Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Truth of the Matter: Scammers Targeting Truth Social Users
published on 2025-01-16 11:00:49 UTC by Penn MackintoshContent:
Key Data
- Threat actors immediately target new Truth Social users — Netcraft received more than 30 messages within hours of creating an account.
- Truth Social’s structure gives threat actors easy access to target groups with more than 100,000 members.
- Advance Fee Fraud scams average $250, with some scammers asking for as much as $1,000 at once on Truth Social.
- Central European, French-speaking threat actor preys on global victims by impersonating trusted brands including: Spotify, Disney+, EasyPark, Sky, Netflix, and Google.
Overview
Truth Social — the social media platform created by Trump Media & Technology Group (TMTG) in 2022 — is being abused to deploy scams at scale, from phishing websites to investment scams, according to Netcraft analysis.
Case in point: The Netcraft team received more than 30 scam messages within just a few hours of creating a single account on Truth Social. And, the cost of falling for these scams can be high.
The Federal Trade Commission (FTC) reported that 1 in 4 Americans who reported losing money to fraud since 2021 said it started on social media. During this same time period, reported losses to scams on social media hit $2.7 billion, far higher than any other method of contact. But this doesn’t include the large portion of scams that go unreported – and only looks at the United States. The true cost of social media scams worldwide is likely billions, if not trillions.
Looking more closely at Truth Social, Gizmodo explored consumer complaints filed with the FTC over the past two years. According to the research, the complaints about scams are “the most shocking, if only because there are such large sums of money involved.”
This blog post details Netcraft’s initial analysis of threat actors and malicious campaigns being used on Truth Social to target its users. Netcraft continually searches for fraudulent content on social media platforms, disrupting and taking down phishing, fraud, scams, and cyber attacks.
Why Scammers May Target Truth Social
In November, Truth Social saw 355,000 daily active users, up 3% from the prior month, according to Bloomberg. When a user joins Truth Social, they are prompted to join groups related to areas of interest and topics that users care about — and each group member can view a list of all other members.
Some of these groups have more than 100,000 members, providing threat actors with a rich source of information to identify and contact other users at scale. This makes it easy for scammers to simply pick a group, tailor a message targeting its members, and hit send. And, because users have opted into these groups, people may be less diligent about questioning information because of an existing confirmation bias.
At the same time, each post from a user is called a “Truth” and users may be taking that quite literally. According to previous reports from Pew Research, the majority of those who use Truth Social (87%) say they expect the news and information there to be mostly accurate.
With easy access to curated member lists and users more likely to trust Truths, as named, Truth Social is a prime target for bad actors.
Criminal Conversations: The Prevalence of Conversational Scams
In a single day, our U.S.-based Truth Social account received 40 unsolicited messages from scammers running a variety of scams.
Most of the attacks follow established peer-to-peer scam patterns, likely with multiple people responding to messages from each account on a rota. The scammer engages a victim in casual conversation and then begins the social engineering process in a way that creates interest from the victim.
All of the scammers we engaged claimed to be based across the United States. However, we observed individual scam accounts active at all hours, indicating that they are either AI-driven or based in other countries in different time zones. In our experience, scammers often start with questions and conversations regarding the location of their target, likely using physical location to build rapport with the victim and verify a victim’s vulnerability.
The first example below asks for an upfront fee to pay for the delivery of a package purportedly containing $20,000 in cash, with payment requested via Cash App. This scammer claimed to be in the same city as the victim — Dallas, Texas. They even look up the victim’s address and ask to meet in person in an effort to appear genuine.
