Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Every Doggo Has Its Day: Unleashing the Xiū Gǒu Phishing Kit
published on 2024-10-30 20:52:41 UTC by Dal BillingsContent:
Key data
This article explores Netcraft’s research into Xiū gǒu (修狗), a phishing kit in use since at least September 2024 to deploy phishing campaigns targeting the US and UK, Spain, Australia, and Japan. Insights include:
- A branded mascot and interactive features added for entertainment
- Over 2,000 phishing websites identified using the kit
- Campaigns targeting the countries around the globe
- Organizations being targeted across the public sector, postal, digital services, and banking sectors
Doggo Background
Netcraft has observed a phishing kit being used in campaigns targeting the US, UK, Spain, Australia, and Japan since September 2024. Over 1,500 related IP addresses and phishing domains have been identified, targeting victims with fake charges related to motorists, government payments, and postal scams. Threat actors using the kit to deploy phishing websites often rely on Cloudflare’s anti-bot and hosting obfuscation capabilities to prevent detection. This research builds on existing intelligence shared in September by security researchers BushidoUK and Fox_threatintel.
“Doggo”
The kit, which uses Mandarin Chinese throughout, provides users with an admin panel (exposed at the /admin path) to configure and manage phishing campaigns. The word “xiū gǒu”, which is referenced in the kit source code, is derived from the admin panel title “xiū gǒu yuánmǎ” (修狗源码). Xiū gǒu roughly translates from Mandarin Chinese internet slang as “doggo” (small dog) and xiū gǒu yuánmǎ as “doggo source code”. This “doggo” concept comes to life as the avatar for the kit’s admin panel and Telegram account—a cartoon dog holding a bottle of soda. “Easter egg” functionality has been developed in the admin panel, allowing users to transform this mascot into a “thug life” version by clicking the avatar.
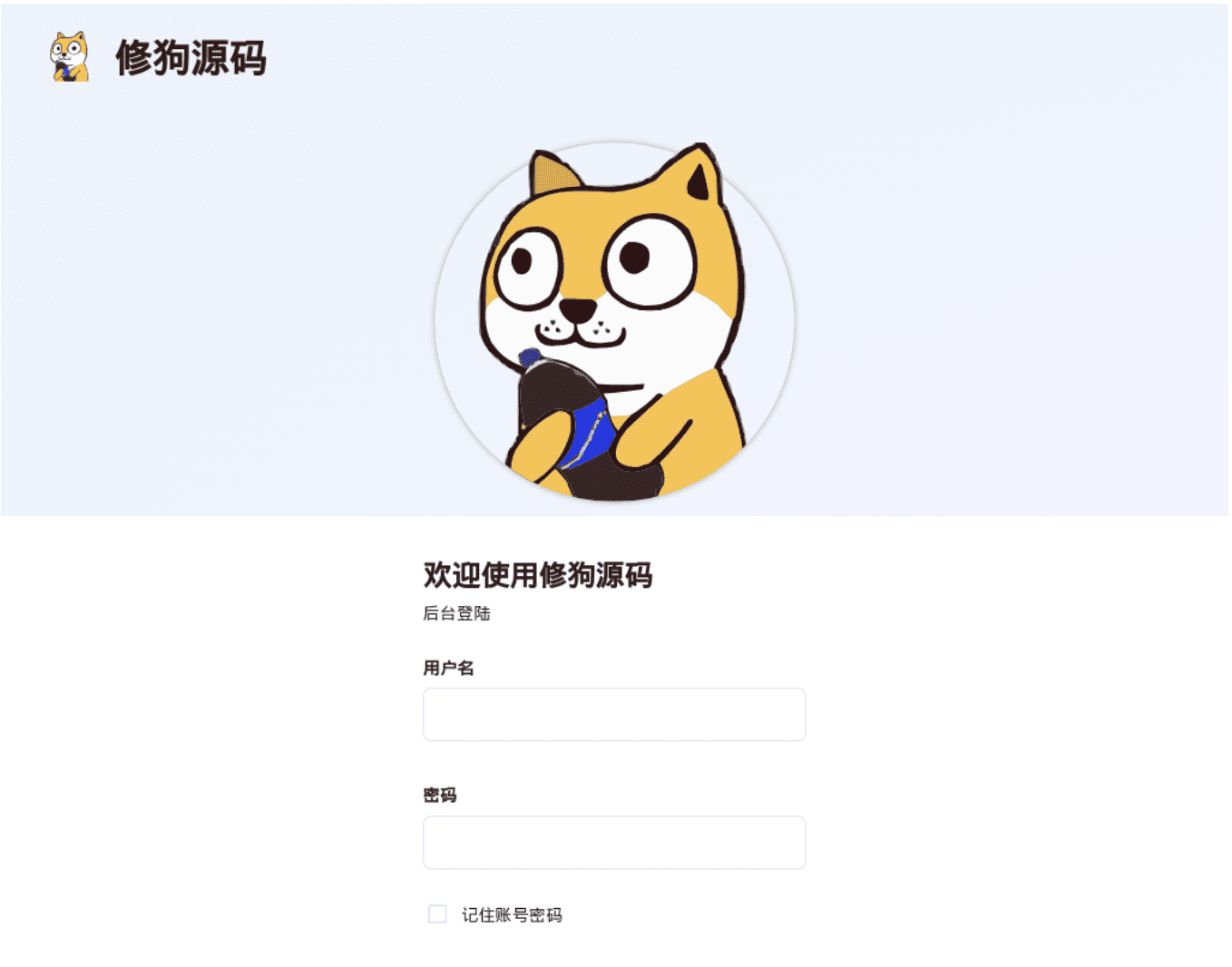
Figure 1. Admin Panel Login with “Doggo” mascot
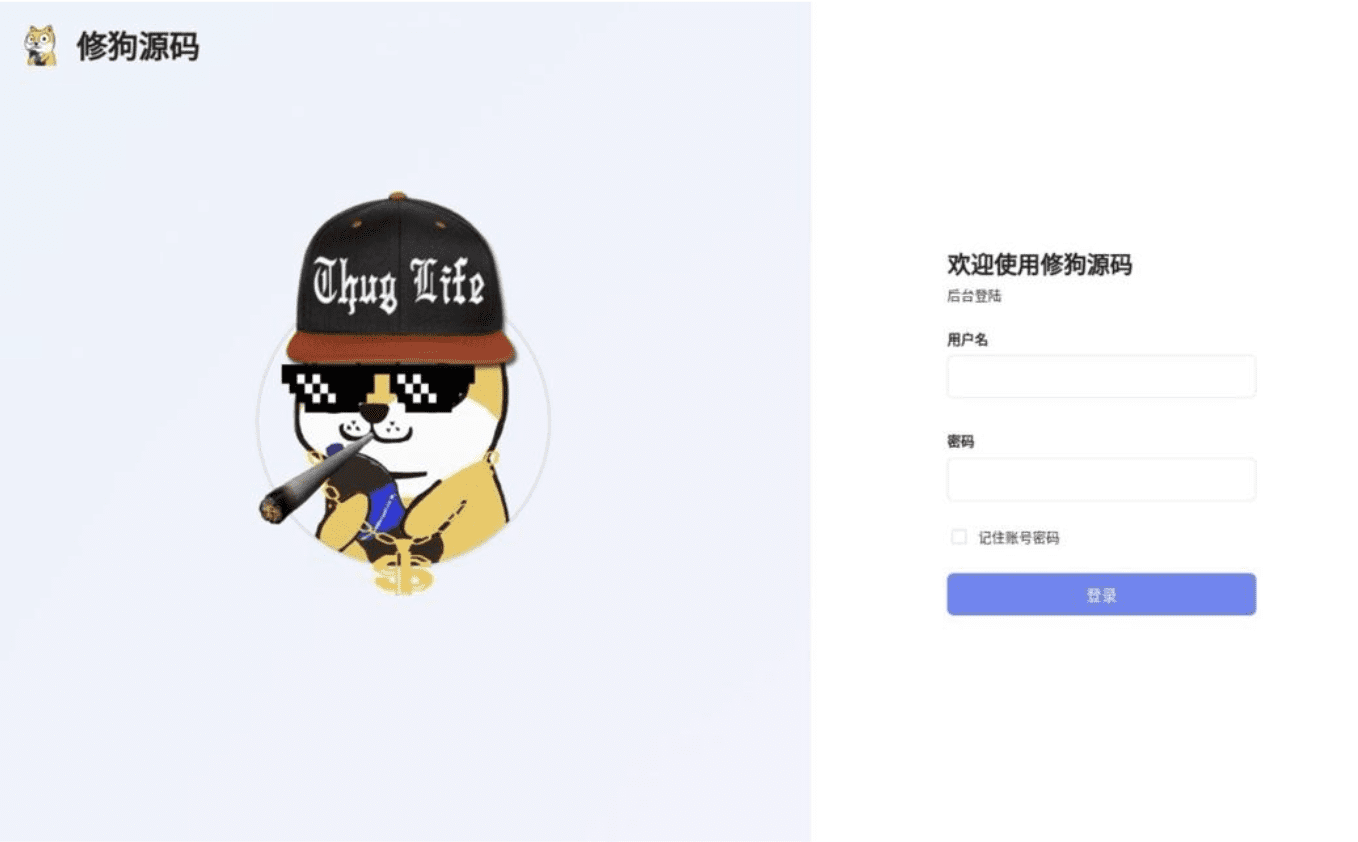
Figure 2. Admin panel with alternative easter egg “doggo”
Key Characteristics
Netcraft observed the following characteristics:
They also often use the “.top” top level domain (TLD) and typically register domains related to the nature of their scam, e.g., including the words ‘parking’ or ‘living’, or by including part of the phishing target name.
