Welcome to our
Cyber Security News Aggregator
.Cyber Tzar
provide acyber security risk management
platform; including automated penetration tests and risk assesments culminating in a "cyber risk score" out of 1,000, just like a credit score.Kubernetes: open etcd
published on 2019-01-06 14:00:00 UTC by UnknownContent:
Quick post on Kubernetes and open etcd (port 2379)
"etcd is a distributed key-value store. In fact, etcd is the primary datastore of Kubernetes; storing and replicating all Kubernetes cluster state. As a critical component of a Kubernetes cluster having a reliable automated approach to its configuration and management is imperative."
-from: https://coreos.com/blog/introducing-the-etcd-operator.html
What this means in english is that etcd stores the current state of the Kubernetes cluster usually including the kubernetes tokens and passwords. If you check out the following references you can get a sense for the pain level that could potentially be involved. At minimum you can get network info or running pods and at best credentials.
refs:
https://techbeacon.com/hackers-guide-kubernetes-security
https://elweb.co/the-security-footgun-in-etcd/
https://raesene.github.io/blog/2017/05/01/Kubernetes-Security-etcd/
the second link talks extensively around types of info the found when they hit all the shodan endpoints for 2379 and did some analysis on the results.
If you manage to find open etcd the easiest way to check for creds is to just do a curl request for:
GET http://ip_address:2379/v2/keys/?recursive=true
Example Loot -
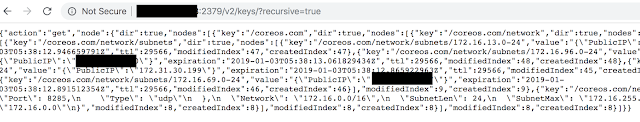
Usually it's boring stuff like this:
But occasionally you'll get more interesting things like:
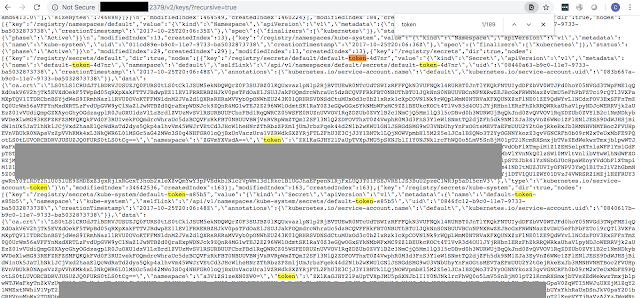
or more fun things like kublet tokens:
"etcd is a distributed key-value store. In fact, etcd is the primary datastore of Kubernetes; storing and replicating all Kubernetes cluster state. As a critical component of a Kubernetes cluster having a reliable automated approach to its configuration and management is imperative."
-from: https://coreos.com/blog/introducing-the-etcd-operator.html
What this means in english is that etcd stores the current state of the Kubernetes cluster usually including the kubernetes tokens and passwords. If you check out the following references you can get a sense for the pain level that could potentially be involved. At minimum you can get network info or running pods and at best credentials.
refs:
https://techbeacon.com/hackers-guide-kubernetes-security
https://elweb.co/the-security-footgun-in-etcd/
https://raesene.github.io/blog/2017/05/01/Kubernetes-Security-etcd/
the second link talks extensively around types of info the found when they hit all the shodan endpoints for 2379 and did some analysis on the results.
If you manage to find open etcd the easiest way to check for creds is to just do a curl request for:
GET http://ip_address:2379/v2/keys/?recursive=true
Example Loot -
Usually it's boring stuff like this:
But occasionally you'll get more interesting things like:
or more fun things like kublet tokens:
https://blog.carnal0wnage.com/2019/01/kubernetes-open-etcd.html
Published: 2019 01 06 14:00:00
Received: 2021 06 06 09:05:30
Feed: Carnal0wnage and Attack Research Blog
Source: Carnal0wnage and Attack Research Blog
Category: News
Topic: Hacking
Views: 31