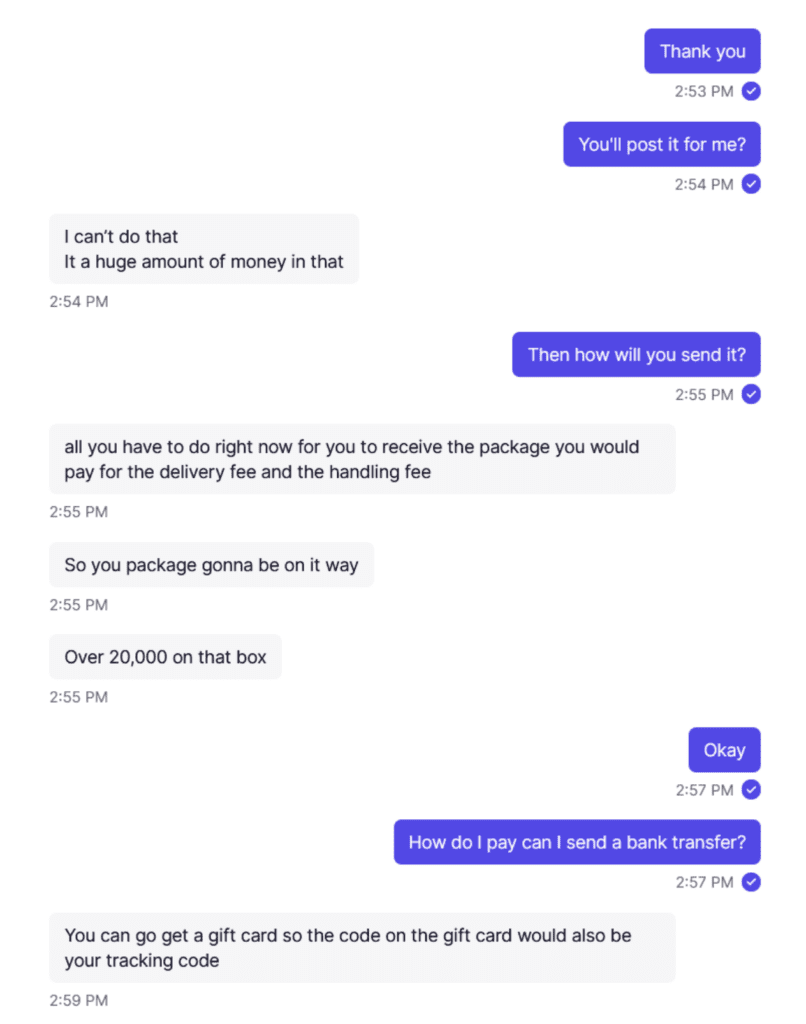
Fig. 1: Advance Fee Fraud scam example where scammer asks for funds to pay for a package
Other prevalent types of scam on Truth Social include romance scams and investment scams — sometimes called pig butchering, where a threat actor builds trust with the victim and then grooms them into making a series of ultimately ill-fated crypto investments. In the example below, a threat actor directed us to contact them on WhatsApp to make an investment in a supposed cryptocurrency platform.
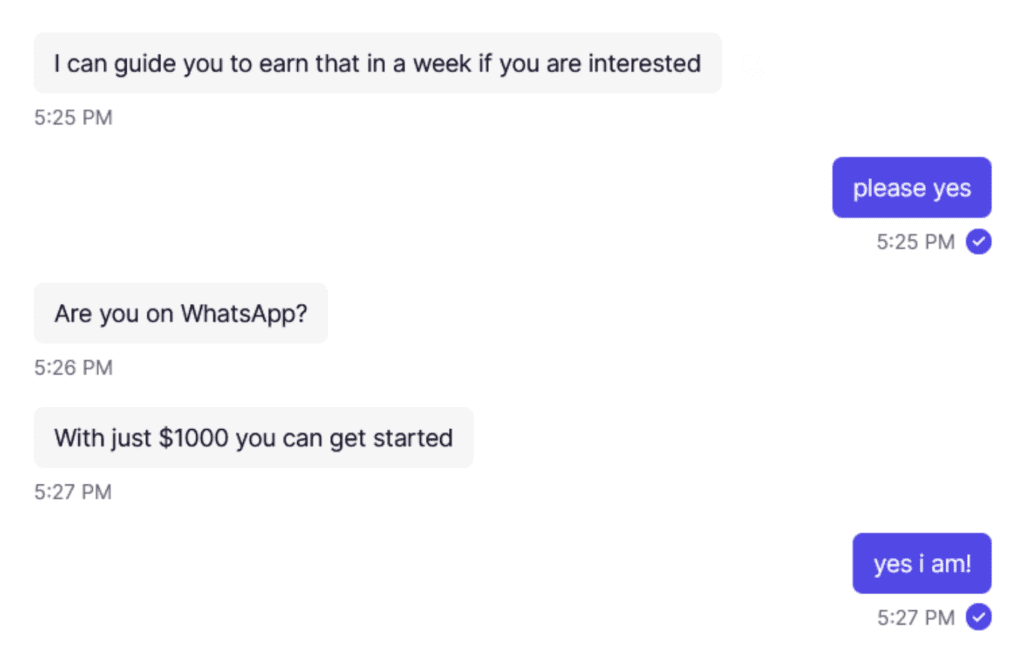
Fig 2. Threat actor entices victim to invest in crypto
The threat actor then followed up on WhatsApp, asking us to deposit funds using an online fake investment platform. Netcraft had detected fraudulent content on this site more than 2 months prior to this exchange.
