Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Uncloaking Fake Search Ads
published on 2023-10-12 09:45:21 UTC by Bobby DilleyContent:
Search engine ads are not always as they seem. Cybercriminals can take advantage of the ability to precisely target potential victims, tricking them into clicking malicious links prominently displayed before the intended legitimate destination.
This blog post takes a detailed look at the increasingly sophisticated usage of the technique known as cloaking, which is used to surreptitiously direct users to malicious URLs from search adverts displaying legitimate URLs of real companies.
How does cloaking work?
For legitimate adverts displayed in search engine results pages, when the link is clicked, it directs the user to the displayed website. These adverts are ostensibly verified by ad publishers such as Google or Bing. Bing’s platform is also used by Yahoo and AOL.
The most naive use of fake search adverts displays the fake destination to the victim. If clicked, this would direct the user to the website as displayed, albeit a malicious copy of the intended destination. This makes it easy for ad publishers to automatically discover and block adverts pointing to malicious URLs using threat intelligence feeds.
Fake ads created using cloaking are different in several ways:
- When clicked, the user is sometimes taken to a different URL to the URL shown in the search results.
- The ad publisher will not necessarily know that the URL to which the fake ad directs the user is malicious, as the cloaker ensures that the publisher is directed to the displayed URL when checking the ad. The displayed URL does not contain malicious content.
- Clicking on the same advert can direct different users to different final URLs.
It is easier for users to fall victim to this type of fake ad:
- The fake ad will display a legitimate URL on the search engine results, alongside the legitimate page title, description and even Google reviews.
- Since it displays a legitimate URL in the search result, it is impossible to tell that it could be potentially malicious until after a user has clicked on the link. Users might not check the address bar for the URL to which they have been redirected.
This technique is currently being used to target a variety of brands including Tesco, Airbnb, McDonald’s, and Argos, as shown below.
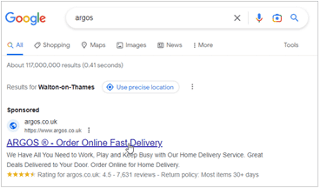
Search result for ‘Argos’ on Google, apparently displaying genuine details.
The advert displays:
- the legitimate Argos URL (https://www.argos.co.uk)/
- convincing looking details (We Have All You Need to Work, etc)
- a fake 4.5 star rating
Users who click on the link are directed either to the real Argos site (argos.co.uk), or the fake shop site shown below (agross[.]store).
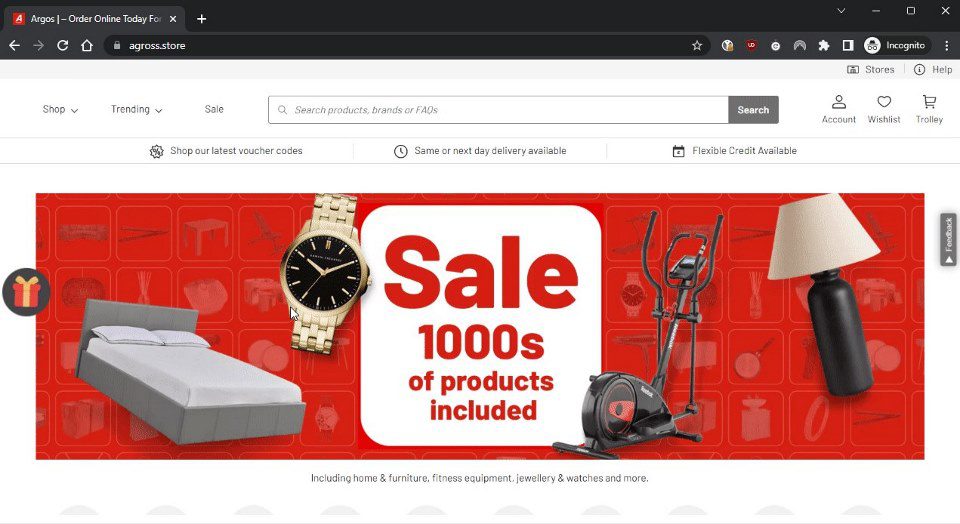
Fake shop site (agross[.]store).
Cloaks and daggers
It is worth noting that cloaking itself is not a new technique, as this Facebook article from 2017 demonstrates. Cloaking is a known issue for ad publishers: Google explicitly bans ‘Using click trackers to redirect users to malicious sites’ in its ads policy.
One way cloaking can be implemented is by setting up a cross-domain redirect as described by Google’s own support page. This allows the criminal to set a ‘click tracker’, that acts as a ‘cloaker’, which can then be used to redirect users to malicious sites. A criminal starts by setting up an ad for the legitimate website (for example, argos.co.uk) so that the legitimate URL is displayed in the search engine results. They then set up a click tracking service that uses cross-domain redirects to redirect to the cloaker.
When the cloaker detects a real user, rather than a bot used by an ad publisher to verify the advert, it may redirect the user to a malicious site. This malicious redirect is not guaranteed to happen all the time, to reduce the chance of it being detected by any further manual checks performed by ad publishers. Cloakers may distinguish bots from humans based on factors like the user’s IP address, the User-Agent header, and browser language settings.