- Xiū gǒu is developed using a modern tech stack, as opposed to the more traditional PHP phishing kits, including:
- Vue.js is used in the front end for both the phishing pages and admin panel
- A Golang back-end, provided through the executable SynPhishServer, which appears to be based on go-gin-api
- The kit comes equipped with Telegram bots to exfiltrate credentials, ensuring that threat actors can maintain access to data even if their phishing site is taken down
- Threat actors using the kit use Rich Communications Services (RCS) rather than SMS to send lure messages
- They also often use the “.top” top-level domain (TLD) and typically register domains related to the nature of their scam, e.g., including the words ‘parking’ or ‘living’, or by including part of the phishing target name
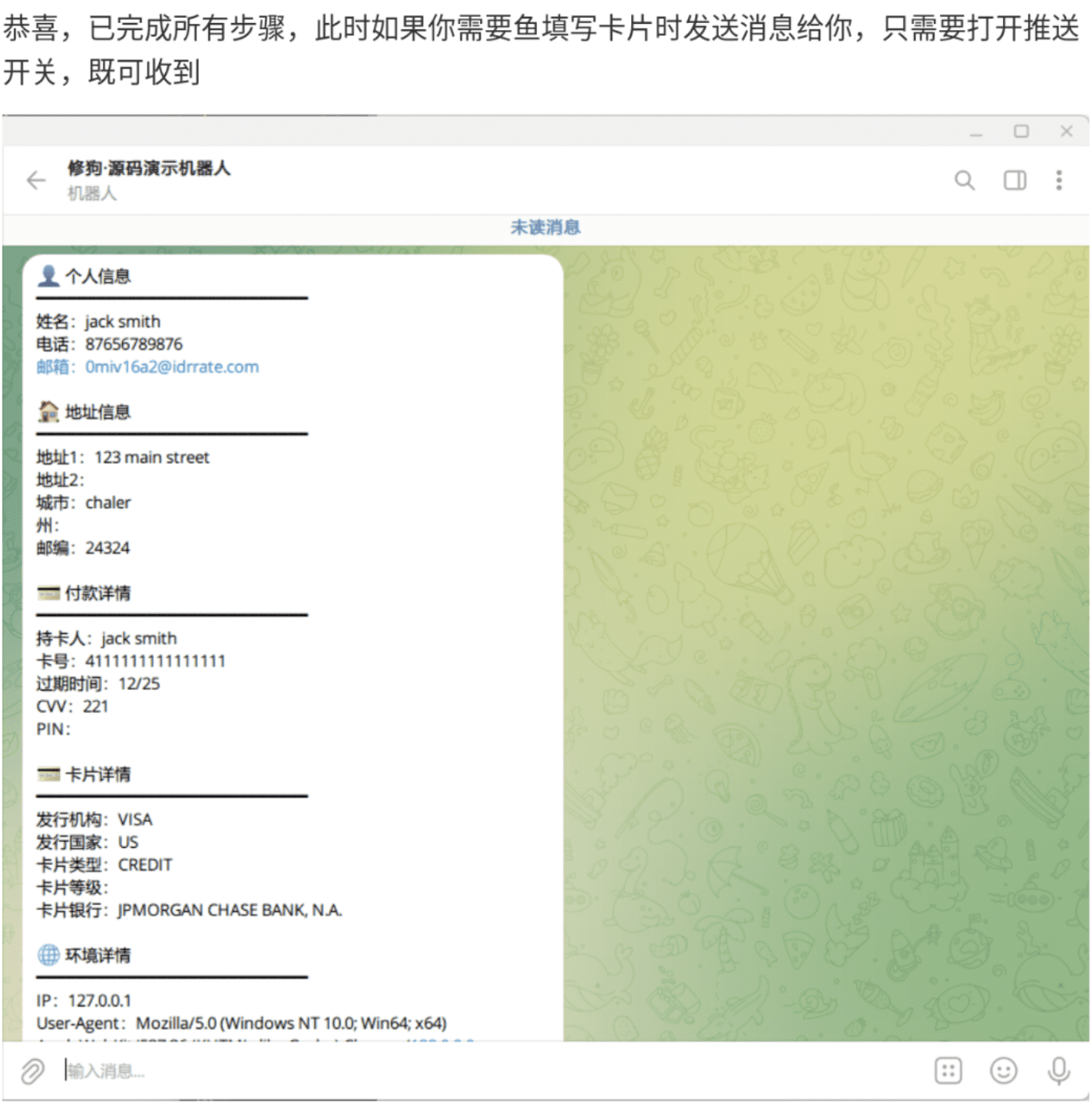
Fig. 3. Xiū gǒu Telegram message containing (dummy) victim information and stolen card details
The kit’s author appears to own the domain xiugou.icu, which provides images in the kits. These enable the author to see where their kits are installed by analyzing referrer headers.
Various subdomains, such as those in the bullets below, suggest the author creates separate sites to perform different functions, such as:
- test1234[.]xiugou[.]icu
- usps0007[.]xiugou[.]icu
- store[.]xiugou[.]icu
- ai[.]xiugou[.]icu (currently live and hosting the open source ai chat framework lobe-chat)
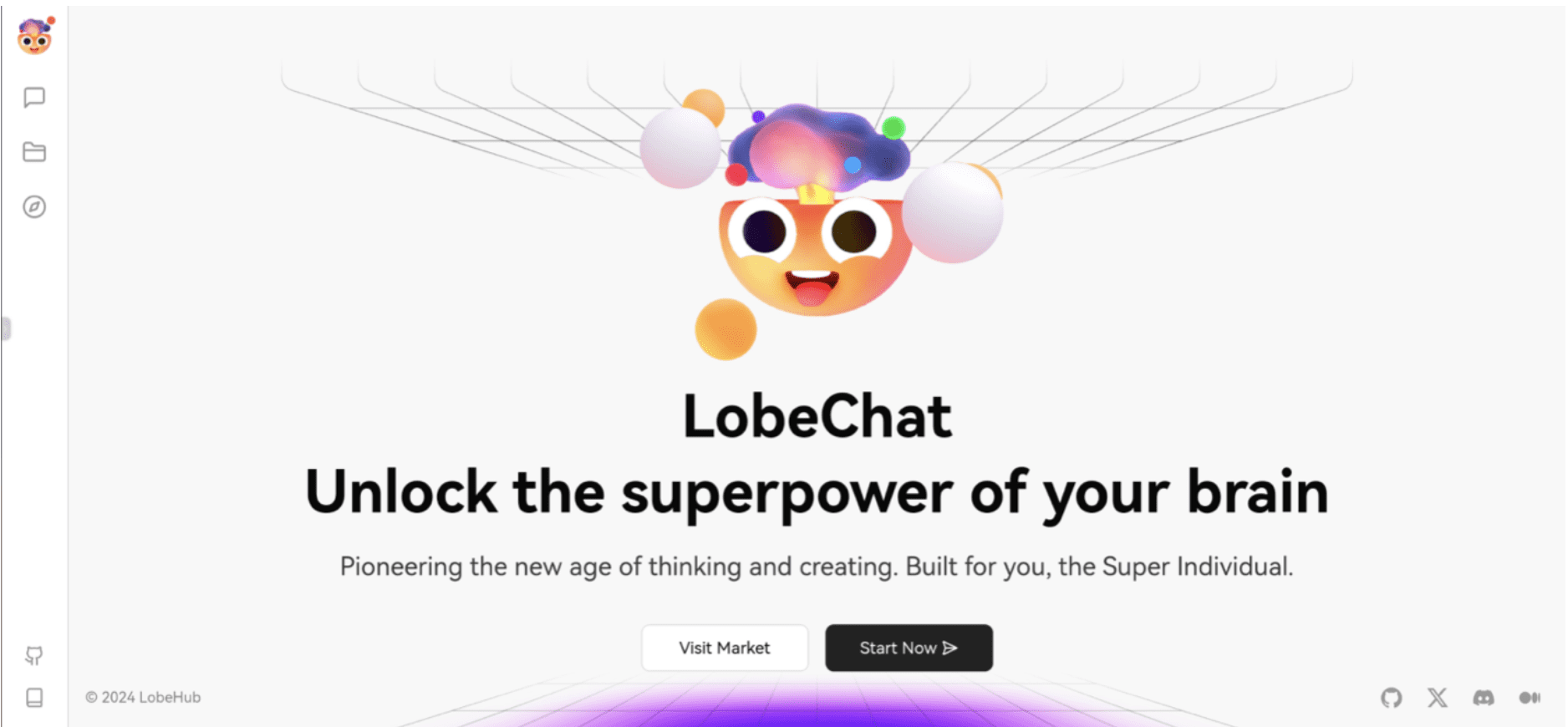
Fig. 4. LobeChat website
Who is being targeted?