Once hooked, a victim may continue to make further investments if the scammer is persistent in their correspondence with them, pouring more money over time into an account from which they can never withdraw funds.
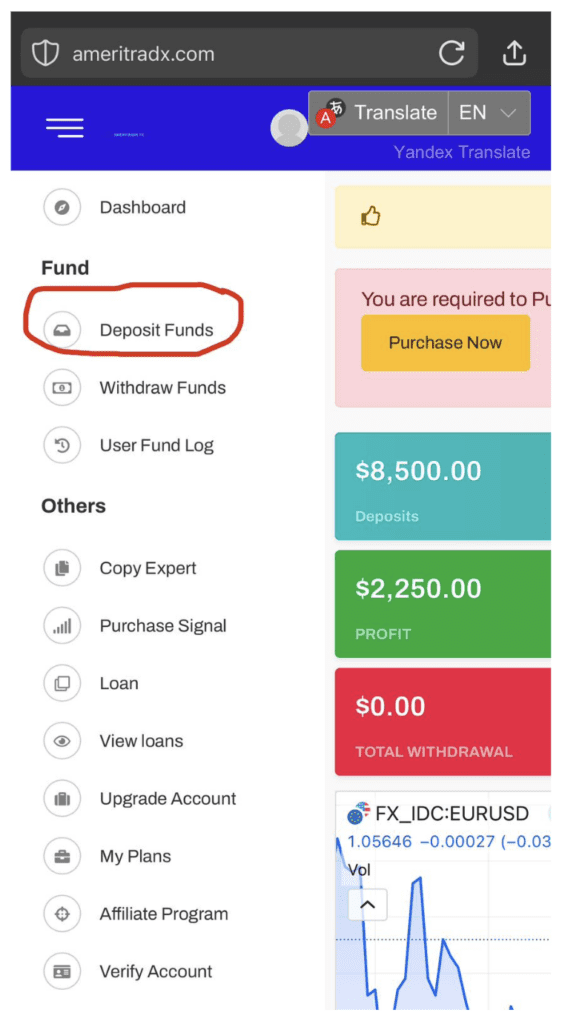
Fig. 3. Fraudulent investment site sent by scammer via WhatsApp
Phishing for the Truth: Threat Actors Aim to Hide Phishing Links from Detection
Our analysis shows Truth Social is also being used to distribute phishing links. Netcraft has identified a French-speaking threat actor based in Central Europe, continually adapting their methodology and changing services and approaches.
This threat actor has utilized at least 7 Truth Social accounts since March 2024, with more than 500 “Truths” posted. Each account has been used to post Truths containing links that point to phishing sites.
These phishing sites are created using a range of (mostly free) hosting platforms and infrastructure, as well as link shorteners and free web page builders. The phishing sites are impersonating well-known brands, including Spotify, Disney+, EasyPark, Sky, Netflix, and Google, and targeting users in the United States, Australia, New Zealand, Spain, Norway, Francophone countries, and Germany.
