Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Top Malware Types on the Dark Web in 2024
published on 2024-10-06 12:21:07 UTC by Lior NoyContent:
In 2024, malware continues to be one of the most significant threats in cyberspace, evolving in both sophistication and frequency. This year, cybercriminals have increasingly adopted a mix of tactics, frequently turning to the dark web to spread various malware variants. The dark web remains a bustling marketplace for cybercriminals to share, sell, and buy malicious software that targets individuals, businesses, and even government entities. Leveraging advancements in AI and Machine Learning, cybercriminals have enhanced their capabilities, making detection more difficult. As organizations continue to migrate to the cloud and increase reliance on digital tools, the dark web has become a pivotal hub for the distribution of malware that exploits these vulnerabilities.
In this article, we explore the top 5 malware types dominating the dark web in 2024, examining their key capabilities, how they infiltrate systems, and the widespread impact they’ve had across different industries. From ransomware and stealers to loaders and more, we’ll delve into how these threats evolve and why they continue to pose significant risks.
So how can I get hit by malware?
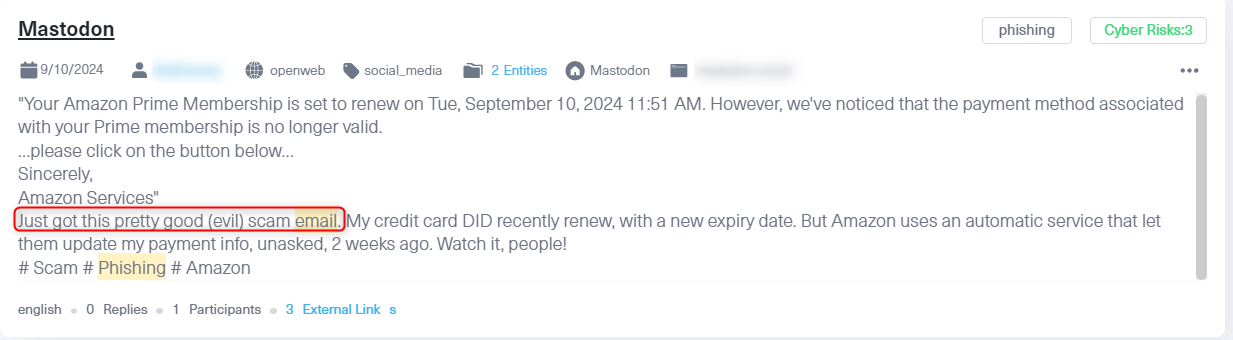
This post from Mastodon, an alternative social media platform, highlights a phishing scam disguised as an Amazon Prime renewal notice. The user shares their experience receiving a convincing fake email that attempts to steal payment details by prompting the recipient to update their payment method.
- Phishing Emails
- A common way to spread malware is through phishing attacks, where users are tricked into clicking malicious links or downloading infected attachments.
- Malicious Downloads
- Cybercriminals often disguise malware as legitimate software such as cracked programs, unauthorized apps like uTorrent, or fake updates. Malicious apps can hide malware that compromises systems.
- Drive-by Exploits/Downloads
- Simply visiting compromised websites can result in malware being downloaded onto your system without your knowledge.
- Exploit Kits and CVEs
- Attackers exploit vulnerabilities (CVE: Common Vulnerabilities and Exposures) in unpatched software or systems to install malware. Exploit kits bundle multiple vulnerabilities to increase the success rate of infections.
Malvertising: Malicious ads trick users into clicking on them, leading to the download of malware.
- Attackers exploit vulnerabilities (CVE: Common Vulnerabilities and Exposures) in unpatched software or systems to install malware. Exploit kits bundle multiple vulnerabilities to increase the success rate of infections.
- Weak or Exposed RDP: Remote Desktop Protocol (RDP) is often targeted to deliver malware by exploiting weak configurations or poor security practices.
