Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Black Friday Gets a Fakeover: Fake Stores Spike 110% by Using LLMs this Holiday Shopping Season
published on 2024-11-26 01:36:33 UTC by Will BarnesContent:
Key Data
This article explores Netcraft’s research into the global growth of fake stores, including activity that makes use of the e-commerce platform SHOPYY to target Black Friday shoppers. Insights include:
- An increase of 110% in fake stores identified between August to October 2024
- Tens of thousands of fake stores utilizing the e-commerce tech platform SHOPYY
- More than 66% of SHOPYY-powered sites identified as fake stores
- More than 9,000 new and unique fake store domains detected by Netcraft between November 18–21, hosted on SHOPYY alone
- Most activity attributed to threat actors likely operating from China
- Activity primarily targeting U.S. shoppers
- Use of Large Language Models (LLMs) to generate text for product listings
Overview
Cyber Week, running from Black Friday to Cyber Monday (and often extending beyond), has become synonymous with holiday season shopping. Brands and e-commerce marketplaces offer significant discounts throughout November to entice consumers to buy products from their online stores. Some forecasts predict that 2024 Black Friday purchases will exceed those of 2023 by $1 billion. While legitimate brands go all out to provide the best offers, some too-good-to-be-true discounts are an indication of more malevolent activity — fraudulent online stores.
In 2023, we saw a 135% increase in fake online stores leading up to the holidays. This trend continues in 2024, with a 110% increase in domains hosting fake stores from August to October. This represents an all-time high, with more activity expected before the end of November 2024.
Since free domain names ceased being available in 2023, this growth represents a record investment in domain names for fake stores with each carrying a registration cost of $1 or more.
Powering the surge in volume is threat actors’ use of Large Language Models (LLMs) to generate long- and short-form text for the product descriptions on these sites. We first observed LLM-generated retail product descriptions in July 2024, and similar behaviors continue into the holiday shopping season. This includes examples of fake stores appropriating product listings directly from Amazon and using LLMs to rewrite the copy for enhanced search engine performance.
Large Language Product Laundering
SHOPYY (also referred to as SHOPOEM) is a Chinese e-commerce platform offering a broad portfolio of technical solutions to help retailers build and optimize online stores, promote their products, and accept different payment types. SHOPYY also provides hosting and domain registration on behalf of store operators.
Unfortunately, the customization and convenience that benefits genuine retailers can be misused by cybercriminals. While some legitimate businesses use SHOPYY as their e-commerce platform partner, we’ve detected thousands of SHOPYY-powered fake stores, increasing month-over-month since April 2024. Between November 18 to 21 alone, Netcraft’s systems identified more than 9,000 new fake store domains hosted through SHOPYY.
These sites often impersonate established brands to take advantage of their intellectual property, brand reputation, and existing customer base. Instead of offering the same quality products and services, they trick unsuspecting shoppers into paying for fake, substandard, or non-existent products.
SHOPYY’s sprawling store portfolio, which spans multiple hosting providers and domain registrars, creates opportunities for criminal exploitation. Such a large and distributed infrastructure means abuse reporting and effective controls are harder to orchestrate, which is likely why the majority of stores on SHOPYY appear to be fraudulent.
The spike since April 2024 can be mostly attributed to activities that catalog product listings scraped from Amazon. Since SHOPYY mainly serves Chinese-speaking users (the platform was founded in Xiamen, China, and offers documentation written exclusively in Mandarin Chinese), these threat actors are likely operating from the region. The activity targets English-speaking shoppers primarily in the U.S., with product listings scraped from Amazon’s U.S. site that offers $USD pricing.
Campaign Hallmarks
The following sections explore the hallmarks and behaviors exemplified by these SHOPYY threat actors.
Low Code Black Friday Branding
In early November, Netcraft systems observed SHOPYY-powered fake stores using a new “Black Friday” widget. This widget adds new code to their websites, revealing the promotional text that reads “Get Early Access to Our Black Friday Deals & More!” and Black Friday-themed imagery. Shortly after the code was introduced, these promotions became visible to site visitors (on November 19).
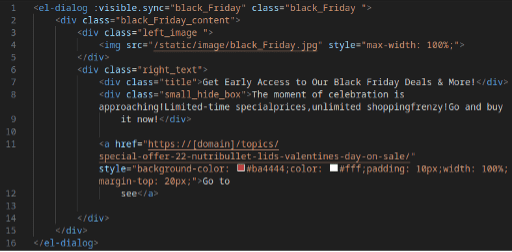
Fig. 1. Source code from a fake store site using the Black Friday widget.