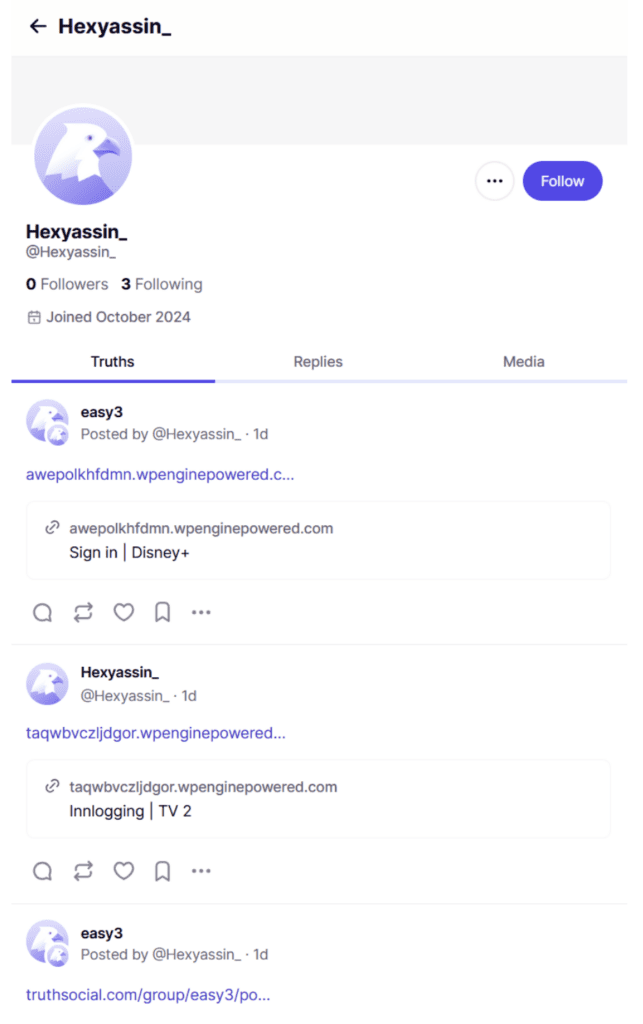
Figure 4: Identified malicious account on Truth Social sharing phishing links to a fake Disney+ site and more
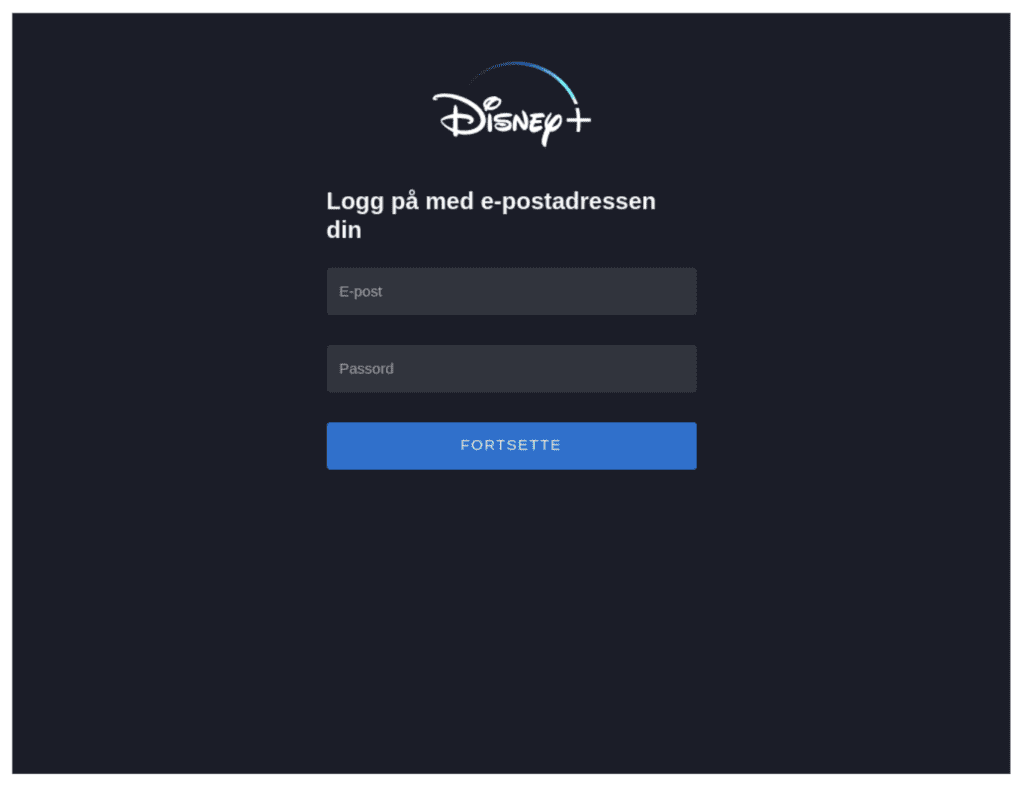
Figure 5: Phishing site impersonating Disney+ login in Norway in order to steal banking details
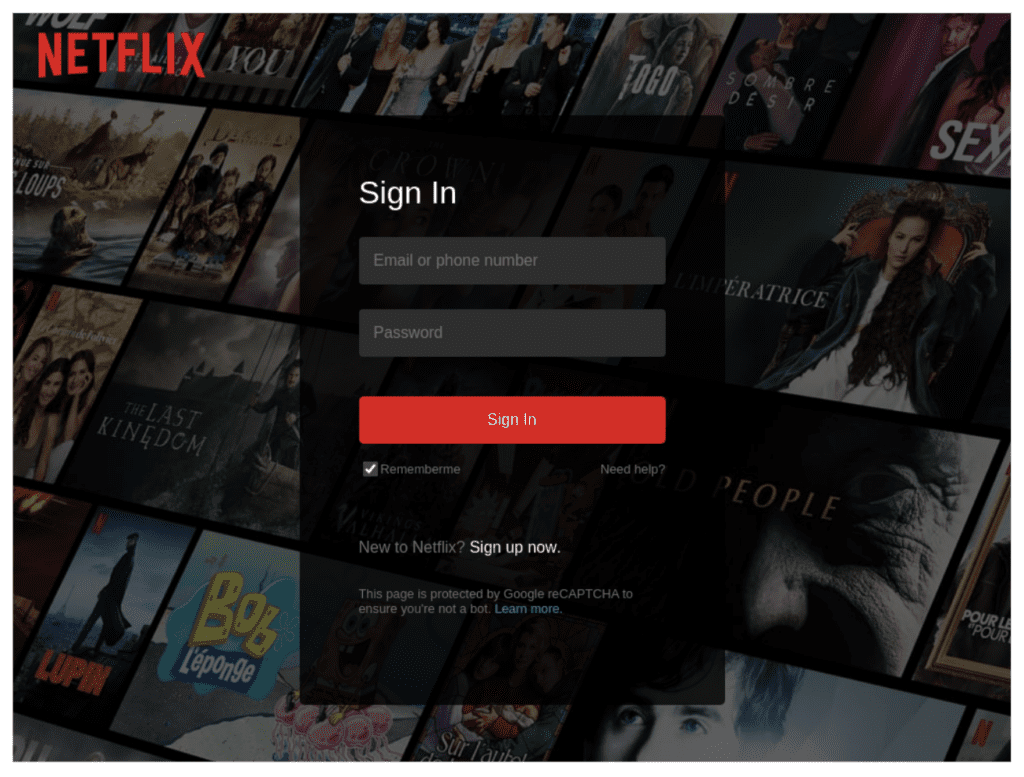
Figure 6: Phishing site impersonating Netflix login, where the backdrop reveals the scammer’s locale is set to French
In most cases, victims receive an unsolicited email saying their subscription for a service has expired and payment details must be updated. Once they log in, they are directed to a form to enter bank details to update their payment information. This login and payment information is then stolen. Here’s more detail on how it works:
Walking Through a Phishing Attack Using Truth Social
- Threat actor sends a lure email from Jira Help or compromised webmail.
- A victim receives the lure email telling them that their subscription to a platform is about to expire. By redirecting via Truth Social, the email can avoid being detected by email filters and anti-virus tools.
- The victim clicks the link, which opens Truth Social and immediately redirects to the phishing page — without ever displaying the scammer’s Truth to the victim.
- The victim finds themself on a login page that looks realistic. However, they could detect the attack if they check the URL carefully.
- The victim enters their login details, which are always accepted regardless of what is entered.
- The victim is then prompted to enter their banking details, purportedly to renew their subscription. The threat actor now has the keys to this bank account, enabling them to cash out in various ways — using the account to launder money, sell account details to other bad actors, clone debit or credit cards, and even empty accounts entirely.