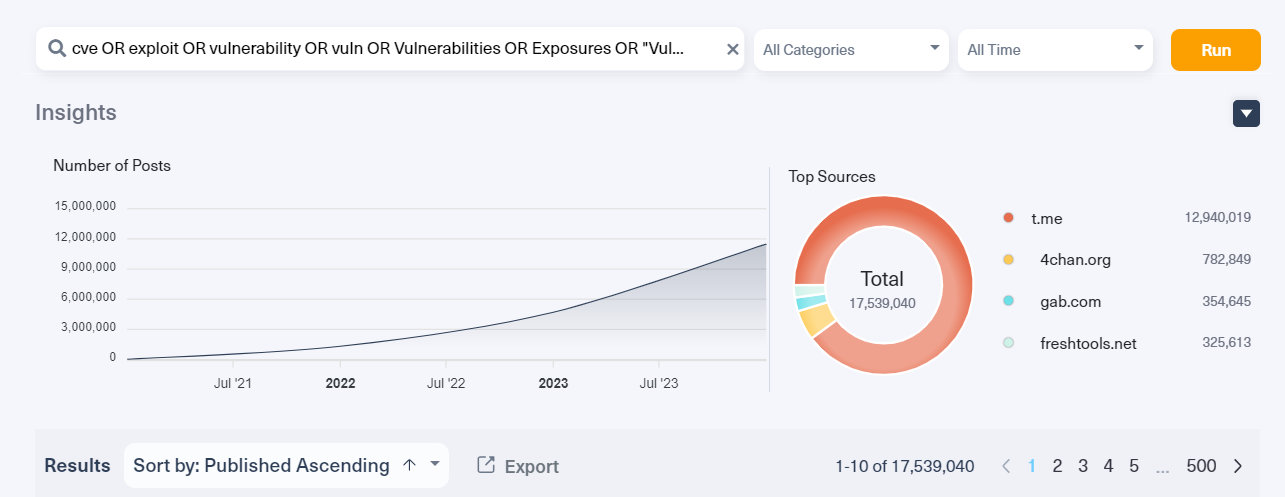
We used Lunar, our dark web threat intelligence tool, to analyze over 17 million posts on the dark and deep web. The graph shows a significant increase in discussions related to CVEs, exploits, and vulnerabilities over the past few years. In July 2021, there were less than 3 million mentions while in July 2023 there were almost 12 million mentions, or 4 times the amount of interest in exploiting vulnerabilities. The chart on the right shows that Telegram (t.me) is the top source, followed by other platforms like 4chan and gab.com. More and more threat actors are using exploit kits and taking advantage of CVEs. As a cyber analyst, it is crucial for you to understand how and why threat actors are exploiting different network vulnerabilities to better predict and defend against emerging threats.
What are the top 5 malware types in 2024?
- RATS (Remote Access Trojans)
- What is a RAT?A RAT is a type of malware that allows attackers to gain complete remote control over an infected computer or network. Once a RAT has been successfully installed, the attacker can monitor user activity, steal sensitive information, execute commands, and even control the system as if they were physically present.
- What can a RAT do?
- Remote control: Attackers can fully control an infected system, executing commands, modifying files, and installing additional malware.
- Keystroke logging and credential theft: RATs often include keyloggers to capture sensitive information like passwords and login credentials, which can also be extracted from browsers.
- File and system access: Allows attackers to download, upload, or delete files, as well as activate webcams and microphones for surveillance.
- Persistence: Many RATs install backdoors, giving attackers long-term access to the system without detection
- Which RAT strains are common in 2024?
- NanoCore: A popular RAT known for its robust features that allow attackers to gain full remote control over compromised systems.
- DarkComet: Continues to be widely used, offering a range of remote access capabilities favored by cybercriminals for espionage and data theft.
- AsyncRAT: A newer strain gaining attention for its customization options and ease of use, making it a go-to choice for targeting businesses and individuals.
- Remcos: Known for its flexibility and wide availability on dark web forums, Remcos has become favored by attackers due to its versatile functionality and ease of deployment.
