Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Microsoft chaos around the world
published on 2024-07-25 12:06:44 UTC by philvilesContent:
Microsoft suffered two outages last week; one relatively minor Azure outage affecting multiple components of the Office 365 suite, and another which caused worldwide IT problems triggered by a CrowdStrike update which caused the Blue Screen of Death upon start up.
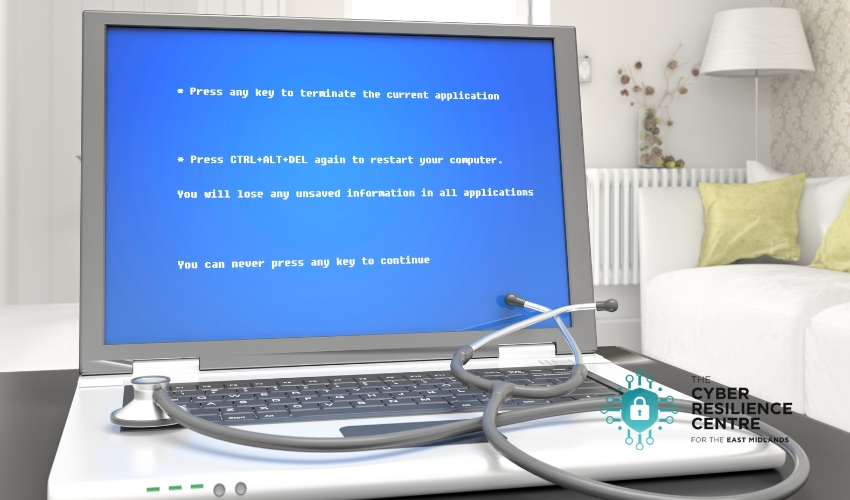
CrowdStrike pulled the guilty update within a few hours and Microsoft have provided a repair kit for affected customers, but this will likely take weeks to reverse the damage caused to millions of devices.
CrowdStrike have since promised to improve its software tests, and while there is no evidence that the CrowdStrike outage was caused by malicious activity, warnings of bad actors attempting to take advantage surfaced, with cyber security experts and agencies around the world warning people about a wave of opportunistic hacking attempts linked to the IT outage.
So what happened?
During the early hours of Friday, July 19, an update was distributed by cybersecurity company CrowdStrike to Windows systems around the world. Unfortunately, this update triggered a logic error affecting Windows 10 and 11 devices which resulted in Blue Screen of Death (BSOD) boot loops - devices entering BSOD mode on start-up.
In order to fix this, devices needed to be manually booted up in safe mode to bypass the loop, and the problematic file needed deleting in the registry settings, followed by a re-boot. This required a hands-on approach to mitigate, and a further problem was caused by the BitLocker system.
BitLocker, which encrypts and secures data on the device, needed to be unlocked but there are many instances where the BitLocker recovery key had been forgotten or misplaced. Without this key, chances are the device needed to be rebuilt from scratch.

In terms of impact, this affected almost every sector including emergency services, TV networks, retail, healthcare, finance, construction, education, IT and cyber services, travel, aviation and even the Mercedes Formula 1 team.
For devices, millions of them needed – or need to be - manually remediated which will likely take weeks if not months to reverse the damage. CrowdStrike pulled the file within a few hours, but the damage had likely already been done.
Threat actors were quick to react to this outage, setting up malicious domains and phishing campaigns using CrowdStrike or Microsoft fixes as the lure.
In some instances, threat actors have asked for funds to unlock systems, while other campaigns resulted in malware being downloaded from fake hotfixes and patches installing malware such as Remcos RAT, or distributing wiper malware.
This incident followed a relatively minor Microsoft Azure outage which affected multiple Azure services in the US, including Office 365 products such as PowerBI, Defender, OneDrive and SharePoint online.
Naturally, in the aftermath of these incidents, cyber researchers and IT professionals are questioning the increasing ubiquitous nature of Microsoft software and products within organisations; companies are heavily dependent on their software for various IT needs.
It is important to consider whether companies should contemplate diversifying their software and infrastructure to mitigate potential risks and dependencies on a single provider.
Reporting
Report all Fraud and Cybercrime to Action Fraud by calling 0300 123 2040 or online. Forward suspicious emails to report@phishing.gov.uk. Report SMS scams by forwarding the original message to 7726 (spells SPAM on the keypad).
https://www.emcrc.co.uk/post/microsoft-chaos-around-the-world
Published: 2024 07 25 12:06:44
Received: 2024 07 25 12:22:07
Feed: The Cyber Resilience Centre for the East Midlands
Source: National Cyber Resilience Centre Group
Category: News
Topic: Cyber Security
Views: 16