Fig. 2. Example Black Friday-themed image.
Copy and Paste Amazon Product Listings
All of the sites identified list products cloned from Amazon, going so far as to configure each product ID to match the original listing. In the example below, the listing is a near-exact clone (containing the same product identifier — B08G8WTDR9 — in the URL). The only changes include new Teamfar product branding and a 30% discount.
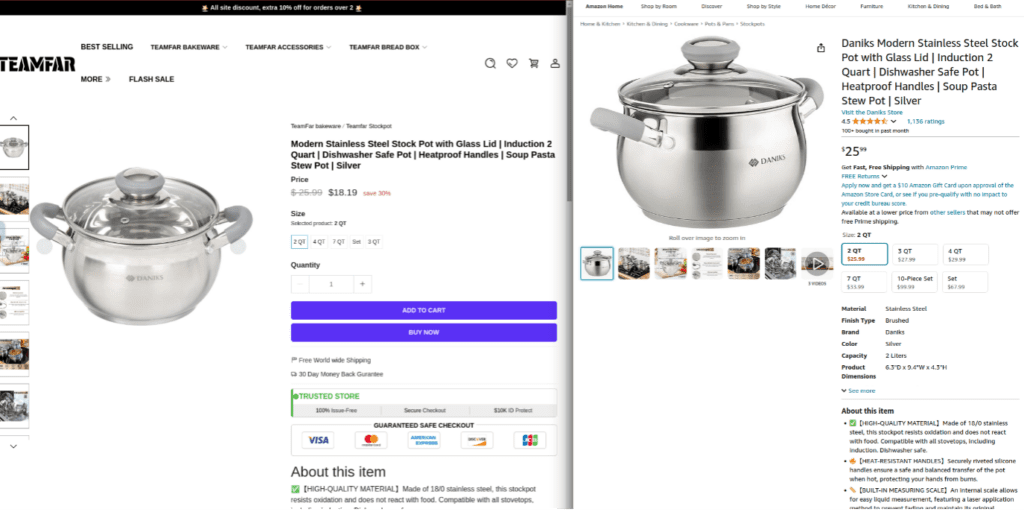
Fig. 3. (Left) Fake store listing for a Teamfar-branded stock pot priced at $18.19. (Right) The same stockpot with an identical product description and different branding on Amazon for $25.99.
Deep discounts are a telltale sign of fraudulent online activity, enticing victims to purchase via criminal-controlled sites. Following payment, these criminals may complete the order using one of the following actions:
- Provide legitimate goods by carrying out return fraud (receiving a refund for a product without completing a legitimate return) or paying using stolen credit cards
- Send the buyer low-quality, potentially counterfeit goods
- Most often, send nothing at all, taking payment, and harvesting details from the victim.
LLM-Generated Titles and Descriptions
Many of these sites use LLMs to rewrite the titles and descriptions for cloned product listings. This frequently yields convincing results. However, in many other cases, the LLM leaves artifacts that describe its own response to the prompt provided (“prompt”: the set of instructions given to encourage a desired response or action from the LLM). These errors may be due to the sheer scale of these activities, which makes human action uneconomical. Language differences between the threat actor and their victims can also mean that text errors are overlooked.
LLMs are often used to rewrite product details with prompts to:
- Refine, simplify, and include keywords in the text (likely for search engine optimization (SEO) purposes)
- Change the wording and reduce duplication while maintaining the same meaning
These characteristics are seen in the nutribullet blender listing below. If the framing text had been removed, the only change would have been removing the word “personal” that appears in the original Amazon listing. The description also appears to be generated using an LLM, featuring the verbose, formal writing style typical of most language models. In both listings, the URL includes the Amazon product code B0CBWD3PN7.