The same cloaker site can be used for multiple different ad campaigns, as determined by an ad campaign ID passed in the URL parameter. The Argos example redirects to either argos.co.uk or a fake shop at agross[.]store. The same cloaker domain also targets Tesco, redirecting to either tesco.com or an affiliate marketing scam at supsale[.]club/tsco-uk/.
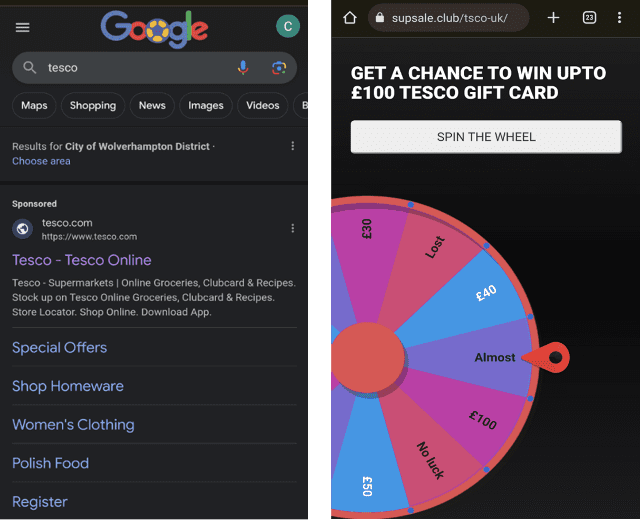
Searching for Tesco on Google is returning a malicious advert for a Tesco affiliate scam, hosted on hxxps://supsale[.]club/tsco-uk/
We have also detected fake ads targeting McDonalds and Marks & Spencer that use the same template for affiliate marketing scams. The McDonalds ad redirects either to its legitimate site (https://www.mcdonalds.com/us/en-us.html) or the affiliate marketing scam shown below.
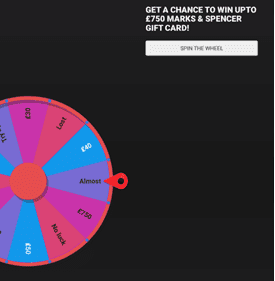
Affiliate marketing scam site Savingspot[.]club/markandsper-uk
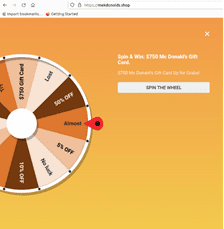
Affiliate marketing scam site mekdonolds[.]shop
How Netcraft can help
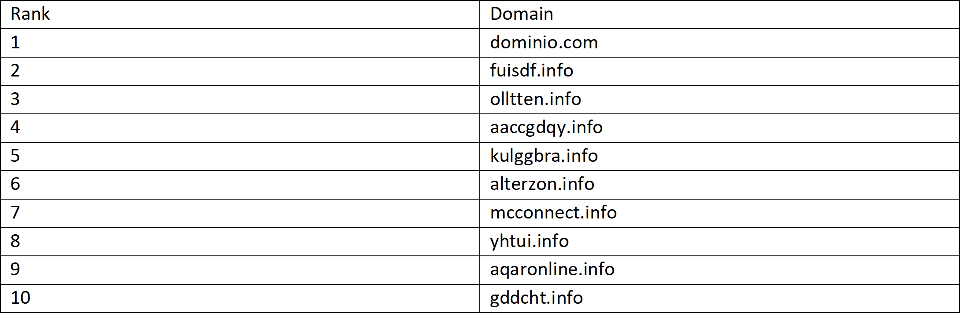
Netcraft’s Cybercrime Detection Service includes a component that targets fake search engine ads. The following table shows the top 10 domains that are running one of the cloaking software packages detected by Netcraft in the past 6 months. These are used to redirect fake ads to a variety of malicious websites. For example, we have blocked 51 instances of health product scams redirected to from boonies[.]info.
Netcraft automatically detects phishing adverts targeting our customer’s brands, including country specific adverts on sites such as Google, Bing, Yahoo and DuckDuckGo. Countermeasures are carried out against any malicious adverts found by sending both the advert URL and the phishing site to which they redirect to our Domain and Website Takedown platform.
The Netcraft browser extension blocks malicious destination URLs in real-time before they load, even if ad publishers’ automated scanners did not detect them. Since it runs on the user’s device, it cannot be circumvented by the cloaker’s anti-monitoring system.
Find out more
Netcraft’s mission is to detect and disrupt cybercrime at scale through constant innovation, extensive automation, and unique insight, delivering a safer online experience for everyone.
To find out how Netcraft’s cybercrime detection, disruption and takedown platform can protect your organization and your customers, you can request a demo or find out more by visiting https://www.netcraft.com/platform/.
https://www.netcraft.com/blog/fake-ads/
Published: 2023 10 12 09:45:21
Received: 2023 10 13 11:42:49
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 14