These RATs are often sold on dark web forums and are frequently bundled with other malware as part of larger attacks.
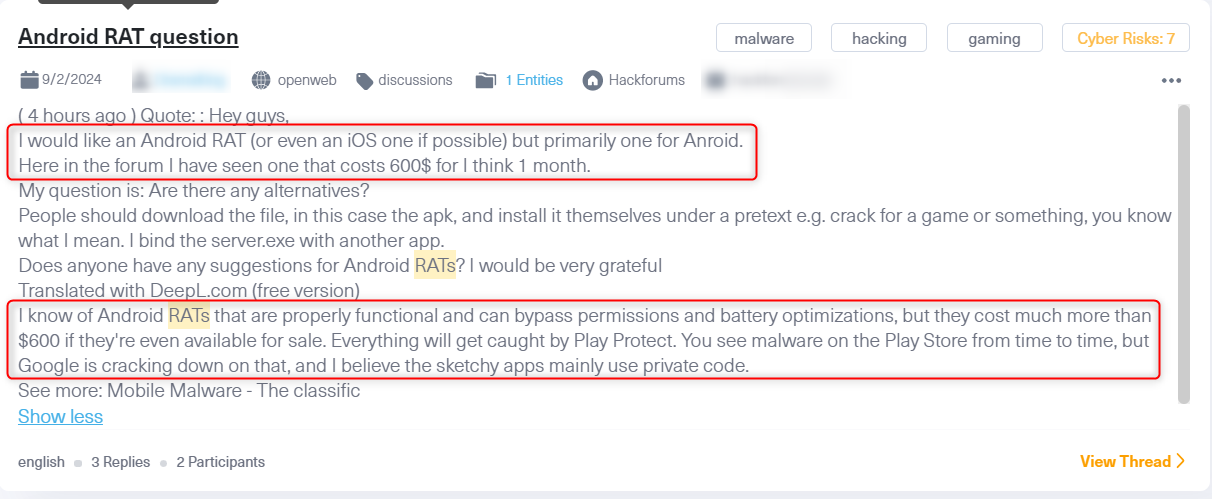
On this thread from Hackforums, a well-known hacker forum, threat actors discuss pricing and alternatives for Android RATs. One user suggests that functional RATs capable of bypassing security checks are typically expensive, though some occasionally make it to the Play Store before being caught. Using Lunar, our cyber monitoring tool, we can effectively track these discussions, keeping up with various RAT functions, pricing, and actors involved, helping cybersecurity analysts stay informed about emerging threats.
- Ransomware
- What is ransomware?Ransomware is a type of malware designed to encrypt a victim’s files or lock them out of their system until a ransom is paid, usually in cryptocurrency. Attackers often threaten to keep the data encrypted permanently or perform double extortion by leaking sensitive data if their demands are not met. Ransomware attacks can cause widespread disruption, especially for businesses, hospitals, and government organizations, as the encrypted data is often critical to operations.
- What can ransomware do?
- Data encryption: Ransomware encrypts files and folders on a victim’s system, rendering them inaccessible.
- Network propagation: Many ransomware variants are capable of spreading laterally within a network, affecting more devices and causing widespread damage.
- Data exfiltration: Some ransomware not only encrypts data but also steals it, giving attackers additional leverage over victims.
- Persistence: Ransomware can sometimes remain dormant, reactivating after attempts to remove it or triggering additional attacks after a set time period.
- Common ransomware strains in 2024
- LockBit 3.0: A leading strain operating under the Ransomware-as-a-Service (RaaS) model, LockBit targets industries like healthcare and finance, using efficient encryption and extortion methods.
- BlackCat (ALPHV): Known for utilizing the Rust programming language, BlackCat stands out by refining double extortion tactics, threatening to leak stolen data to extract larger ransoms from victims.