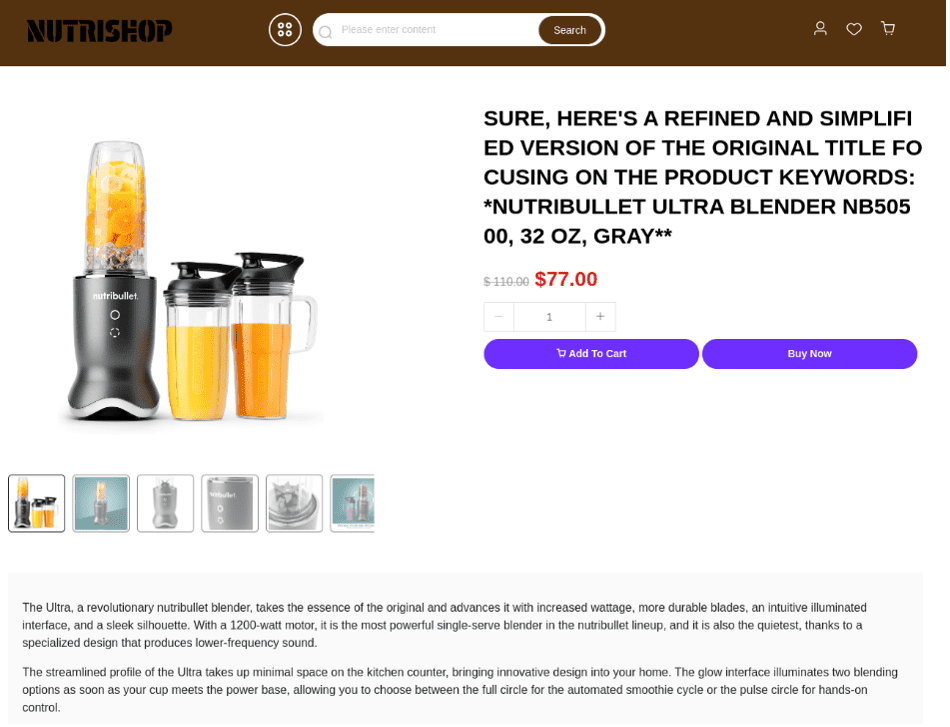
Fig. 4.
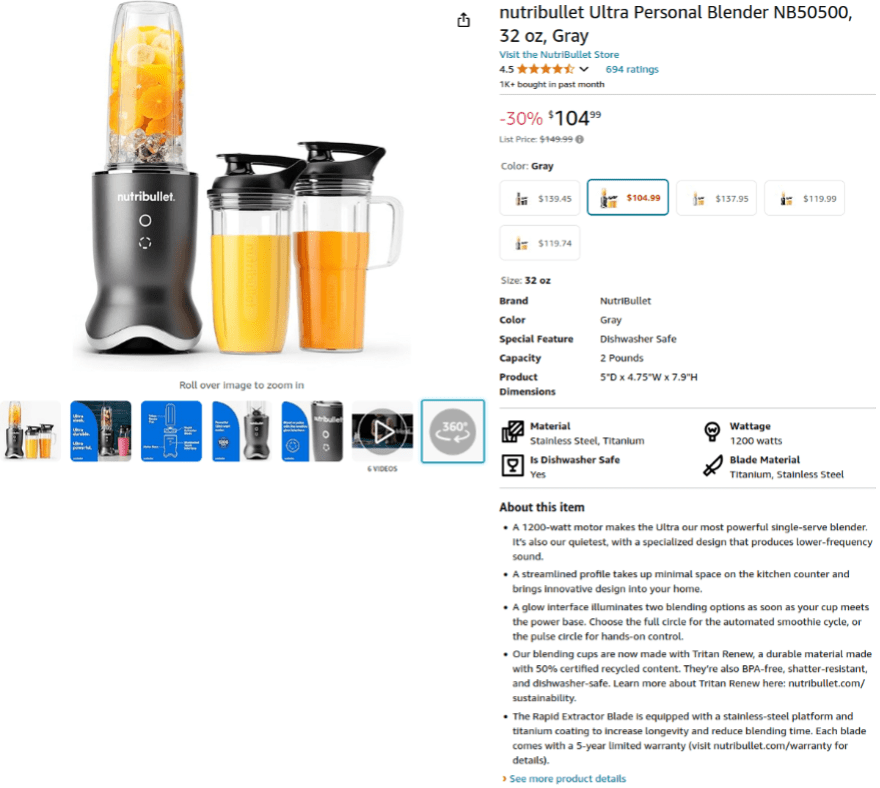
Fig. 5.
Fig 4 – 5. Artifacts reveal the use of LLMs to rewrite Amazon product descriptions. The nutrishop fake store listing for the nutribullet blender (top) has cloned, rewritten text from the Amazon listing (bottom).
In addition to editing listing titles, LLMs are being used to generate product descriptions, as shown in the Le Creuset example below. Here, the listing also leaks the threat actor’s text prompt with the response: “Here’s a rephrased version of each line to maintain their meanings while avoiding duplication.”
