Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.What is a DDoS Attack?
published on 2024-08-08 07:00:00 UTC by Simon BurgeContent:
Cyber threats are a significant concern for individuals, businesses, and governments alike.
The increasing reliance on internet-based services and the interconnectedness of systems have made cybersecurity a critical issue.
Among the various types of cyber threats, one of the most disruptive is a Distributed Denial of Service (DDoS) attack.
DDoS attacks can cripple websites, disrupt online services, and cause substantial financial and reputational damage.
This article will explain what a DDoS attack is, how it works, the different types of DDoS attacks, notable examples from recent history, and effective measures to protect against such attacks.
By gaining a deeper insight into DDoS attacks, we can better prepare and defend against these formidable cyber threats.
What is a DDoS Attack?

A DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic.
The goal of a DDoS attack is to make the targeted website or service unavailable to its intended users.
By sending an enormous amount of requests simultaneously, the attack exhausts the target’s resources, causing slow performance or complete shutdown.
Unlike a simple Denial of Service (DoS) attack, which originates from a single source, a DDoS attack leverages multiple sources, making it much harder to defend against.
DDoS attacks can target various layers of a service, including the network, transport, and application layers.
They are a significant threat to businesses, governments, and individuals, often resulting in significant financial losses, reputational damage, and operational downtime.
How Does a DDoS Attack Work?
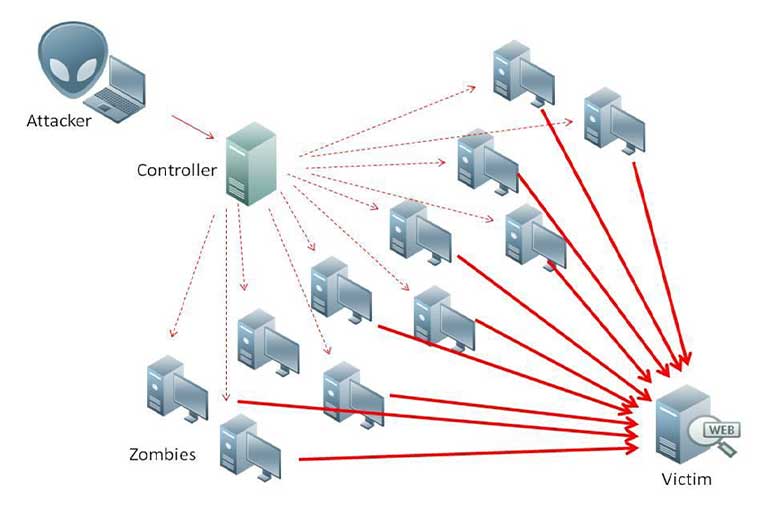
A DDoS attack operates by inundating a target server, service, or network with an overwhelming volume of traffic, rendering it incapable of functioning properly.
Here’s how it works:
Botnet Formation
Compromised Devices
The attacker gains control over a large number of devices, such as computers, smartphones, IoT devices, and servers, by infecting them with malware.
These compromised devices become part of a botnet, obediently following the attacker’s commands.
Coordination
The attacker orchestrates the botnet, instructing the compromised devices to send traffic to the target.
This coordination is typically done through command and control (C&C) infrastructure, which allows the attacker to remotely control the botnet.
Traffic Flood
Inundation
Once the botnet is ready, the attacker initiates the attack by directing all the compromised devices to flood the target with traffic.
This flood can consist of various types of data packets, such as TCP, UDP, ICMP, or HTTP requests, depending on the type of DDoS attack.
Overwhelm Resources
The massive influx of traffic overwhelms the target’s resources, including bandwidth, processing power, memory, and network connections.
As a result, legitimate users are unable to access the target’s services or experience severe performance degradation.
Persistence and Variation
Persistence
DDoS attacks can be sustained for extended periods, ranging from minutes to days, depending on the attacker’s objectives and resources.
Variation
Attackers may vary the attack vectors, targets, and intensities to evade detection and mitigation efforts.
They can also launch multiple simultaneous attacks against different targets, complicating defence strategies.
Concealment
Attackers often employ techniques to conceal the origins of the attack, such as spoofing IP addresses or leveraging anonymization services, making it difficult to trace the source of the malicious traffic.
What are the Different Types of DDoS Attacks?

Distributed Denial of Service (DDoS) attacks come in various forms, each targeting different aspects of a network or service.
Here are some of the most common types:
Volume-Based Attacks
UDP Flood
This attack floods the target with User Datagram Protocol (UDP) packets, overwhelming its bandwidth.
Since UDP is connectionless, the attacker can spoof the source IP addresses, making it difficult to trace the origin of the attack.
ICMP Flood
In this attack, the attacker sends a large number of Internet Control Message Protocol (ICMP) echo request packets to the target, causing it to become unreachable by flooding it with echo replies.
Ping Flood
Similar to ICMP floods, this attack sends a large number of ping requests to the target, consuming its resources and causing network congestion.
Protocol-Based Attacks
SYN Flood
This attack exploits the TCP three-way handshake process by flooding the target with a large number of SYN requests, overwhelming its capacity to establish legitimate connections and leading to service disruption.
ACK Flood
In an ACK flood attack, the attacker sends a flood of TCP ACK packets to the target, causing it to expend resources processing the acknowledgments and slowing down legitimate traffic.
Application Layer Attacks
HTTP Flood
This attack targets web servers by sending a large number of HTTP requests, exhausting server resources such as CPU and memory and causing the website to become unresponsive.
Slowloris Attack
In a Slowloris attack, the attacker sends HTTP headers to the target server at a slow pace, gradually consuming all available connections, effectively preventing legitimate users from accessing the server.
Hybrid Attacks
DNS Amplification
This attack leverages vulnerable DNS servers to amplify the volume of traffic sent to the target, making it more challenging to mitigate and causing significant service disruption.
NTP Amplification
Similar to DNS amplification, this attack exploits vulnerable Network Time Protocol (NTP) servers to amplify the volume of traffic directed at the target, overwhelming its resources and causing downtime.
Famous Examples of DDoS Attacks

