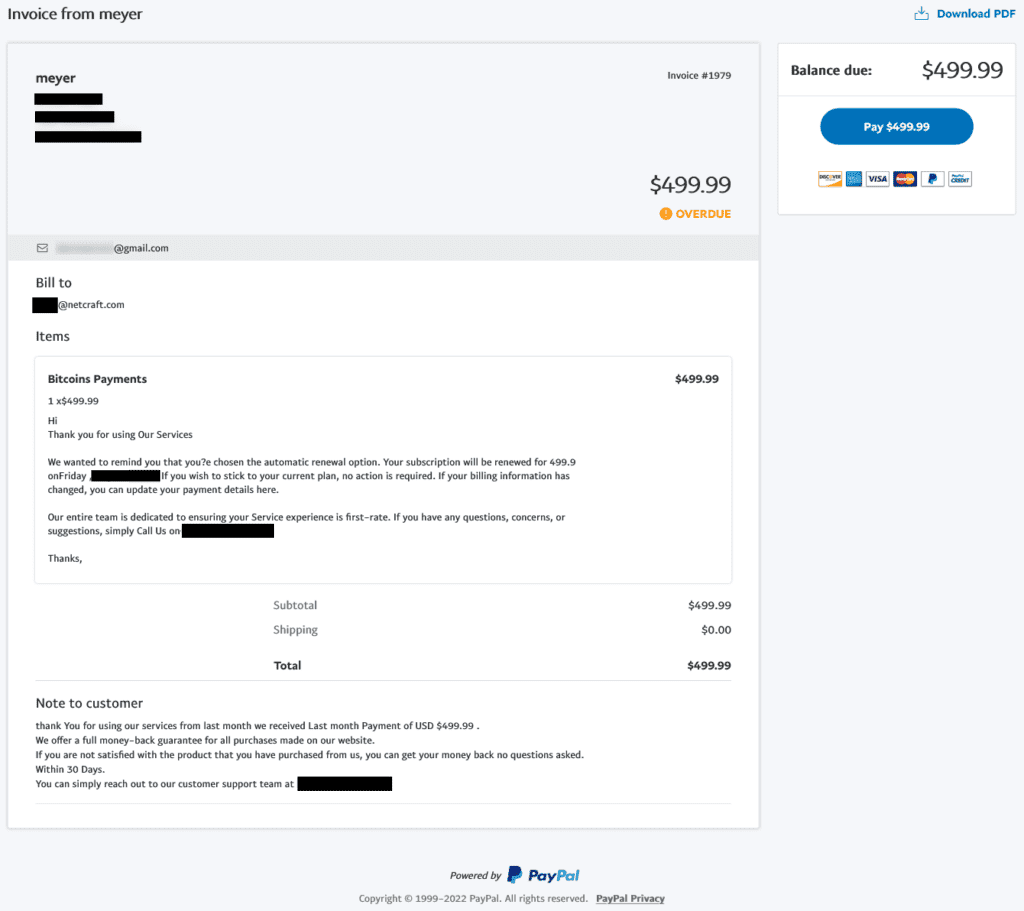
The invoice claims to be for a cryptocurrency payment for an unnamed service. Cryptocurrencies are often used in scam messages: criminals can instantly and irrevocably send the entire balance elsewhere, with no comeback for the victim. Phishing attacks are commonly designed to provide a false sense of urgency to make the victim act quickly, without thinking. This example uses an ‘automatic renewal’ to encourage the victim to act quickly before the service ‘renews’.
How can Netcraft help?
In the last 18 months, Netcraft has helped take down over 21,000 phone numbers. We’ve detected a large variety of companies being targeted by similar scams, including BitDefender, Coinbase, Ebay, Geek Squad, McAfee, Norton, PayPal, Target, QuickBooks, Walmart, as well as various US government departments.
Netcraft’s brand protection operates 24/7 to discover phishing, fraud, scams, and cyber attacks through extensive automation, AI, machine learning, and human insight. Our disruption & takedown service ensures that malicious content is blocked and removed quickly and efficiently—typically within hours.
To find out how the Netcraft’s platform can protect your brand and your customers, you can request a demo at netcraft.com, or find out more by visiting our pages for brand owners.
https://www.netcraft.com/blog/phone-scams-conducted-using-paypals-own-invoicing-service/
Published: 2023 09 20 09:49:42
Received: 2023 09 20 11:42:24
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 14
