Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score..zip TLD: six months on, and still rollin’
published on 2023-11-29 13:13:51 UTC by Bilaal RashidContent:
It has been six months since Netcraft first reported on abuse of the new .zip TLD, outlining the fraudulent activity we detected and blocked. Within weeks of its launch, Netcraft had detected many fresh .zip domain registrations designed to exploit confusion between the new TLD and the .zip file extension for ZIP archives.
So, what has changed in the last 6 months? Not much, it seems.
.zip registrations
The rate of new .zip domains registrations has declined since our previous blog post. Despite this, there are now:
- 16,705 registered .zip domains (a threefold increase since our previous post)
- 8,432 .zip domains with A records in total (a fourfold increase)
- 4,421 .zip domains with MX records in total, only 619 of which don’t also have A records
- 4,196 distinct IP addresses for .zip domains in total (a fivefold increase)
- 417 .zip domain names that mention ‘installer’ or ‘update’ (a twofold increase)
Out of these domains, we discovered 5 serving zip bombs. In addition, the larger number of distinct IP addresses (1 for every 4 domains now, compared to 1 for every 6 domains six months ago) suggests that .zip domains are becoming more diverse.
Malicious websites
Netcraft has blocked 50 malicious .zip domains since the previous post on 17 May 2023, bringing the total to 56. These domains mostly impersonate Microsoft, Google, and Steam, as the following figure illustrates:
Other notable attacks include:
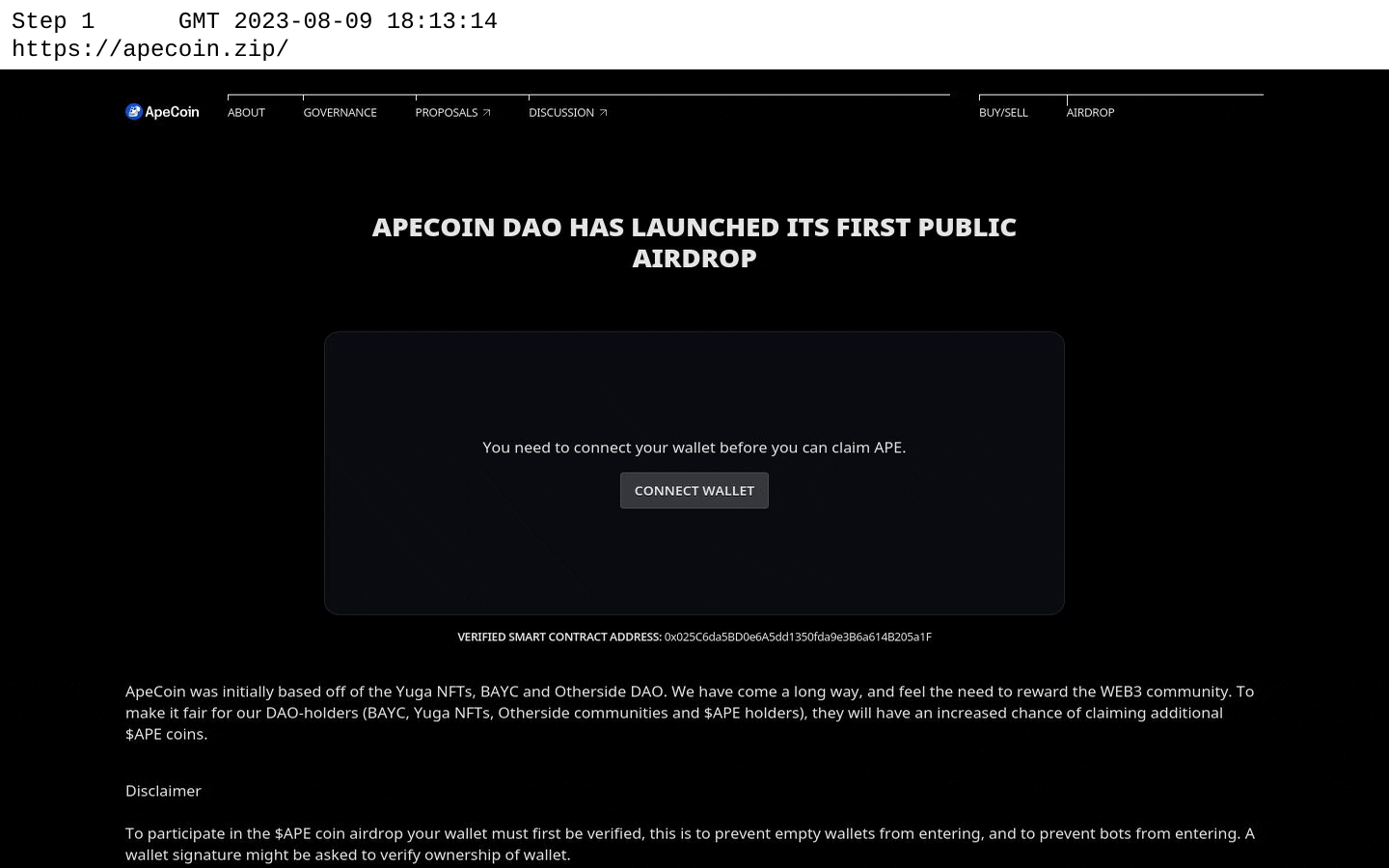
- Apecoin[.]zip, first seen on 9th August 2023, is a crypto drainer scam impersonating a cryptocurrency platform. It purports to add cryptocurrency to a user’s wallet, but when authorisation is given instead transfers all their assets (cryptocurrency, NFTs, etc) to the criminals operating the site. This same technique is being used by criminals exploiting people’s generosity around the Gaza conflict.