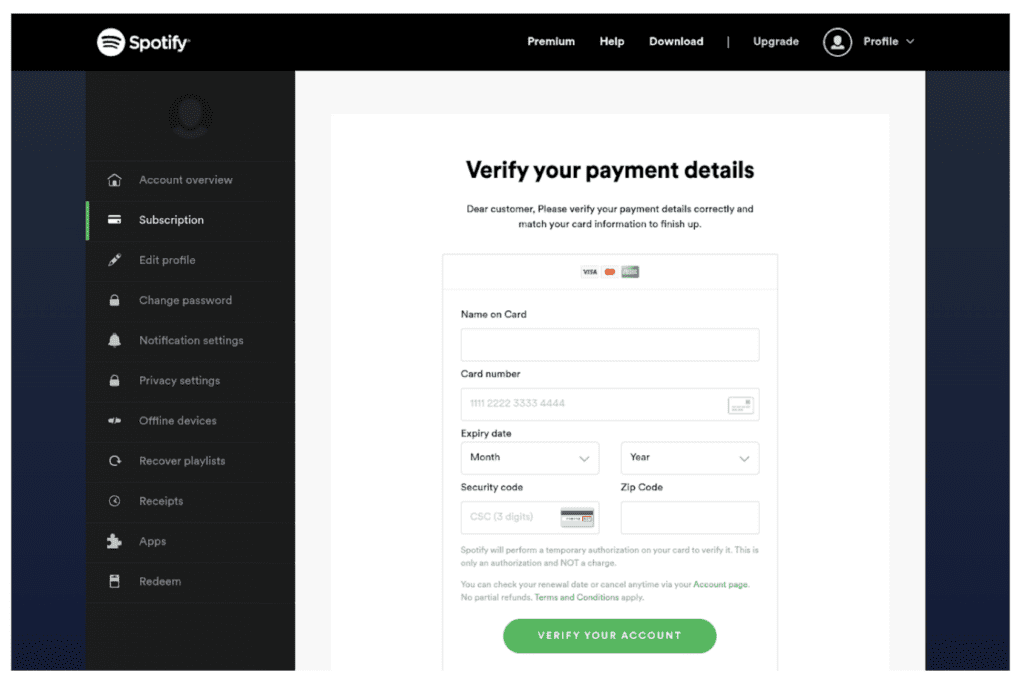
Figure 7: Fake Spotify site designed to steal users’ bank details.
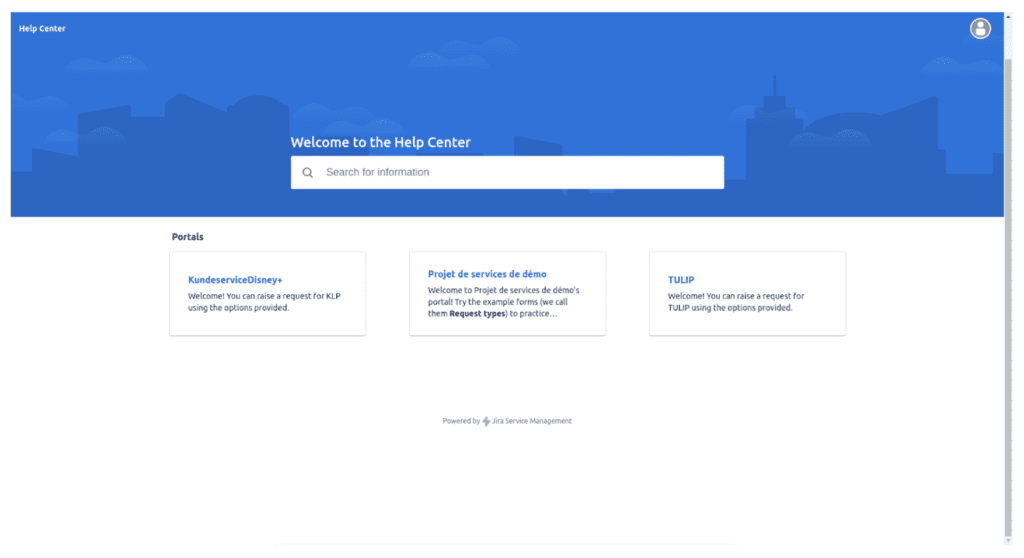
Figure 8: Jira Help portal used to send phishing emails from high-reputation Atlassian servers
Protecting Your Business — and Consumers — from Social Media Scams
The amount of phishing, fraud, and scams increases every day — and artificial intelligence is making it easier than ever for bad actors to take advantage of the billions of social media users online worldwide.
It’s critical for businesses to leverage new technologies to detect, disrupt, and take down threats to their business, brand, and reputation, as well as help protect their consumers from harm. Netcraft operates around the clock to detect and stop cyber threats across a wide range of digital channels for more than 100 attack types across many threat channels, including phishing, advance fee fraud, and more.
To learn more about how Netcraft can help defend your brands against social media scams and phishing, request a demo today.
Truth Social users can also report any scam websites they encounter directly to Netcraft, and protect themselves from known sites using the Netcraft Browser Extension and Apps.
https://www.netcraft.com/blog/truth-social-scam-threat-review/
Published: 2025 01 16 11:00:49
Received: 2025 01 16 15:01:00
Feed: Netcraft
Source: Netcraft
Category: Cyber Security
Topic: Cyber Security
Views: 3