Xiū gǒu is being used to impersonate brands across various verticals, including the public sector, postal, banking, and digital services. The scams typically manipulate victims into providing their personal details and making payments, for example, to release a parcel or fulfill a fine.
Some of those being impersonated include the USPS, UK Government (e.g., gov.uk and DVSA), Services Australia, Evri, Lloyds, New Zealand Post, and Linkt.
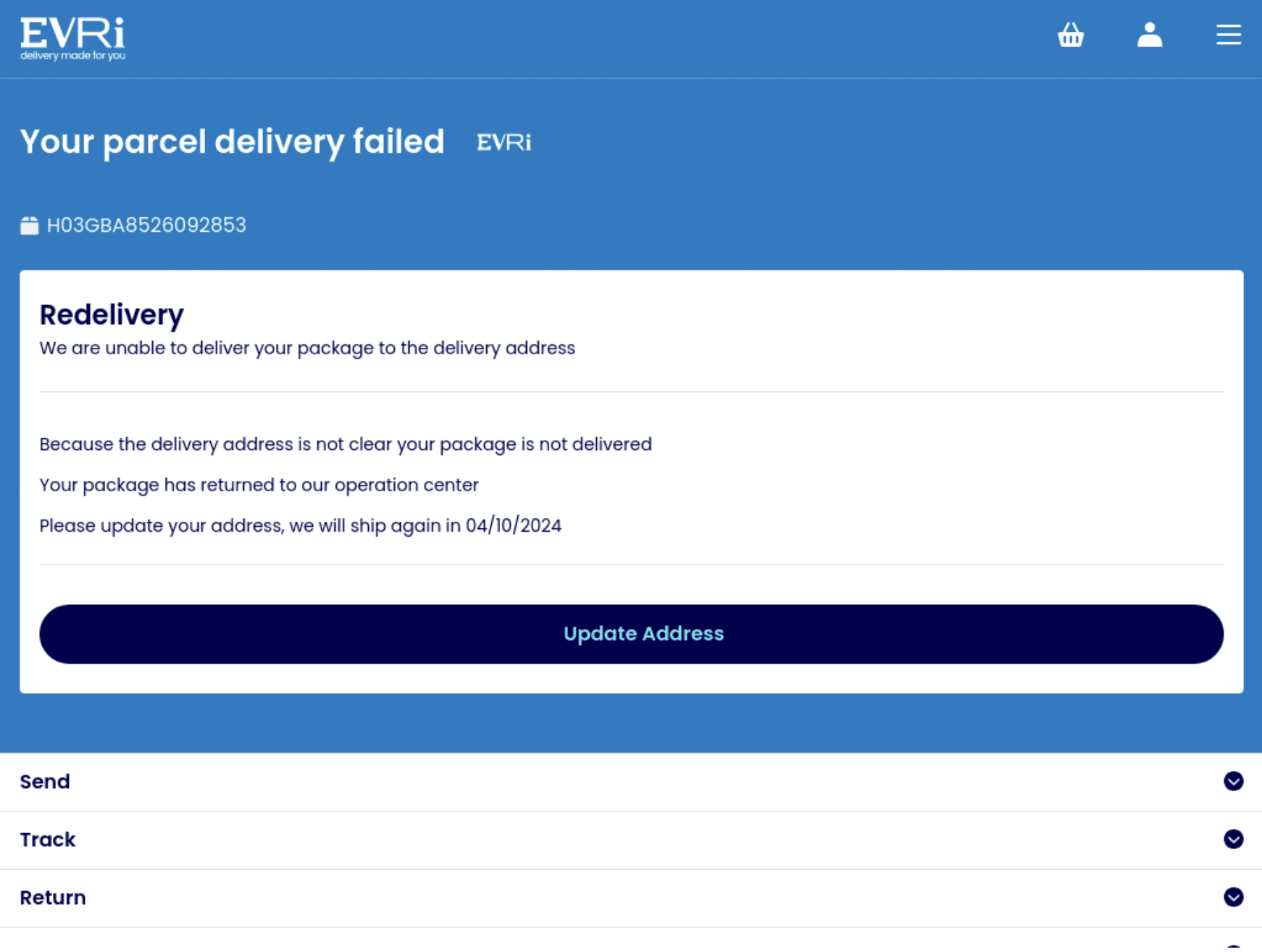