- Sledgehammer[.]zip, first seen on 11th July 2023, impersonates the official website for a Discord bot. It tricks users into adding a bookmarklet that runs malicious JavaScript allowing the attacker to take over the victim’s Discord account.
![Slgedgehammer[.]zip](https://www.netcraft.com/wp-content/uploads/2023/11/image4.png)
- Tronox[.]zip, first seen 28 May 2023, impersonates a Microsoft login screen. The page contains invisible text inputs that the browser’s autofill may inadvertently populate. This could lead to leaking of personal information (such as their full name, address, and credit card details).
![tronox[,]zip, step 1](https://www.netcraft.com/wp-content/uploads/2023/11/image51.png)
![tronox[.], step 4](https://www.netcraft.com/wp-content/uploads/2023/11/image7.png)
- V0464309[.]zip, first seen 31 May 2023, impersonates a law firm and tricks visitors into installing an update supposedly to fix a Chrome security vulnerability. Doing so downloads malware that harvests email credentials. This uses a common attack technique for .zip domains: mimicking software version numbers to trick victims into thinking they are downloading legitimate software. Fraudsters can also use non-standard slash characters, such as the Unicode division slash (∕), to create download links that appear to be from legitimate, well-known websites: this works by embedding these characters in HTTP Basic Authentication credentials within the URL, while actually connecting to the .zip domain.
![V0464309[.]zip](https://www.netcraft.com/wp-content/uploads/2023/11/image8.png)
We’ve also detected:
- 19 domains hosting fake Microsoft pages, some of which were only accessible from certain geographical locations. They redirected to legitimate pages or Rickrolls when accessed from outside the targeted region
- Two domains hosting web shells
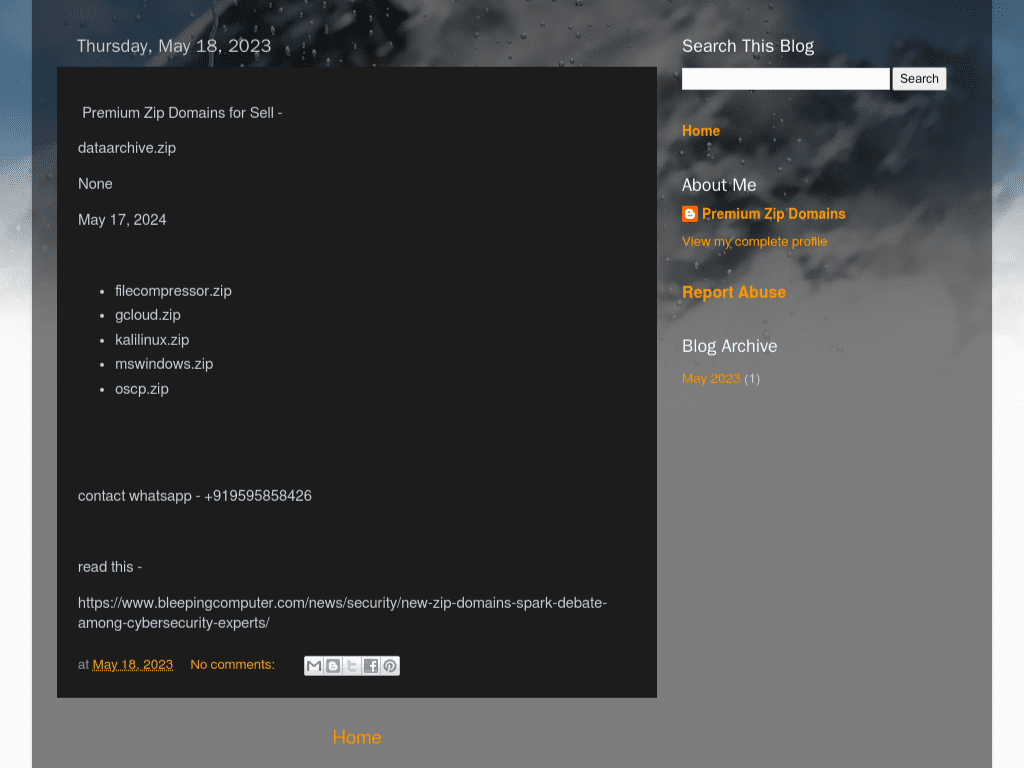
- An individual offering suspicious .zip domains for sale. The page linked to an article explaining how .zip domains could be used maliciously
‘Altruistic’ websites
As we mentioned in our original blog post, we’ve also continued to see websites that raise awareness about the possible dangers of .zip domains. For example, Mrd0x[.]zip is a fake WinRAR window that demonstrates how users may be tricked into thinking they have opened a zip file, when in fact they are downloading malware.