Several notable Distributed Denial of Service (DDoS) attacks have made headlines over the years, demonstrating the devastating impact these attacks can have on businesses, governments, and internet infrastructure.
Here are some famous examples:
GitHub (2018)
In February 2018, GitHub experienced one of the largest DDoS attacks ever recorded.
The attack peaked at 1.3 terabits per second (Tbps) of traffic, making it the most massive DDoS attack at the time.
The attack exploited vulnerable servers to amplify the volume of traffic directed at GitHub’s servers, causing intermittent outages and disruptions to its services.
Dyn (2016)
In October 2016, a series of massive DDoS attacks targeted Dyn, a major Domain Name System (DNS) provider.
The attacks disrupted access to several high-profile websites, including Twitter, Netflix, Reddit, and PayPal.
The attackers utilised a botnet composed of compromised Internet of Things (IoT) devices, such as webcams and routers, to launch the attacks.
The incident highlighted the vulnerability of critical internet infrastructure to DDoS attacks and underscored the importance of securing IoT devices.
ProtonMail (2015)
In November 2015, ProtonMail was targeted by a powerful DDoS attack.
The attack, which peaked at 500 Gbps, was one of the largest DDoS attacks at the time.
The attackers demanded a ransom payment in exchange for ending the attack.
ProtonMail refused to pay the ransom and instead collaborated with other security organisations to mitigate the attack and restore its services.
Estonia (2007)
In April 2007, Estonia experienced a series of crippling DDoS attacks targeting its government, media, and banking websites.
The attacks coincided with a diplomatic dispute between Estonia and Russia, leading to speculation that the attacks were politically motivated.
The incident raised awareness of the potential for DDoS attacks to disrupt entire countries’ digital infrastructure and sparked discussions about cybersecurity and international relations.
How to Protect Yourself from a DDoS Attack?

Protecting against DDoS attacks requires a combination of proactive measures and robust cybersecurity strategies.
Here are some effective ways to defend against DDoS attacks:
DDoS Protection Services
Consider subscribing to DDoS protection services offered by reputable cybersecurity firms.
These services can detect and mitigate DDoS attacks in real-time, ensuring that your network and services remain accessible during an attack.
Cloud-based Solutions
Utilise cloud-based DDoS mitigation solutions that can absorb and filter malicious traffic before it reaches your network.
Cloud providers have the infrastructure and expertise to handle large-scale attacks effectively.
Bandwidth Scalability
Ensure that your network infrastructure has sufficient bandwidth to handle sudden surges in traffic.
Scalable bandwidth allows your network to absorb DDoS attacks more effectively.
Redundancy and Failover Mechanisms
Implement redundancy and failover mechanisms to distribute traffic across multiple servers or data centres.
This redundancy can help mitigate the impact of DDoS attacks by spreading the load and maintaining service availability.
Firewalls and Intrusion Prevention Systems (IPS)
Deploy firewalls and IPS solutions to filter out malicious traffic and block DDoS attack vectors.
Configure these security devices to detect and mitigate DDoS attacks proactively.
Update Security Policies
Regularly update and enforce security policies to mitigate the risk of DDoS attacks.
Implement measures such as rate limiting, traffic filtering, and access control lists to prevent unauthorised access and abuse.
Network Traffic Monitoring
Monitor network traffic patterns and behaviour to detect signs of a potential DDoS attack.
Use network monitoring tools and anomaly detection systems to identify abnormal traffic spikes and take appropriate action.
Incident Response Plan
Develop and regularly test an incident response plan specifically tailored to DDoS attacks.
Ensure that your team knows how to respond effectively during an attack, including activating mitigation measures and communicating with stakeholders.
User Awareness Training
Educate employees and users about the risks of DDoS attacks and how to recognize and report suspicious activity.
Promote cybersecurity best practices, such as using strong passwords, updating software regularly, and avoiding clicking on suspicious links or attachments.
Conclusion
Hopefully you now understand what a DDoS attack is, different types, and how to prevent them.
Distributed Denial of Service attacks pose a significant threat in today’s interconnected digital landscape.
These malicious attacks have the potential to disrupt services, leading to downtime, financial losses, and reputational damage for businesses, governments, and individuals alike.
However, by gaining a deeper understanding of how DDoS attacks work and implementing effective protective measures, organisations can mitigate the risk and impact of such attacks.
It is essential for businesses to invest in robust cybersecurity solutions, such as DDoS protection services and network infrastructure enhancements, to detect and mitigate attacks in real-time.
By adopting a proactive approach to cybersecurity and implementing best practices, organisations can minimise their vulnerability to DDoS attacks and ensure the continuity and reliability of their digital services.
https://securityjournaluk.com/ddos-attack/
Published: 2024 08 08 07:00:00
Received: 2024 08 08 07:03:07
Feed: Security Journal UK
Source: Security Journal UK
Category: Security
Topic: Security
Views: 1
