Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.“Quishing” you a Happy Holiday Season
published on 2023-12-19 09:10:59 UTC by Bobby DilleyContent:
QR Code phishing scams — What they are and how to avoid them.
Originally invented to keep track of car parts in the early 90s, QR codes have been around for decades. After gaining broader acceptance during the COVID-19 pandemic, they are now—perhaps inevitably—being exploited by cybercriminals. Quishing, or QR Code phishing, exploits smartphone users scanning the 2D barcode, which leads to a phishing site, malicious link, or another cyber attack.
We’ll look at the threat from QR code-based phishing and consider why cybercriminals are adopting this technique. Additionally, we’ll explore opportunities to detect and disrupt these attacks at scale.
QR codes in phishing emails: what’s the threat?
QR codes work precisely as malicious links; a victim who scans the QR code – typically using their smartphone – will be directed towards a malicious site. From here, the deception can continue as with any other phishing campaign.
By now, many know how to spot suspicious-looking links in phishing emails that mimic official communications from established brands or institutions. The opposite is true with QR codes: there is typically no user-accessible way to check the destination before scanning.
From a cybercriminal’s perspective, there are several reasons to use QR codes for phishing, often dubbed quishing, including:
- Hiding URLs from users – QR codes provide criminals with a very effective mechanism for hiding suspicious URLs, making this an ideal way to bypass growing user skepticism concerning clicking questionable and shortened URLs.
- Circumventing corporate controls – If users receive a QR-based phishing email on their work computer, they will likely scan the code using their phone. Cybercriminals know personal devices may have less built-in security than a company computer or phone. It’s a subtle way of encouraging victims to use devices not under corporate control and are, therefore, less likely to be prevented from falling victim.
- Hiding URLs from security tools – Unlike Netcraft’s advanced detection services, many security tools and systems cannot scan images, relying on text-based analysis to detect malicious links within emails, which means they can’t see the links hidden in QR codes so that QR-based phishing emails can slip through.
Anatomy of a QR code scam
In the following example, a QR code is included in an email purporting to be from Microsoft. Note that the instructions accompanying the code are also part of the image (as well as a realistic-looking Microsoft logo), which means the email will evade some text-based filtering techniques.
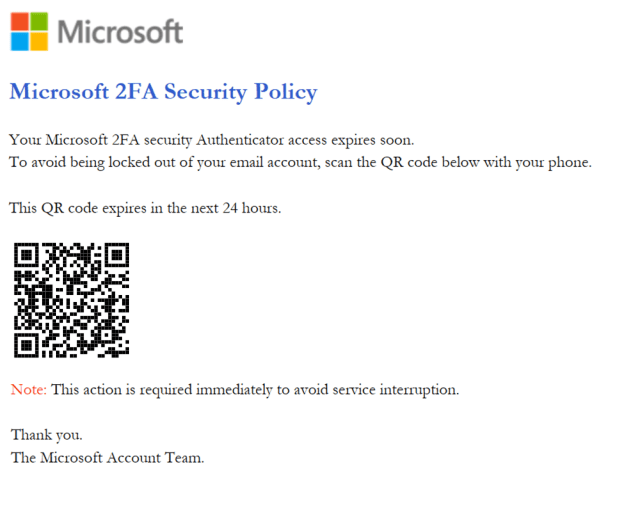
Figure 1 A phishing email targeting Microsoft includes a QR code that directs the victim to a malicious website.
It’s worth noting that the criminal’s deception includes a reference to 2FA (two-factor authentication). Setting up 2FA’ is associated with improving online security and is often legitimately completed using QR codes. The QR code directs the user to a phishing site that tricks the victim into entering their Microsoft login and password.

Figure 2 Phishing site designed to capture victims’ Microsoft Account credentials.
The following example again targets users within a corporate network, an environment where DocuSign (a service that allows organizations to manage electronic agreements) is commonly used. Furthermore, the image within the email includes the QR code and text instructions. On scanning the code, the victim is directed to another phishing site that attempts to steal Microsoft credentials.
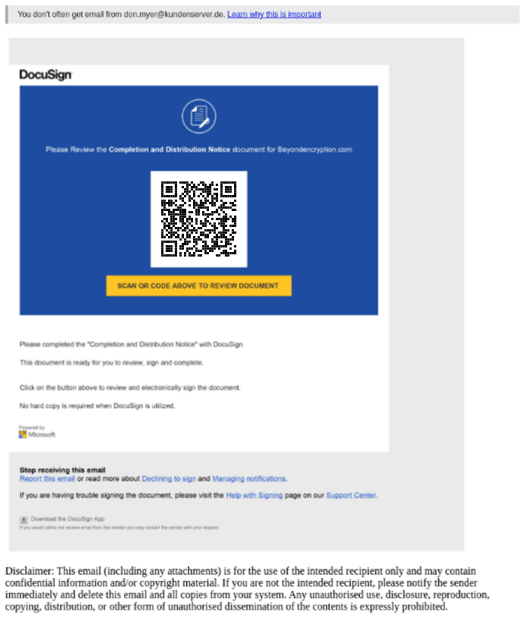
Figure 3 A phishing email targeting DocuSign, which includes a QR code that directs the victim to a malicious website
Protecting your teams and yourself from ‘Quishing’ attacks
If you receive a suspicious email containing a QR code, forward the email, or send a screenshot of the QR code, to the Netcraft team at scam@netcraft.com. We’ll analyze the email, extract the URL, and if it contains a link to a phishing site (or another type of malicious website) we’ll block the website so it can’t be used to trick other users.
Customers of Netcraft are automatically protected against QR code-based phishing attacks through our best-in-class threat detection. Unlike many other security platforms, our anti-phishing platform can identify QR images lurking in emails, and block access to malicious sites before they can do any harm.
Connect with the Netcraft team today to start protecting your team from quishing attacks and various other forms of phishing. Book your demo here, or find out more by visiting our Guide to preventing phishing and other cyber attacks.
https://www.netcraft.com/blog/quishing-you-a-happy-holiday-season/
Published: 2023 12 19 09:10:59
Received: 2023 12 19 22:41:48
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 19