Fig. 5. Fake Evri parcel release page
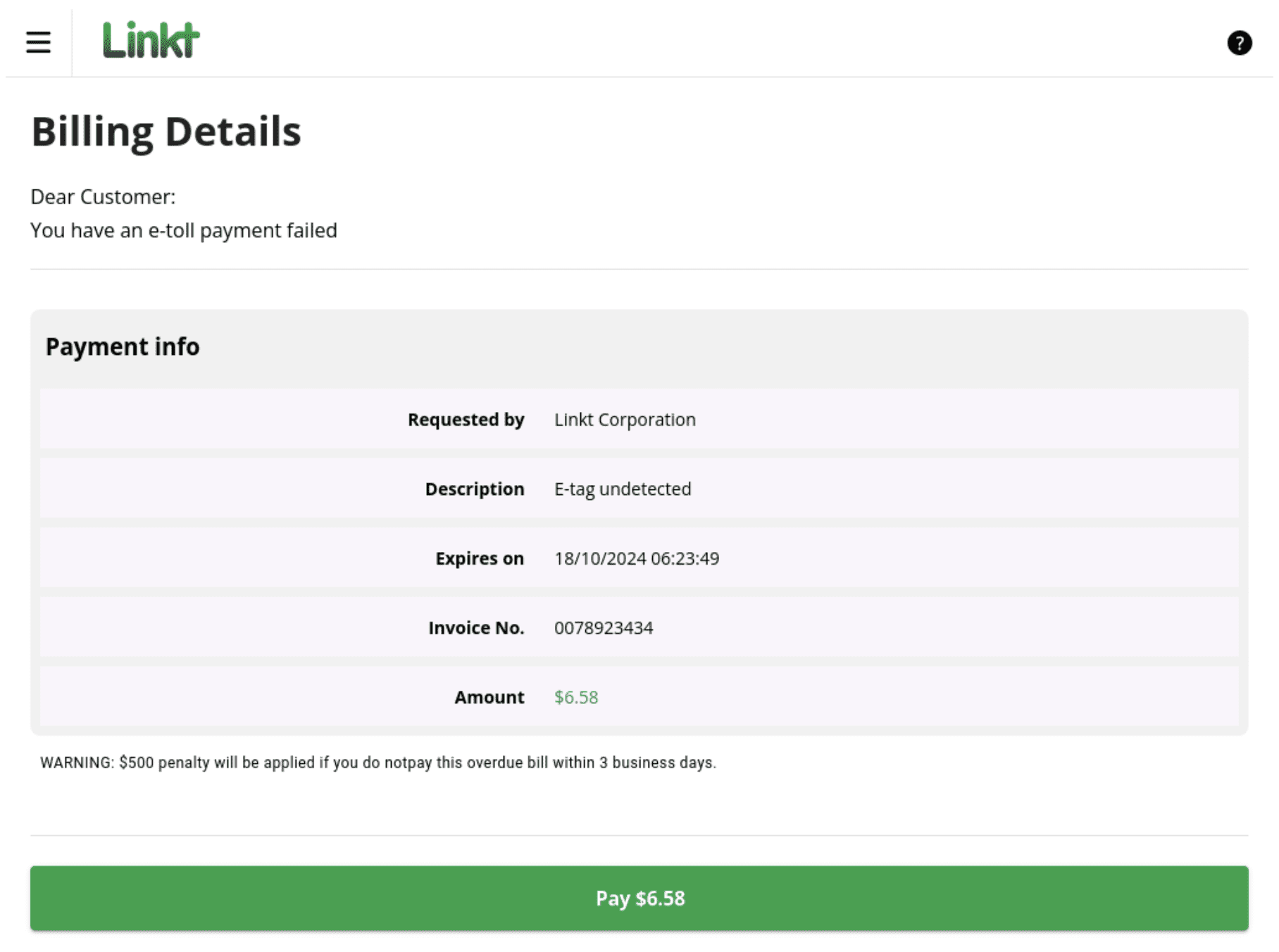
Fig. 6. Fake Linkt payment page
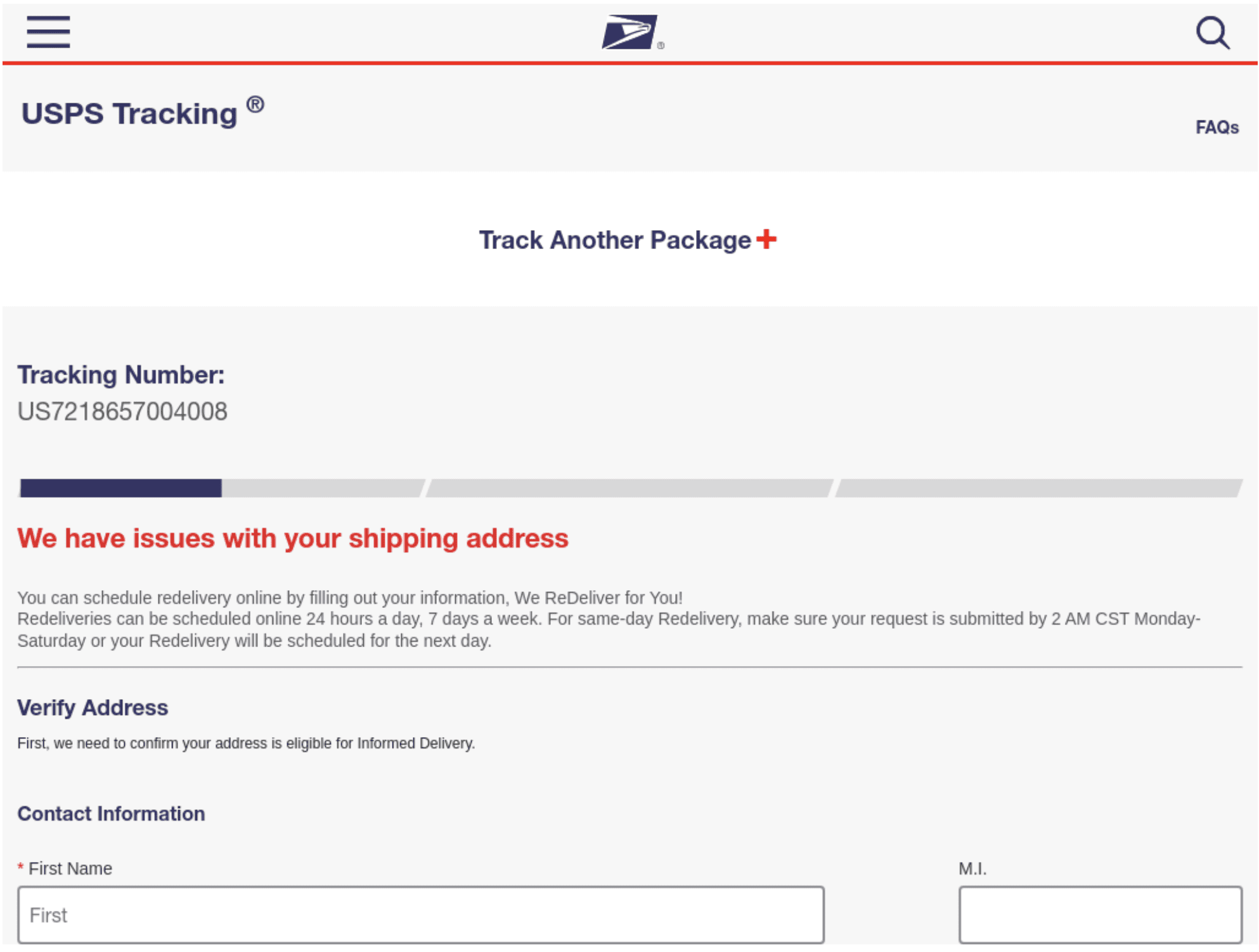
Fig. 7. Fake USPS package release page
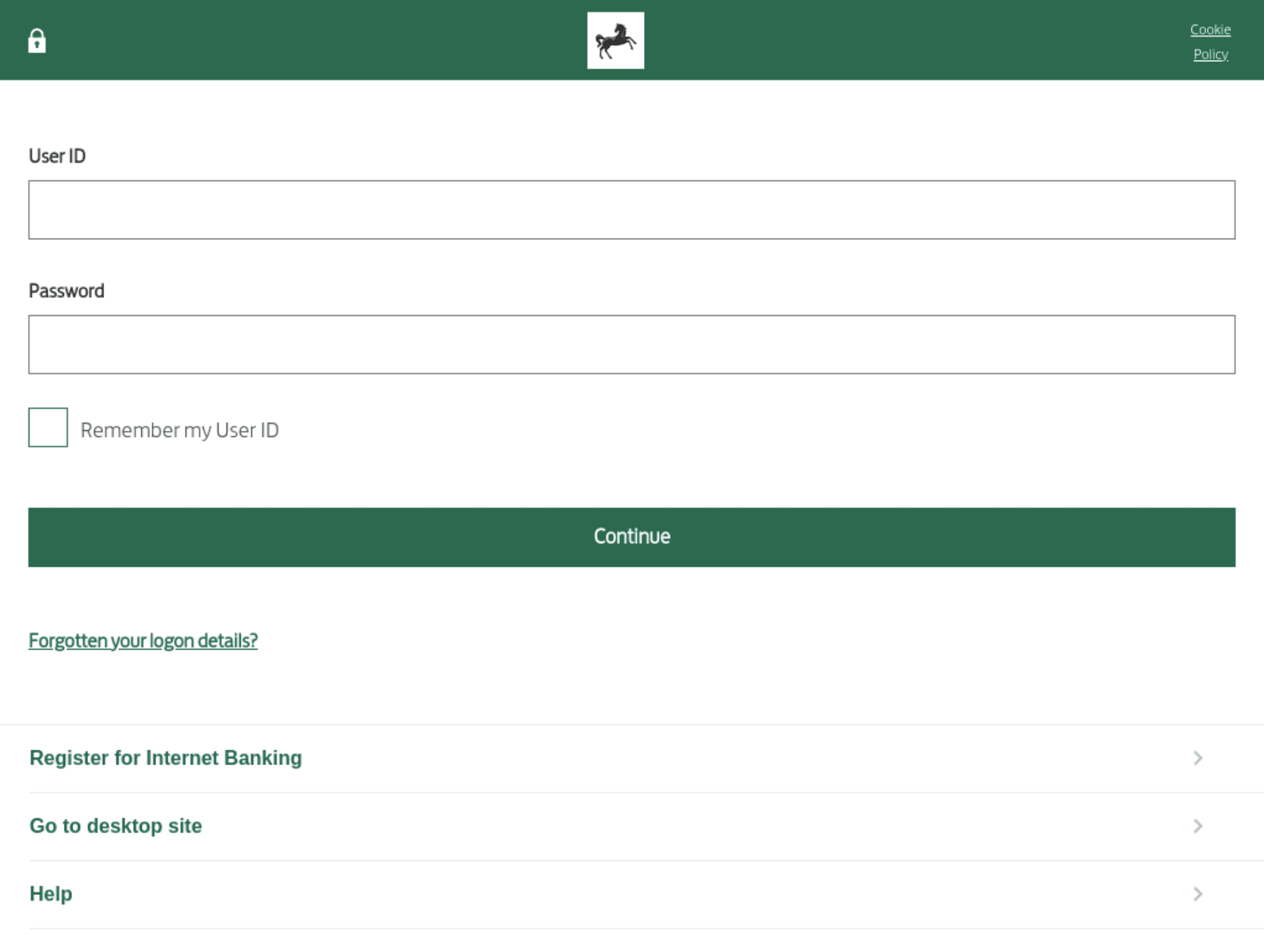
Fig. 8. Fake Lloyd’s Bank login form
Xiū gǒu attack flow
Netcraft has documented the end-to-end xiū gǒu attack flow, showing how threat actors use the kit to deploy phishing campaigns. The example below shows an impersonation of gov.uk (the UK government’s main website).
