Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.The Origins of the Names TaoSecurity and the Unit Formerly Known as TAO
published on 2021-04-01 18:00:00 UTC by Richard BejtlichContent:
What are the origins of the names TaoSecurity and the unit formerly known as TAO?
Introduction
I've been reading Nicole Perlroth's new book This Is How They Tell Me the World Ends. Her discussion of the group formerly known as Tailored Access Operations, or TAO, reminded me of a controversy that arose in the 2000s. I had heard through back channels that some members of that group were upset that I was operating using the name TaoSecurity. In the 2000s and early 2010s I taught classes under the TaoSecurity brand, and even ran TaoSecurity as a single-person consultancy from 2005-2007.
The purpose of this post is to explain why, how, and when I chose the TaoSecurity identity, and to show that it is contemporaneous with the formal naming of the TAO group. The most reliable accounts indicate TaoSecurity predates the TAO brand.
TaoSecurity Began with Kung Fu and Taoism
 |
| With Sifu Michael Macaris, 21 June 1996 |
In the summer of 1994, after graduating from the Air Force Academy and before beginning my graduate program at what is now called the Harvard Kennedy School, I started watching re-runs of the 1970s David Carradine Kung Fu TV series, created by Ed Spielman. I was so motivated by the philosophical message of the program that I joined a kung fu school in Massachusetts. I trained there for two years, and studied what I could about Chinese history and culture. I learned from the show and that it was based on Taoism (for example) so I bought a copy of the Tao Te Ching by Lao Tzu and devoured it.
Visiting China
 |
| Tai Chi on the Yangtze, May 1999 |
In the spring of 1999 my wife and I took a three week trip to China for our honeymoon. We were both interested in Chinese culture so it seemed like a great opportunity. It was an amazing trip, despite the fact that we were in China when the United States bombed the Chinese embassy in Belgrade.
I include these details to show that I was quite the fan of Chinese culture, well before any formal cyber threat intelligence reports associated me with China. I read books on Taoism and embraced its concepts.
Creating TaoSecurity
 |
| WHOIS lookup for taosecurity.com |
In the summer of 2000 I was a captain at the Air Force Computer Emergency Response Team, within the 33rd Information Operations Squadron. I decided I wanted to try creating a Web presence, so I registered the TaoSecurity domain name on 4 July 2000. The WHOIS record above shows 3 July, which is odd, because a previous post on the topic captured the correct date of 4 July 2000. I also coined the phrase "the way of digital security."
My wife commissioned an artist to design the TaoSecurity logo, which I have used continuously since then. At the time I had never heard of TAO. There was a good reason for that. TAO was just being born as well.
General Hayden on Creating TAO
 |
| Playing to the Edge by General Michael Hayden |
A succinct source on the origins of the unit previously known as the TAO is the 18 October 2018 article by Steven Loleski. He wrote a piece called From cold to cyber warriors: the origins and expansion of NSA’s Tailored Access Operations (TAO) to Shadow Brokers (PDF). Mr. Loleski cited General Michael Hayden's 2016 book Playing to the Edge, which I quote more extensively here:
"In the last days of 2000, as we were rewiring the entire agency’s organizational chart (see chapter 2), we set up an enterprise called TAO, Tailored Access Operations, in the newly formed SIGINT Directorate (SID). We had toyed with some boutique end-point efforts before, but this was different. This was going to be industrial strength...And, even in a period of generalized growth, TAO became the fastest-growing part of NSA post-9/11, bar none."
Seeing as General Hayden was in charge of NSA at the time, that would seem to make it clear that TaoSecurity preceded TAO by several months, at least.
I also looked for details in the 2016 book Dark Territory: The Secret History of Cyber War by Fred Kaplan. I've enjoyed several of his previous books, and he interviewed and cited me for the text.
Mr. Kaplan explained how General Michael Hayden, NSA director from March 1999 to April 2005, named the unit, as part of a general reorganization effort. Thanks to Cryptome and FOIA requests by Inside Defense we can read the October 1999 report recommending organizational changes. That reorganization was the genesis for creating TAO.
