Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.5 Tips to be an awesome CISO
published on 2021-11-22 21:35:22 UTC by j4vv4dContent:
I’m not a CISO, I never have been and hope I never will be. It seems like a lot of hard work and stress, and if you’re the CISO at a company when you suffer a breach it’s difficult to blame the intern without a mob of security professionals criticising you.
But I do observe CISO’s very closely, and as a result I have figured out how to be an awesome CISO.
Now, before you object, hear me out. David Attenborough isn’t a whale, or a penguin, or a hippo. But he’s observed these animals in the wild for many years and so when his soothing vocals accompany a nature documentary, you sit there and listen to his every word. He is an expert on all forms of animals without having been an animal himself.
Similarly, you can think of me as the David Attenborough of cyber security – observing CISOs in their natural habitat.
Risk Appetite
Make everything about risk appetite. The beauty of this is that you can always shift the responsibility to the business whenever there’s a tough decision to be made. A third party playing hardball but you don’t want to be the bad CISO in case you miss out on the golf day they have every year. Simply say it’s not within the company’s risk appetite and glance over at the business owner.
When in doubt scribble a diagram on the whiteboard to show how they are outside of the organisations risk appetite.
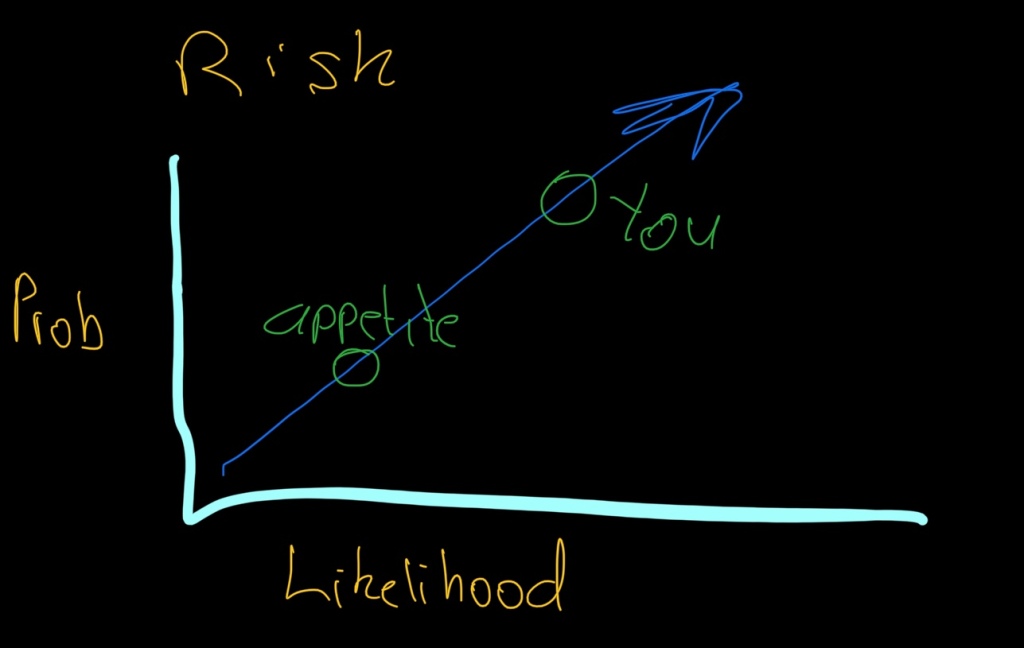
Amber all the way
While metrics underpin information, the board has the attention span of a 3 year old. They only want to see pretty charts and graphs upon which they will consider for 90 seconds before making their investment decisions worth millions.
This is where the traffic light system comes into play. Red, Amber, or Green (RAG). You want to represent your controls and security posture in the most accurate way possible in one visual chart.
Maybe you want more money so you’ll be tempted to show the department as being red. Big mistake, as that will be interpreted as you being incompetent, and will be asked why are they paying you so much money just to have the department in the red.
Overplay your hand and say that everything is green and not only will you not get any more budget, but if a breach does happen, you’ll be publicly flogged for lying that everything was green.
Therefore, your traffic light should always remain a steady amber. You still need money, and if something bad does happen on your watch… you did warn them.

Gluttony
Some will say gluttony is a sin. But not if you’re a CISO. Of course we’re talking about data here. Ingest all the logs, put something to capture data on every endpoint, every router, switch, and firewall. Ingest it into one on-prem SIEM from where you can send data to your cloud-based SIEM, and a smaller subset to your expensive SIEM that charges you per MB.
Acquire all the threat intelligence you can, 5 sources should be the minimum. Subscribe to analyst reports, and call in trusted advisors every 3 months for a planning session.
That way, whenever anyone asks you a question. Especially if they’re an auditor – you can point them to the logs and say, “it’s in there somewhere” wink at them and walk away. It’s always better to have more data, even if it’s a messy mountain in which you can’t find anything, than not enough data.
Just don’t tell your records management person about it. They’re difficult people to deal with.

Confidentiality
If captain America worked in cybersecurity, his shield would be confidentiality. Go to conferences and talk about all the amazing things you’re doing, big yourself up because your next employer could be sitting in the audience.
Use enough technical jargon to make it appear as if you know what you’re talking about, but avoid buzzwords.
Give enough details that it appears as if you’re working on something only the likes of Elon Musk could compete with. But when pushed for details, apologise and say that it is confidential. Of course, you can use other words such as things being proprietary, top secret, only available on a need to know basis.
Joke about how your lawyer is in the room and thinks you’ve already disclosed too much. This will divert peoples attention into trying to spot the lawyer. Which isn’t as much fun as spot the fed.

The 5 year strategy
Good things come to those who wait. Your cyber security strategy to turn your mountains of data into a digital Mona Lisa won’t happen overnight. Your traffic lights will turn green, but it will take time, money, and patience.
Of course the 5 year plan will likely get to 7 years before being scrapped as being a pipe dream. But that doesn’t matter, because in 2.3 years you’ll be a CISO elsewhere telling people how your new project is super awesome, but it’s on a need to know basis.

*I don’t know if it’s actually David or Richard Attenborough who does the nature programmes. Either way, you know who I mean.
https://javvadmalik.com/2021/11/22/5-tips-to-be-an-awesome-ciso/
Published: 2021 11 22 21:35:22
Received: 2021 11 22 23:04:12
Feed: J4vv4D
Source: J4vv4D
Category: Cyber Security
Topic: Cyber Security
Views: 20