- Hunters International: An emerging ransomware group in 2024, linked to former affiliates of Hive, a notorious ransomware group disbanded in early 2023. Hunters International focuses on corporate and public infrastructure attacks, utilizing increasingly aggressive tactics such as double extortion.
- RansomHub: Launched in early 2024, this group quickly gained prominence by targeting sectors like energy and healthcare, using extortion and data auction methods to pressure victims into paying ransoms.
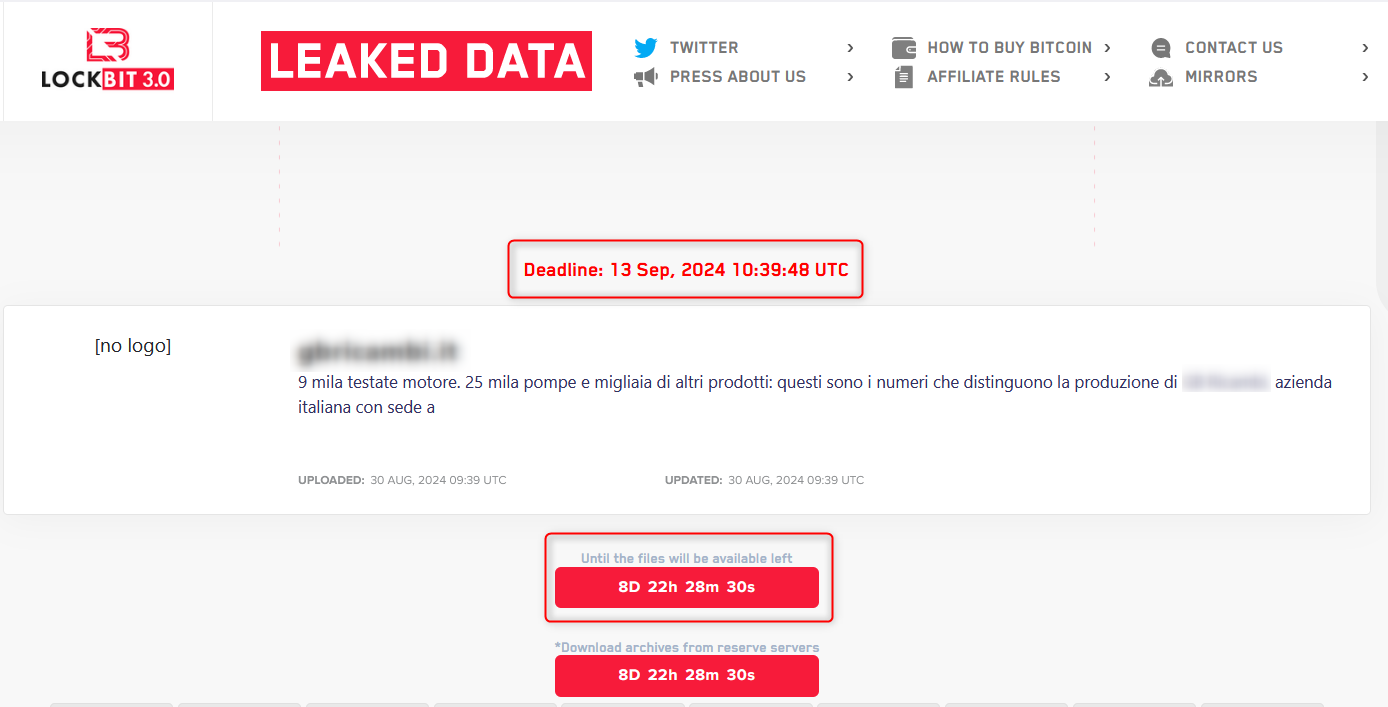
The image shows a LockBit 3.0 ransomware leak page. It features a listing for a victim (an Italian company). The page includes a countdown timer indicating the deadline for ransom payment before the stolen data is made public, which is set for September 13, 2024.