Kaplan on Creating TAO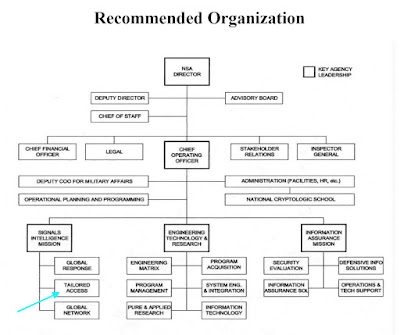 |
| External Team Report Recommended Organization, 22 October 1999, Cryptome |
This document, titled EXTERNAL TEAM REPORT: A Management Review for the Director, NSA, October 22, 1999 mentions the need to reorganize the "Signals Intelligence Mission (SIM)" into "three offices, Global Response, Tailored Access and Global Network." The October 2000 public news story by Inside Defense about the reorganization implies that it did not happen overnight.
Mr. Kaplan notes that General Hayden initiated his "One Hundred Days of Change" program on 15 November 1999. A three-day server crash in January 2000 hampered reform efforts, prompting big changes in NSA approaches to computing. However, TAO was eventually operating some time in 2000. Mr. Kaplan notes the following in his book:
"It began, even under his expansion, as a small outfit: a few dozen computer programmers who had to pass an absurdly difficult exam to get in. The organization soon grew into an elite corps as secretive and walled off from the rest of the NSA as the NSA was from the rest of the defense establishment. Located in a separate wing of Fort Meade, it was the subject of whispered rumors, but little solid knowledge, even among those with otherwise high security clearances...
Early on, TAO hacked into computers in fairly simple ways: phishing for passwords (one such program tried out every word in the dictionary, along with variations and numbers, in a fraction of a second) or sending emails with alluring attachments, which would download malware when opened.
Once, some analysts from the Pentagon’s Joint Task Force-Computer Network Operations were invited to Fort Meade for a look at TAO’s bag of tricks. The analysts laughed: this wasn’t much different from the software they’d seen at the latest DEF CON Hacking Conference; some of it seemed to be repackaged versions of the same software. Gradually, though, the TAO teams sharpened their skills and their arsenal."
It's clear from this passage that TAO started as a small unit that conducted less exotic operations. It was difficult to join, but a far cry from the powerhouse it would soon become. It's also clear that knowledge of this organization was tightly controlled. Even the term "tailored access" was not associated publicly with NSA until the October 2000 reporting by Inside Defense, reproduced by Cryptome.
Minihan's Role
 |
| Dark Territory by Fred Kaplan |
Circling back to the mention of 1997 in Mr. Aid's article, we do find the following in Mr. Kaplan's reporting:
"Fort Meade’s would be the third box on the new SIGINT organizational chart—“tailored access.”
[Lt Gen Kenneth] Minihan [NSA director 1996-1999] had coined the phrase. During his tenure as director, he pooled a couple dozen of the most creative SIGINT operators into their own corner on the main floor and gave them that mission. What CIA black-bag operatives had long been doing in the physical world, the tailored access crew would now do in cyberspace, sometimes in tandem with the black-baggers, if the latter were needed—as they had been in Belgrade—to install some device on a crucial piece of hardware.
The setup transformed the concept of signals intelligence, the NSA’s stock in trade. SIGINT had long been defined as passively collecting stray electrons in the ether; now, it would also involve actively breaking and entering into digital machines and networks.
Minihan had wanted to expand the tailored access shop into an A Group of the digital era, but he ran out of time. When Hayden launched his reorganization, he took the baton and turned it into a distinct, elite organization—the Office of Tailored Access Operations, or TAO."
This reporting indicates that there was a tailored access group operating at NSA prior to General Hayden, but it was not actually named "TAO" and was not as large or exotic as what was to come.
Conclusion
 |
| "Tao inside," TAO's play on the Intel Inside marketing campaign |
To summarize, General Hayden assigned the name TAO to a group inside NSA in late 2000, months after I registered the TaoSecurity domain name. Although General Minihan had created a tailored access group during his tenure, the existence of that team, as well as what was later formally called TAO, was a close-held secret. The term "tailored access" did not appear in the public until Inside Defense's reporting of October 2000.
Although I worked in the unit (Air Intelligence Agency) that served as the cryptologic service group for NSA (the Air Force contribution to the agency), I was not aware of any tailored access teams when I chose TaoSecurity as the name for my repository of security ideas. I selected TaoSecurity to reflect my interest in Taoism, and it had nothing to do with TAO or the NSA.
https://taosecurity.blogspot.com/2021/04/the-origins-of-names-taosecurity-and.html
Published: 2021 04 01 18:00:00
Received: 2021 06 06 09:05:05
Feed: TaoSecurity
Source: TaoSecurity
Category: Cyber Security
Topic: Cyber Security
Views: 10