- RCS message is sent to the victim containing a shortened link; this link often includes a tracking parameter
- Victim clicks link
- Victim is sent to a phishing website styled to look exactly like gov.uk
- Note: Bots, such as those used for attack detection, are directed to legitimate, non-malicious sites to obfuscate activity
- Victim enters their personal data and payment details
- Victim’s details (including their IP address and browser characteristics) are exfiltrated to Telegram via a bot set up by the fraudster running the phishing website
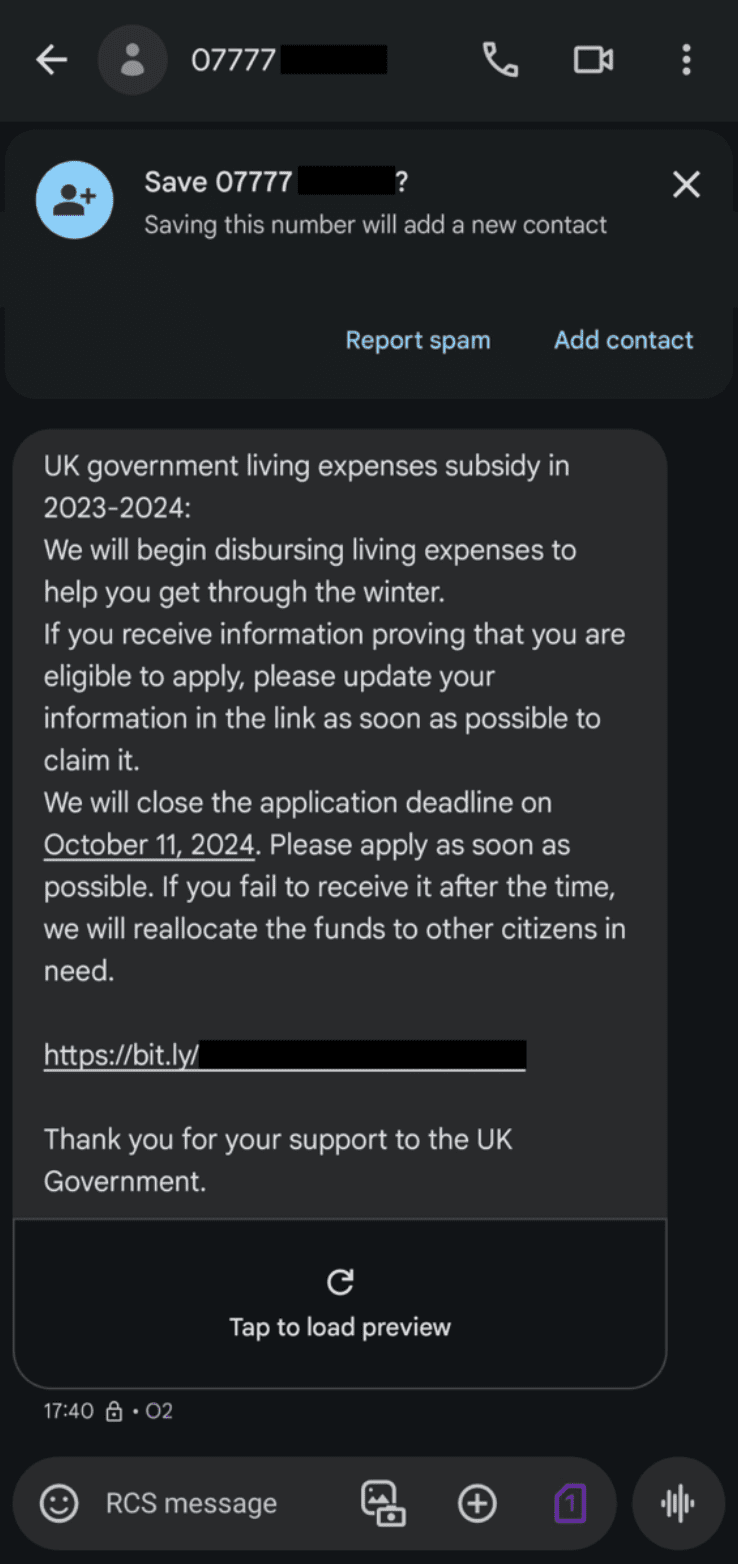
Fig. 9. RCS lure message targeting victims with communications regarding cost of living payments