- Stealers
- What is a stealer?A Stealer is a type of malware designed to extract sensitive data from an infected system, typically targeting information like login credentials, credit card details, cryptocurrency wallets, and system information. The stolen data is often sent to a remote command-and-control (C2) server operated by the attacker, who can then sell or use the data for further malicious activities. Stealers are often lightweight and simple, making them easy for cybercriminals to deploy.
- What can a stealer do?
- Data harvesting: Stealers primarily target browser data (saved passwords, cookies, and autofill data), crypto wallets, and system information.
- Credential theft: They extract login credentials stored in browsers, allowing attackers to perform credential-stuffing attacks or sell the data on dark web markets.
- Crypto wallet exfiltration: Many modern stealers can also steal cryptocurrency wallet credentials, targeting both browser extensions and standalone wallet applications.
- System and browser fingerprinting: They collect system details and browser configurations, which can be used in bypassing security measures like two-factor authentication (2FA).
- Common stealer strains in 2024
- RedLine: A widely used stealer known for efficiently harvesting credentials, credit card information, and cryptocurrency wallets. It’s popular among cybercriminals for its data theft capabilities.
- Vidar: Another prominent strain, Vidar is favored for its ability to extract a wide range of sensitive information, making it a go-to choice for attackers targeting personal and financial data.
- Lumma: A newer strain gaining attention for its specialized focus on cryptocurrency assets. Its ease of distribution via Malware-as-a-Service (MaaS) platforms contributes to its rising popularity.
- RisePro: Also gaining prominence in 2024, RisePro is valued for its capability to target cryptocurrency wallets and its frequent appearance on dark web forums, where it is sold alongside other malware.
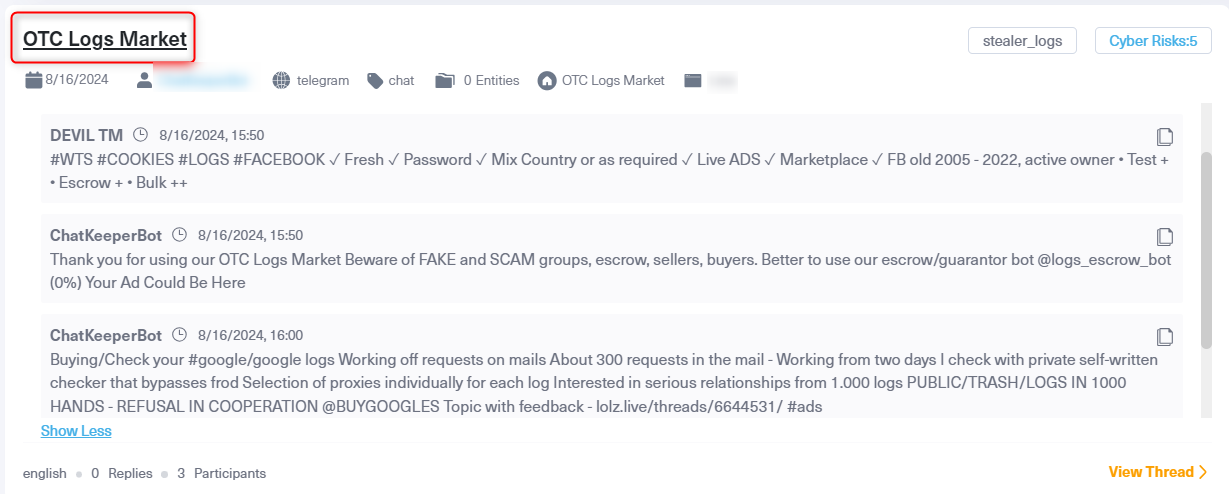
Posts from a Telegram channel managing a private marketplace for selling logs and stolen credential data.
