Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Creating custom username list & wordlist for bruteforciing.
published on 2013-12-18 08:34:00 UTC by nirav desaiContent:
During brute-forcing every time you need custom password list & username list. Username list is as well as important as password list, it should be unique for every organization.If we use traditional large number of username list , then it will be tedious process.Custom username list also useful in username enumeration.
Creating custom username list:-
(1)Jigsaw:-
During information gathering stage , you may use jigsaw script. It is great script for gathering employees `s details like fullname, position, department, email addresses.You should use script with your jigsaw credential.
some times email address`s initial can be username of employee.So you can get different username from output of jigsaw script.
(2)Username script:-
If you have full name of users then you can use username.py script to generate possible username by using different combination of first name & last name.
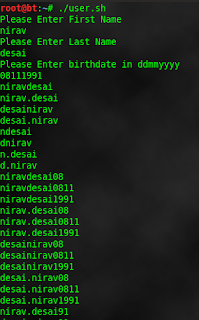
I also write bash script which generate possible username using first name, last name & birth date.
Creating Custom word list:-
(1)Cewl:-
Custom Word List generator. CeWL is a ruby app which spiders a given url to a specified depth, optionally following external links, and returns a list of words.
wyd is a password profiling tool that extracts words/strings from supplied files and directories. It parses files according to the file-types and extracts the useful information, e.g. song titles, authors and so on from mp3's or descriptions and titles from images.
(3)Cupp:-
People spend a lot of time preparing for effective dictionary attack. Common User Passwords Profiler (CUPP) is made to simplify this attack method that is often used as last resort in penetration testing and forensic crime investigations. A weak password might be very short or only use alphanumeric characters, making decryption simple. A weak password can also be one that is easily guessed by someone profiling the user, such as a birthday, nickname, address, name of a pet or relative, or a common word such as God, love, money or password.
https://tipstrickshack.blogspot.com/2013/12/creating-custom-username-list-wordlist.html
Published: 2013 12 18 08:34:00
Received: 2024 02 20 16:42:59
Feed: Hacking and Tricks
Source: Hacking and Tricks
Category: Cyber Security
Topic: Cyber Security
Views: 24