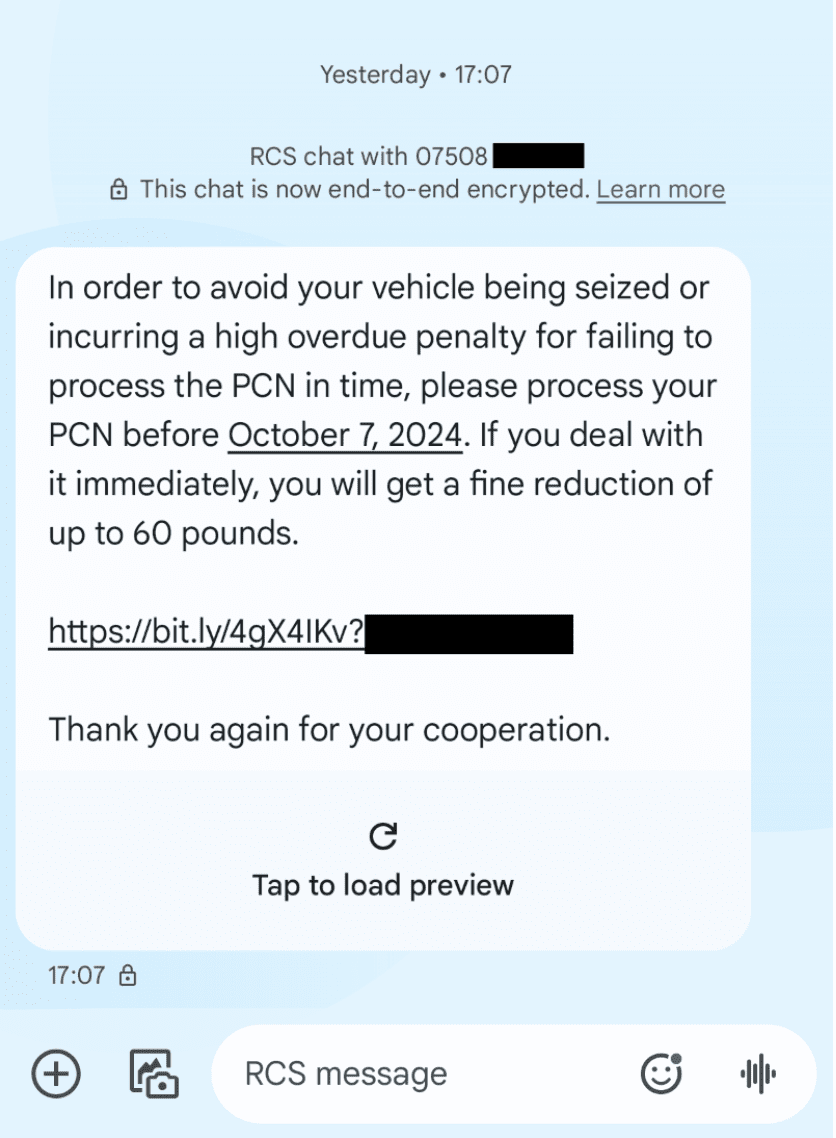
Fig. 10. RCS lure message targeting victims with communications regarding a fake penalty charge notice (PCN)tims with communications regarding cost of living payments
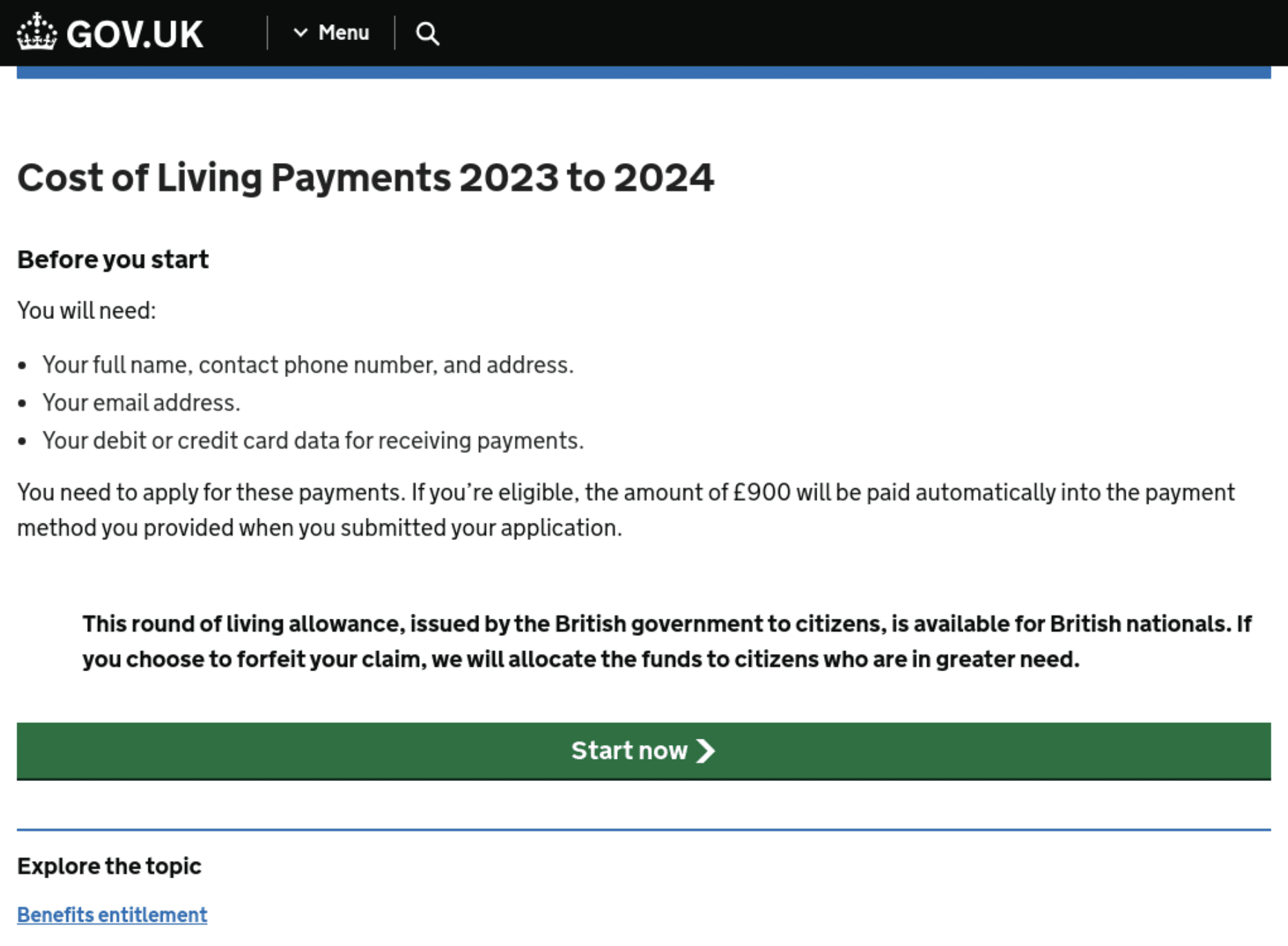
Fig. 11. Phishing website for cost of living payments, mimicking gov.uk (where there is no such page)
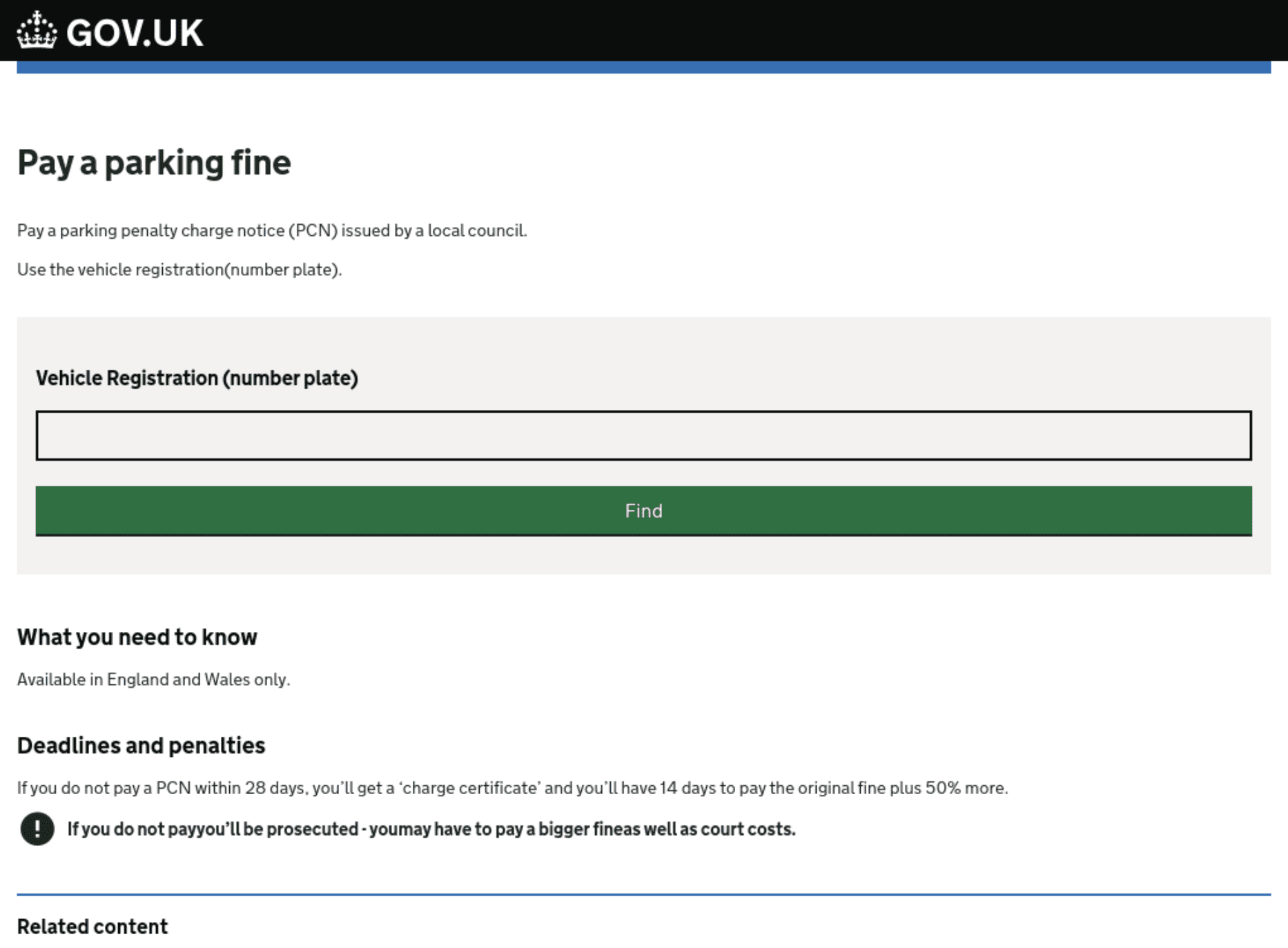
Fig. 12. Phishing website mimicking the gov.uk page for PCNs
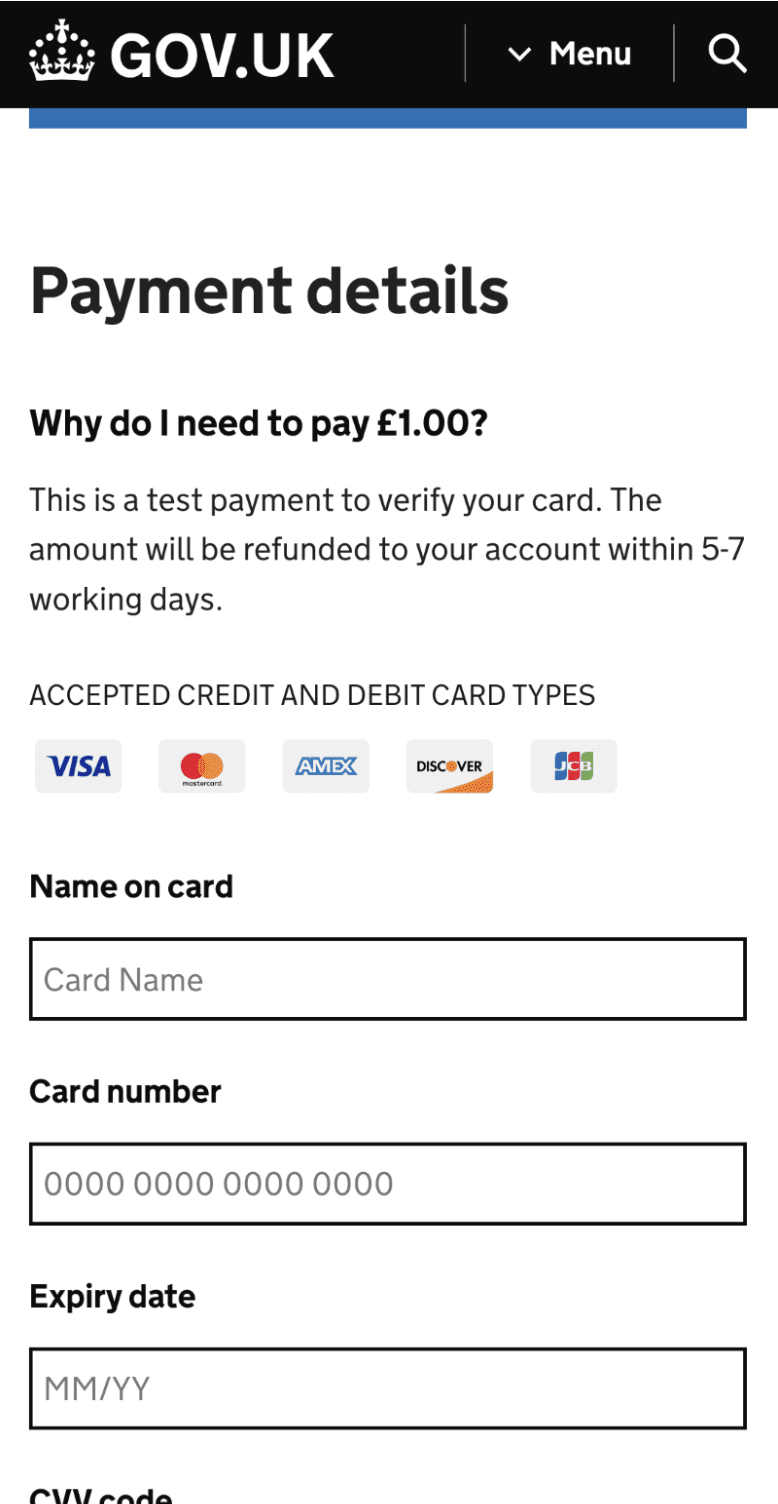
Fig. 13. Fake form mimicking gov.uk to extract victim payment details
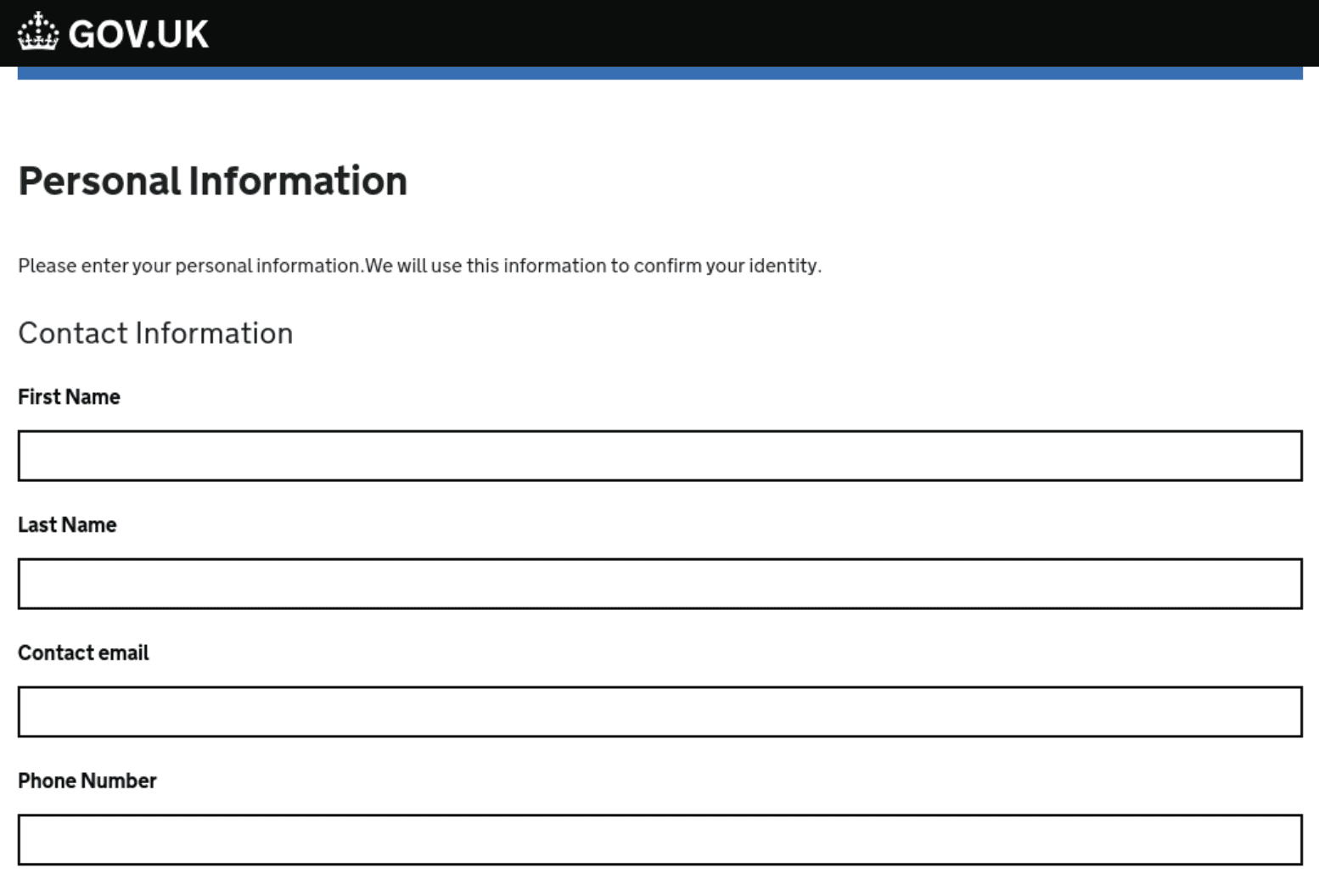