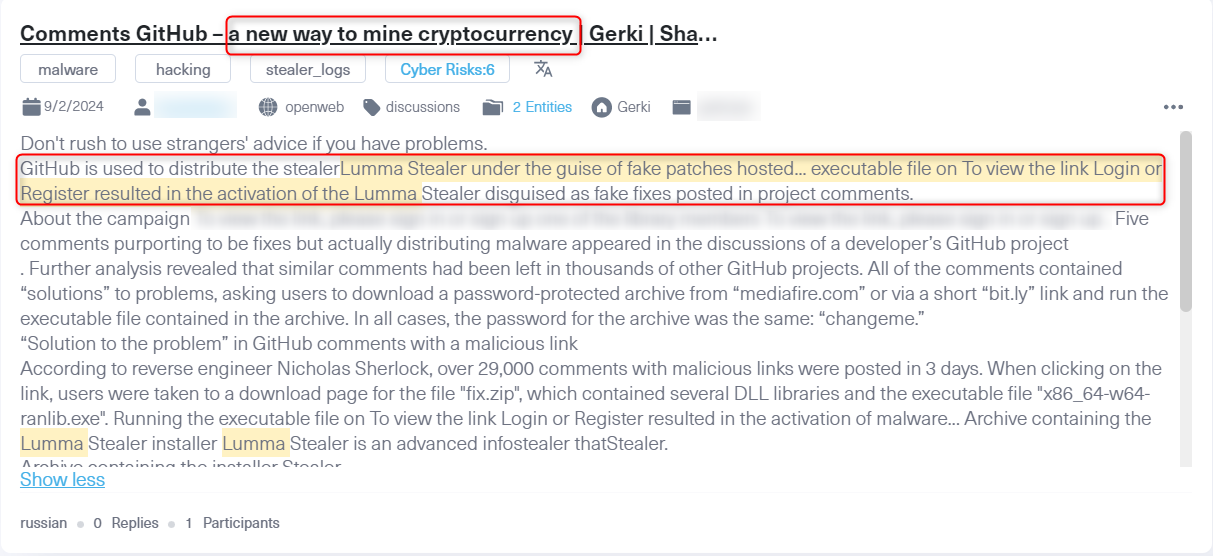
A post from Gerki, a Russian forum known for its focus on dark web activities, hacking, and blackhat topics, discusses the Lumma Stealer, connecting it to a new cryptocurrency mining technique through GitHub comments. Posts like these highlight the ongoing exploitation of trusted platforms like GitHub to distribute malware. Monitoring such threats is crucial, as this technique could enable unauthorized crypto mining on systems, leading to potential data breaches or operational disruptions.
- Loaders
- What is a loader?A Loader is a type of malware designed to infiltrate a system and deliver additional malicious payloads. Unlike other forms of malware that focus on direct exploitation, Loaders act as the initial stage of an attack, gaining access and laying the groundwork for further malware installation. Once inside the system, Loaders deliver more destructive malware such as ransomware, stealers, or Remote Access Trojans (RATs).
- What can a loader do?
- Payload delivery: Loaders are primarily used to install other malware on an infected system, ranging from ransomware to credential stealers.
- Persistence: Many modern loaders are designed to maintain a foothold in the system, ensuring they can continue downloading additional malware over time.
- Evasion: Loaders employ advanced techniques to avoid detection, such as script-based evasion and incorporating digital signatures to appear legitimate.
- Common loader strains in 2024
- SocGholish: One of the most prominent loaders in 2024, known for its persistence and evasion techniques, allowing it to silently install additional malware on compromised systems.
- GootLoader: Popular for using techniques like SEO poisoning to lure victims to malicious websites, where it installs other malware, including ransomware and stealers.
- Raspberry Robin: Gaining prominence due to its distribution via infected USB drives and its ability to deliver various types of malware, making it a versatile loader.
- HijackLoader: An emerging strain in 2024, notable for its sophisticated techniques and capability to deliver multiple malware payloads.