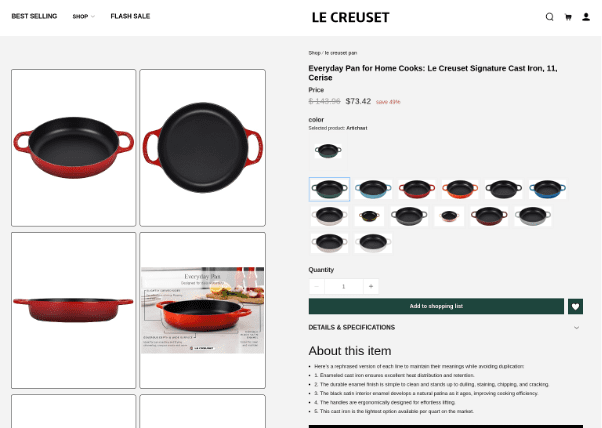
Fig. 6. This fake store, impersonating Le Creuset, leaks information about the LLM’s prompt as an artifact.
In the examples below, the entire product description has been populated with the original prompts:
- A rephrasing of “Modify the wording of each line to avoid duplicates while retaining the same meaning” appears in several forms where the LLM has resynthesized the text.
- The prompt appears verbatim: “Please rewrite the following content, adjusting the sentence structure while preserving the original meaning. Ensure the result remains within 500 words for better readability. Focus on using English directly in the output.”
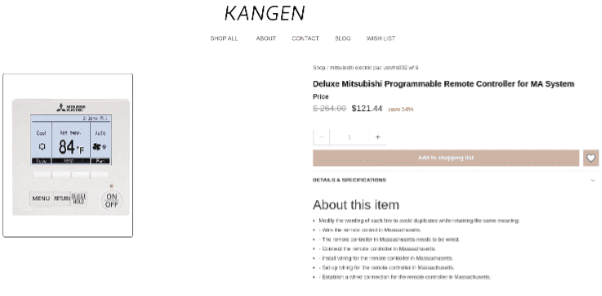
Fig. 7. A fake store selling air conditioning equipment leaks the LLM prompt asking for each line to be reworded.
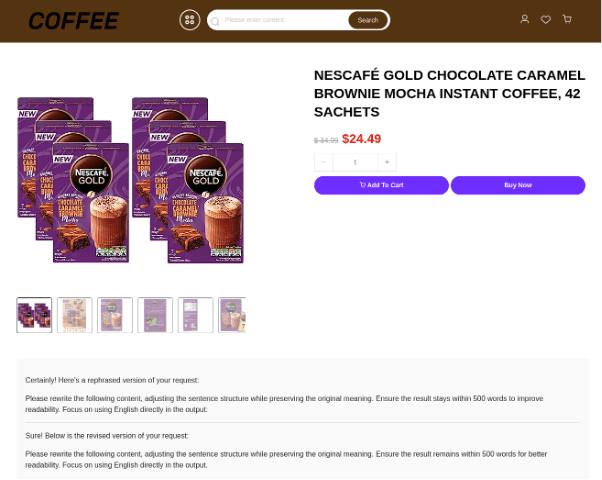
Fig. 8. A coffee-themed fake store leaks the LLM prompt used in full.
In Fig 7, note how a lack of input from the original product description has caused the LLM to hallucinate the “MA” in the text as the U.S. state code for Massachusetts.
Fake Trusted Store Seals
Trust adds value to online stores and their products. Many websites detailed throughout this article often feature a “Trusted Store” seal, either at the bottom of the page or directly under a product listing. When clicked, this offers a fake certification list: Certified Secure; 100% Issue-Free; Verified Business; Data Protection.
Unlike legitimate trust seals, there is no indication of who issued the certification, which demonstrates the bogus nature of the claim. To any unsuspecting user, this indicator of fraudulent activity could be easily missed.
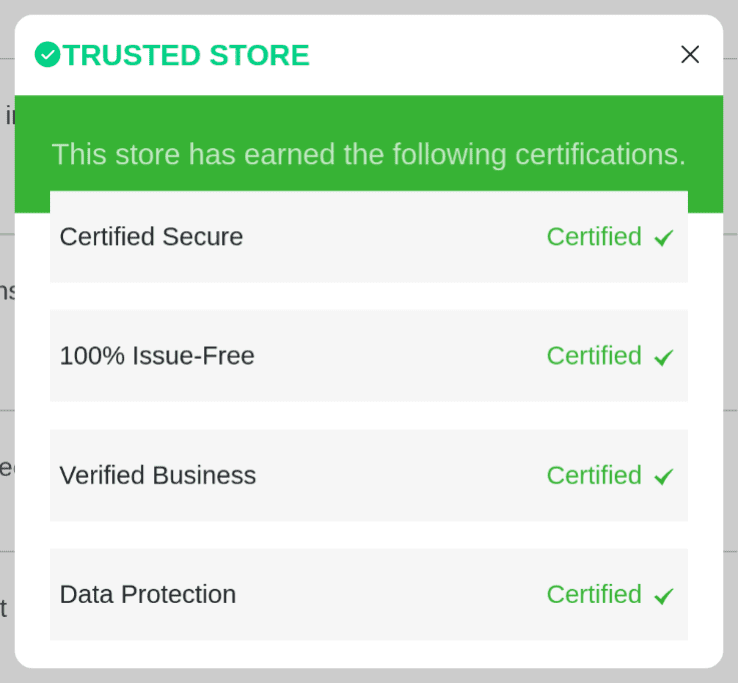
Fig. 9. Bogus “Trusted Store” seal on fake store sites.