![Mrd0x[.]zip, a fake WinRar window](https://www.netcraft.com/wp-content/uploads/2023/11/image10.png)
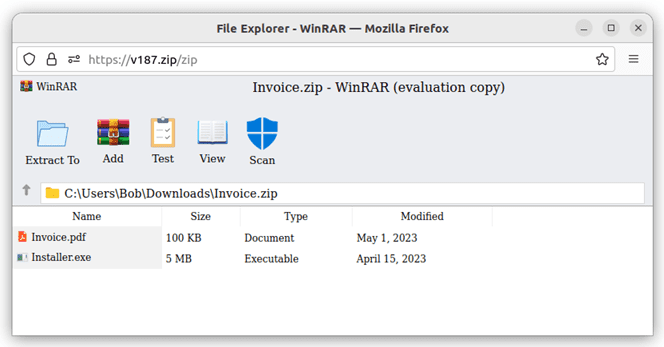
V187[.]zip demonstrates how sites can also be displayed in a popup window, making the deception even more convincing.
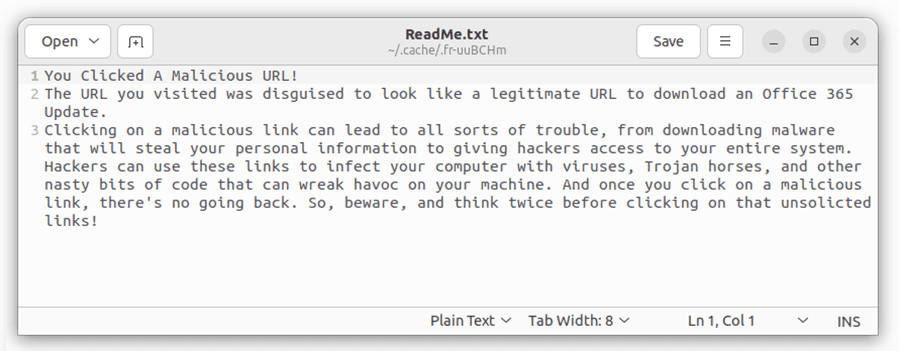
Office365[.]1[.]14[.]win-x86[.]zip also warns users about the dangers of the .zip TLD. Unlike the majority of these ‘altruistic’ sites warning about the dangers of clicking on unsolicited links, Office365[.]1[.]14[.]win-x86[.]zip displays a fake GitHub page to make the download appear legitimate.
![Office365[.]1[.]14[.]win-x86[.]zip](https://www.netcraft.com/wp-content/uploads/2023/11/image12.png)
The page immediately downloads a .zip file containing a ‘warning’ message.
Perhaps encouragingly, a much larger number of .zip websites warned visitors about the dangers of the .zip TLD deceptions, compared to the number that hosted malicious content. Having said that, these altruistic sites are using the same tactics that criminals themselves rely on, potentially providing reusable code and new ideas for fraudsters.
How can Netcraft help?
Our position at the epicentre of the battle against cybercrime allows us to rapidly identify, monitor and react to new threats, like those identified in this post. We continue to monitor for malicious content on .zip and other new TLDs. The Netcraft browser extension and mobile apps block the .zip threats described in this post, and will block new threats as we discover them.
We offer solutions for domain registries and domain registrars, including real-time alerts or takedowns for fraudulent content found on your TLD/infrastructure and a tool for analysing the likelihood that a new domain name is deceptive and will be used for fraud.
About Netcraft
Netcraft is the world leader in cybercrime detection, disruption, and takedown, and has been protecting companies online since 1996. We help organizations worldwide (including 12 of the top 50 global banks) and perform takedowns for around one third of the world’s phishing attacks, taking down 90+ attack types at a rate of 1 attack every 15 seconds. Our malicious site feeds protect billions of people around the world from phishing, malware, and other cybercrime activities.
https://www.netcraft.com/blog/zip-tld-six-months-on-and-still-rollin/
Published: 2023 11 29 13:13:51
Received: 2023 11 29 15:41:36
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 28