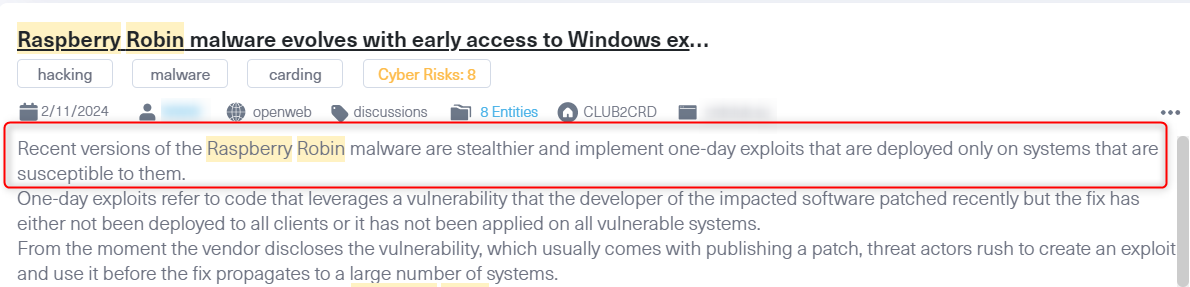
A post from Brian’s Club, a well-known Russian-speaking dark web forum primarily focused on carding—the trade of stolen credit card information and payment data. The post discusses recent developments in the Raspberry Robin malware, highlighting its evolution to become stealthier and its use of one-day exploits. These exploits target vulnerabilities in systems that have not yet fully applied recent security patches, allowing attackers to exploit the gap between patch releases and deployment.
- Spyware
- What is spyware?Spyware is a type of malicious software designed to covertly infiltrate systems and collect sensitive information such as login credentials, browsing history, or personal data. Spyware often operates in the background, transmitting the gathered information to attackers for misuse, such as identity theft, financial fraud, or surveillance. It is commonly deployed in both individual and corporate espionage campaigns.
- What can spyware do?
- Data collection: Spyware can harvest sensitive data, including passwords, chat messages, browsing history, and more. The victim is unaware of what is happening on his computer.
- Keystroke logging: Many spyware variants act as keyloggers, recording everything typed on the keyboard, enabling attackers to capture login details, credit card information, and private communications.
- Surveillance: Advanced spyware can activate the victim’s webcam or microphone, capturing real-time audio and video data.
- Evasion and persistence: Spyware employs sophisticated techniques to avoid detection by antivirus software, including code obfuscation, encryption, and injecting into legitimate processes.
- Common spyware strains in 2024
- Formbook: One of the most prevalent spyware families in 2024, favored by cybercriminals for its ease of use and its ability to steal user input and exfiltrate sensitive data.
- Darkgate: Known for its versatility, Darkgate serves both as spyware and a loader, capable of remotely controlling infected machines and even engaging in cryptocurrency mining.
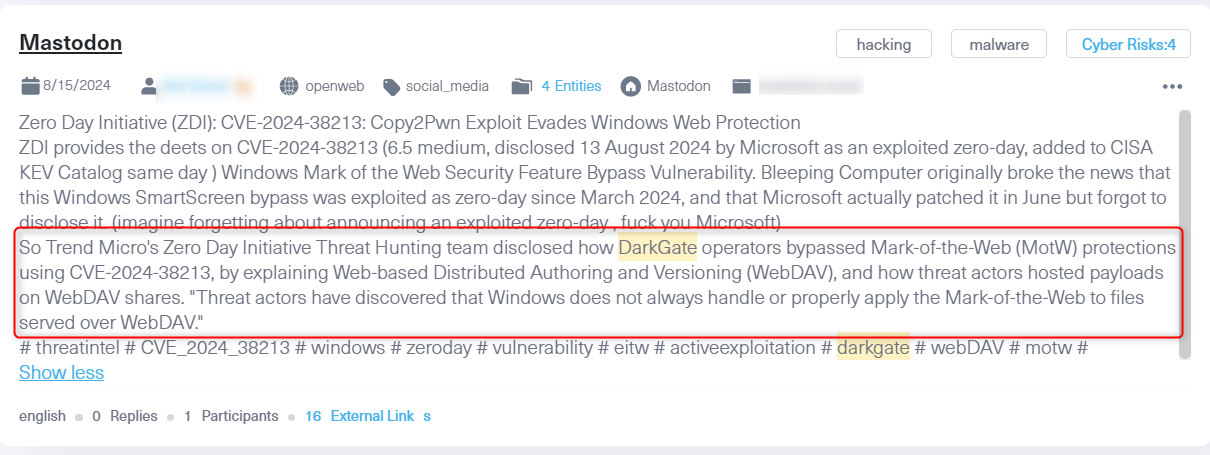
A post from Mastodon, an alternative social media platform, discussing the CVE-2024-38213 vulnerability, a zero-day exploit that bypasses Windows Web Protection using the Mark of the Web (MotW) feature. The post explains how DarkGate operators exploited this flaw via WebDAV to distribute malicious payloads on Windows systems.