Fig. 14. Fake form mimicking gov.uk to extract victim’s personal information

Fig. 15. Fake PCN form mimicking gov.uk
By observing the full list of domains using xiū gǒu, we’ve identified threat actors targeting UK victims specifically. At least eight variations of the domain “yingguo[.]top” have been logged—Yingguo translating to “United Kingdom”—in addition to 18+ of the domain “f^¢kgb[.]top”.
Telegram bot scam
Netcraft gained access to a xiū gǒu tutorial, which shows users how to prepare a Telegram bot for data exfiltration. This includes a step-by-step flow via xiugou_example_bot, illustrated in the screenshots below.
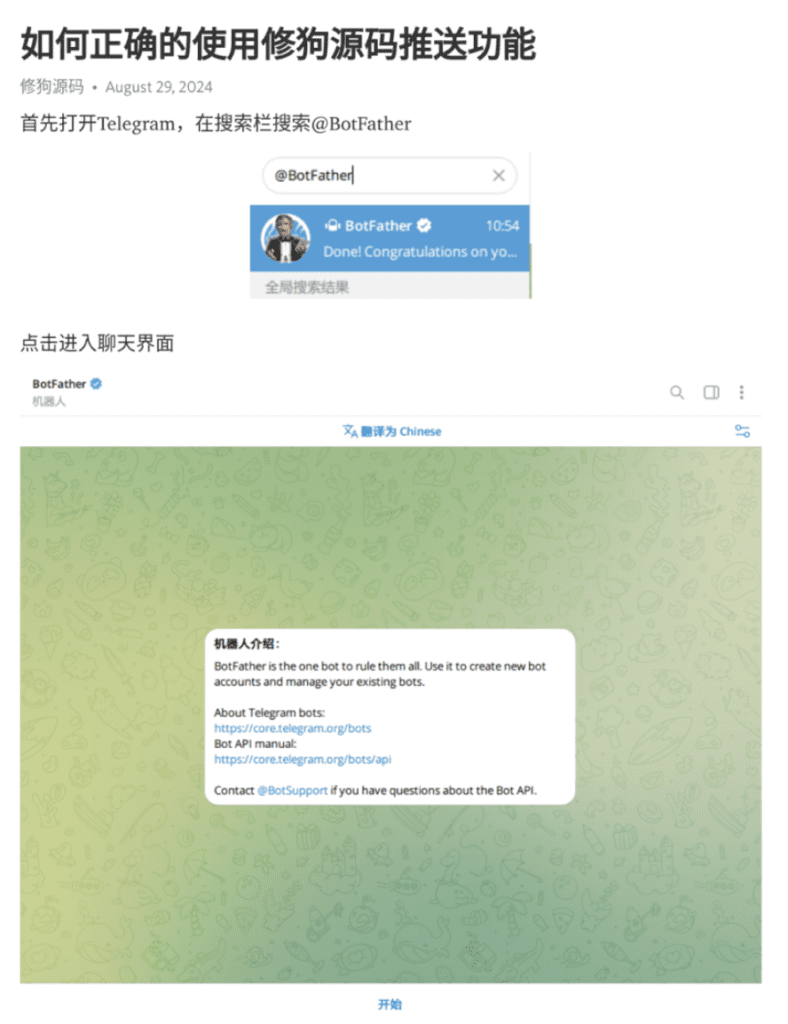
Fig. 16.