This same seal is used on a range of fake shopping sites with different behaviors, suggesting it may be a plug-in available as a SHOPYY feature.
Flash Sale Page
The /MoreThemePages/ path on these sites (linked in the header or footer) takes the user to a “Flash Sale” page. In some cases, this page is broken. In others, it lists products from the fake store alongside various SEO terms tailored for seasonal sales throughout the year. This includes Black Friday, Valentine’s Day, Spring and Winter sales, and calendar months.
While LLMs don’t appear to have been used on this particular page, they are readily used by cybercriminals for SEO purposes.
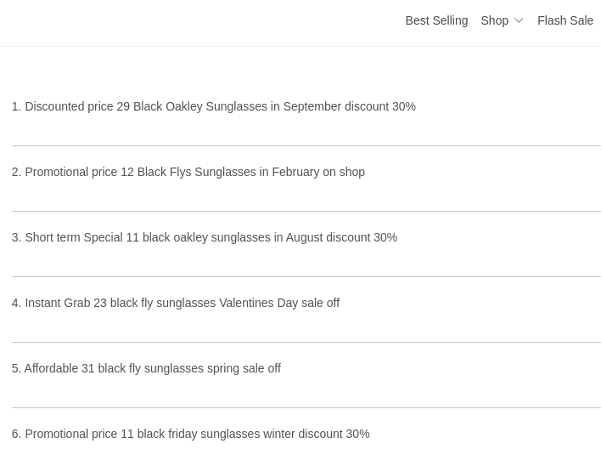
Fig. 10. Fake store using Black Friday terms for SEO alongside a selection of other discount and seasonal terms.
.shop Top-Level Domain
This surge of activity almost exclusively uses the .shop top-level domain (TLD) —93.5% of SHOPYY fake stores do so. The second most common domain is .com, accounting for 4.2% of all SHOPYY-powered domains.
Using .shop has dual benefits for fake store operators:
- It may suggest to any unsuspecting user that the shop is legitimate (“.shop” is a recognized TLD like “.com”) despite fewer legitimate online stores using it;
- It’s also a particularly low-cost solution for new domain registrations, reducing the cost of setting up many domains for criminal campaigns
In Summary
Black Friday, Cyber Monday, and the extended holiday shopping season is a time of heightened retail spending and online activity. This provides the ideal environment for threat actors to profit from shoppers’ money and data using fake stores. The allure of discounts and limited-time offers, and their sheer volume at this time of year, can easily create a false sense of security for consumers — making them more susceptible to scams.
With the use of LLMs and the customization available in tools like SHOPYY, cybercriminals can affordably create and host convincing fake stores quickly and at scale.
For retailers, fake stores are more than just a consumer inconvenience. They represent a significant brand protection and reputation issue. Fake store scams that impersonate your brand can result in:
- Damage to customer confidence and trust
- Increased complaints and negative reviews
- Added resulting support costs
- Lost revenue, as sales are diverted from legitimate sites
To combat the fake store threat, retailers must invest in proactive security measures, educate customers, and actively monitor for fraudulent activity and brand impersonation.
Netcraft’s fake store solutions detect, take down, and provide valuable intelligence on the criminals exploiting your customers and extracting value from your organization. We analyze more than 600,000 e-commerce sites per month and have taken down hundreds of thousands of fake shops to date, giving brands the freedom and confidence to grow their business without fear of brand abuse.
To find out more, read our latest fake store case study for fashion retailer YoungLA or book a demo now.
https://www.netcraft.com/blog/2024-llm-powered-fake-online-shopping-site-surge/
Published: 2024 11 26 01:36:33
Received: 2024 11 26 10:39:32
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 17