Malware Hotspots: Key Platforms for Distribution and Exploitation
Malware, including stealers, ransomware, RATs, loaders, and spyware, is commonly distributed through dark web forums, hacker communities, and specialized marketplaces like Exploit and Dread. Many cybercriminals utilize Malware-as-a-Service (MaaS) and Ransomware-as-a-Service (RaaS) platforms, which provide pre-built malware, technical support, and management dashboards. These platforms are accessible to a wide range of threat actors, from low-level cybercriminals to advanced persistent threat (APT) groups, depending on their purpose and objectives. Some malware strains can also be found on open-source platforms like GitHub, though this is less common for more advanced threats.
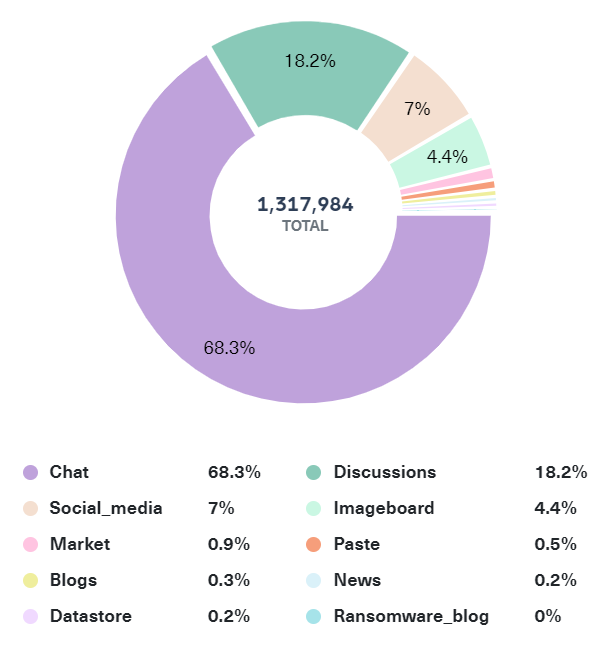
The attached screenshot is taken from Lunar’s data segmentation tool. It shows the distribution of sources for malware-related data. The tool segments the data into categories like chat platforms, discussion forums, social media, and dark web marketplaces.
Looking forward: protecting your business against future malware threats
As malware evolves, staying ahead of this serious threat requires constant vigilance. Cybercriminals utilize hacker forums, dark web marketplaces, and even social media platforms to distribute malware, leak sensitive data, and trade stolen information. To effectively protect against these threats, it’s crucial to remain informed about the latest trends, identify potential breaches, and monitor if your data has been leaked or sold.
Stay updated on the latest threats and ensure your data remains secure by leveraging these advanced solutions like Lunar.
The post Top Malware Types on the Dark Web in 2024 appeared first on Webz.
https://webz.io/dwp/top-malware-types-on-the-dark-web-2024/
Published: 2024 10 06 12:21:07
Received: 2025 03 10 09:23:58
Feed: Webz.io Dark Web Posts Dark Web News
Source: Webz.io Dark Web Posts
Category: News
Topic: Dark Web
Views: 12