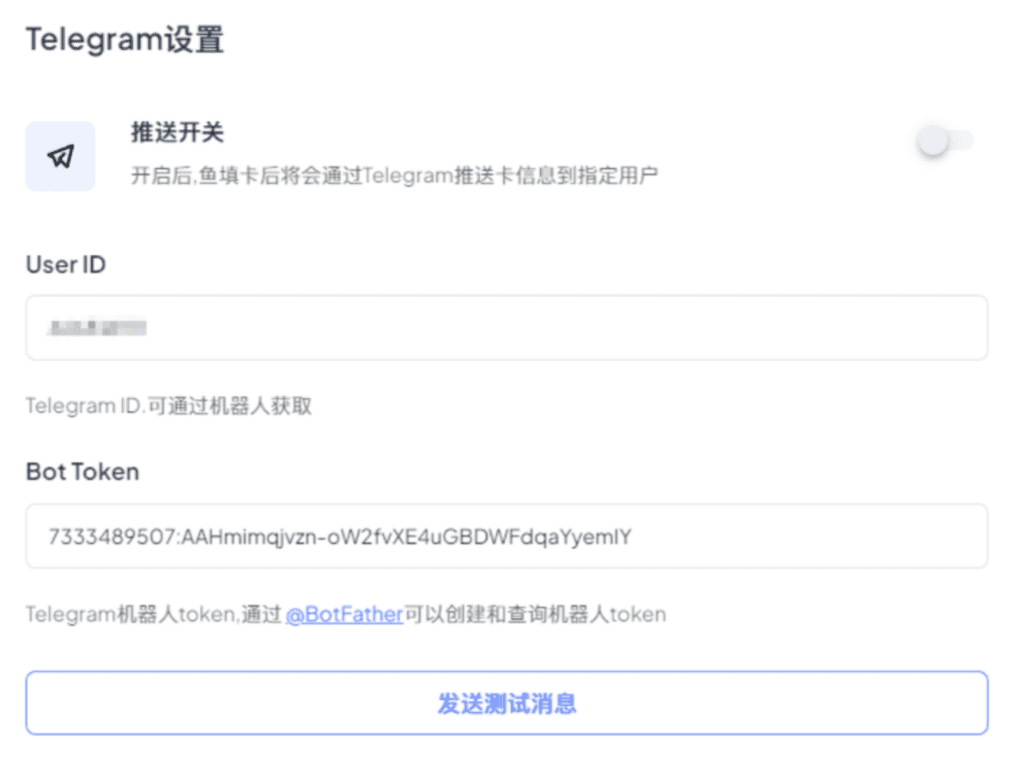
Fig. 17.
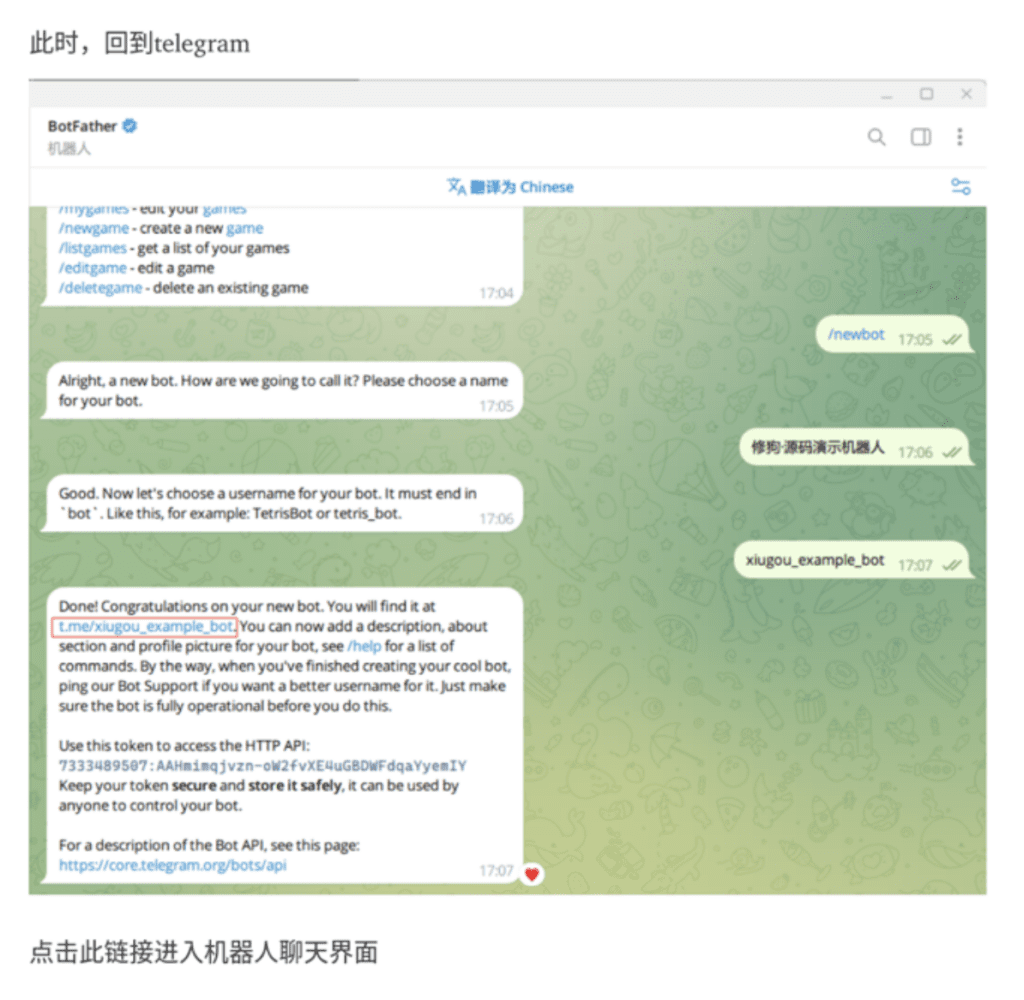
Fig. 18.
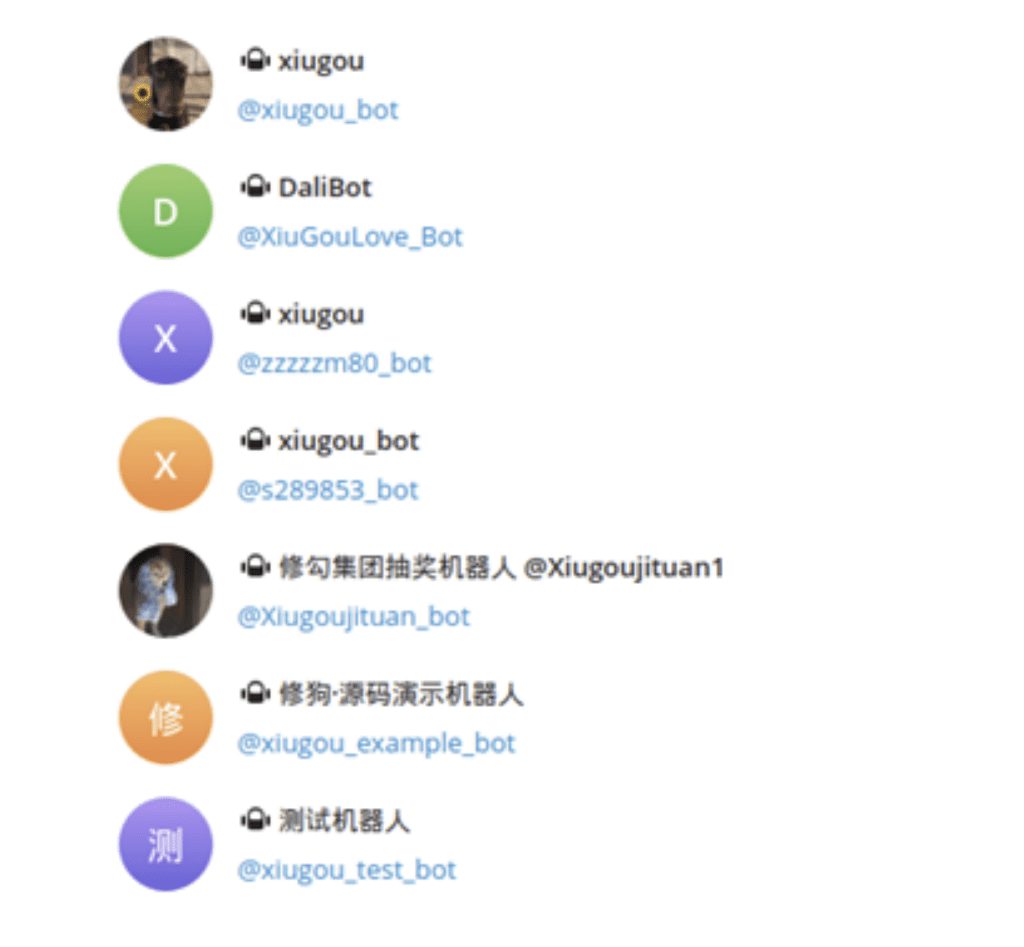
Fig. 19.
Fig. 16 – 19: Step-by-step tutorial for setting up Telegram bot for data exfiltration
Conclusion
The findings from our research into the xiū gǒu phishing kit provide an interesting perspective into the minds and methods of the authors behind the kits. User experience is key, as we can see by xiū gǒu’s use of specific scripting languages as well as the inclusion of user tutorials. The author has also chosen to measure and analyze the use of their kit, most likely so that they can optimize and improve their competitiveness over time. We also get a sense of how—as with the doggo mascot—authors inject personality and humor into their kits, leaving their own distinctive mark.
Understanding how phishing tradecraft are developed is essential to preventing phishing attacks. By analyzing phishing kits in-depth, it’s possible to improve the speed and accuracy with which threats can be detected, classified, and taken down.To find out how Netcraft can help you move more quickly and address threats at any scale, book a demo now.
https://www.netcraft.com/blog/doggo-threat-actor-analysis/
Published: 2024 10 30 20:52:41
Received: 2024 10 31 10:19:18
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 12
